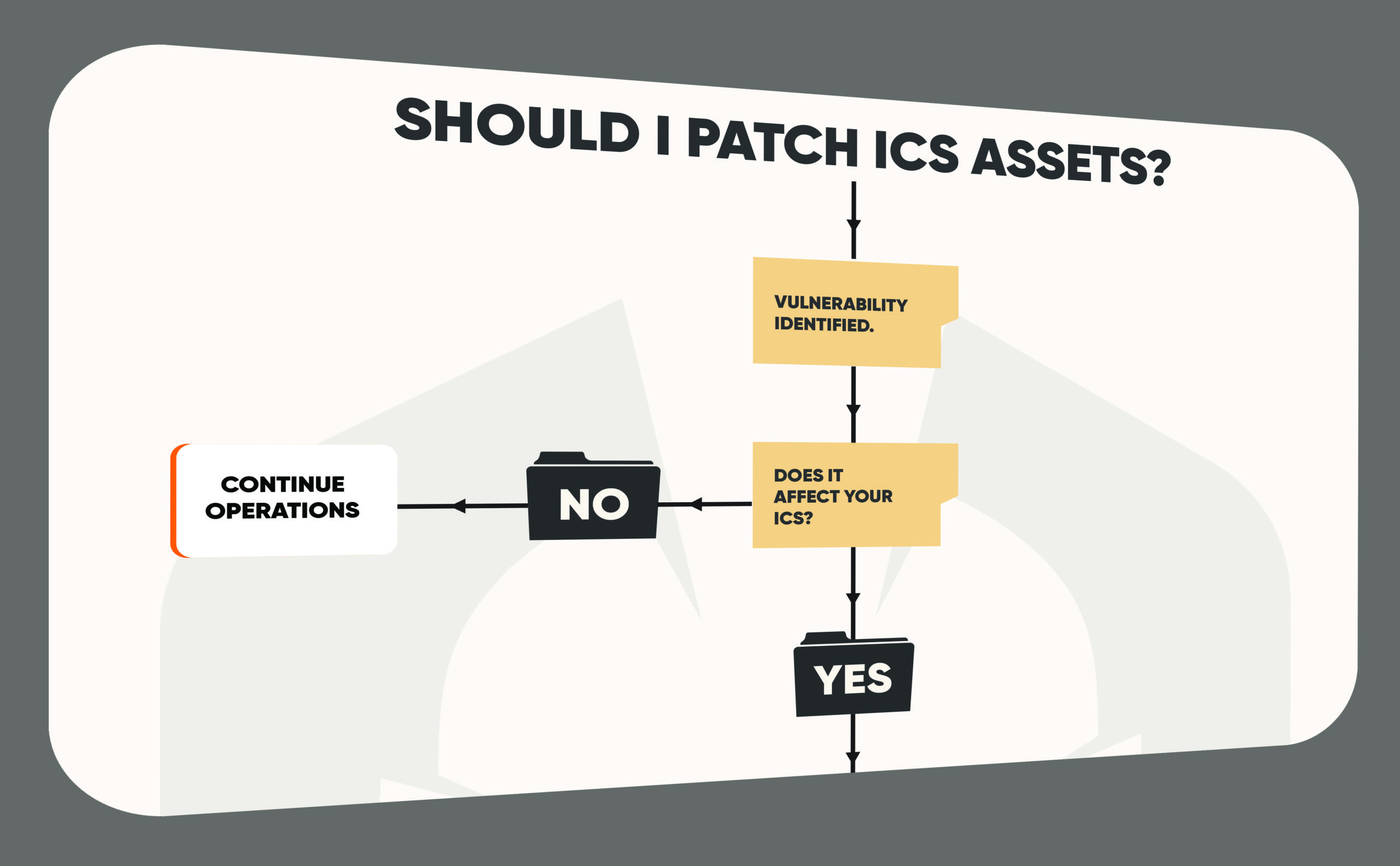
When Should We Patch ICS Assets?
The decision to patch ICS assets is a topic of significant debate in the cybersecurity community. Unlike IT systems, where patching is generally encouraged to address vulnerabilities, ICS environments often prioritize stability and availability, leading to differing views on whether patching should be immediate or even necessary in every case. Many experts argue that patching…
View details