React Less. Defend More.
OT RISK ASSESSMENT
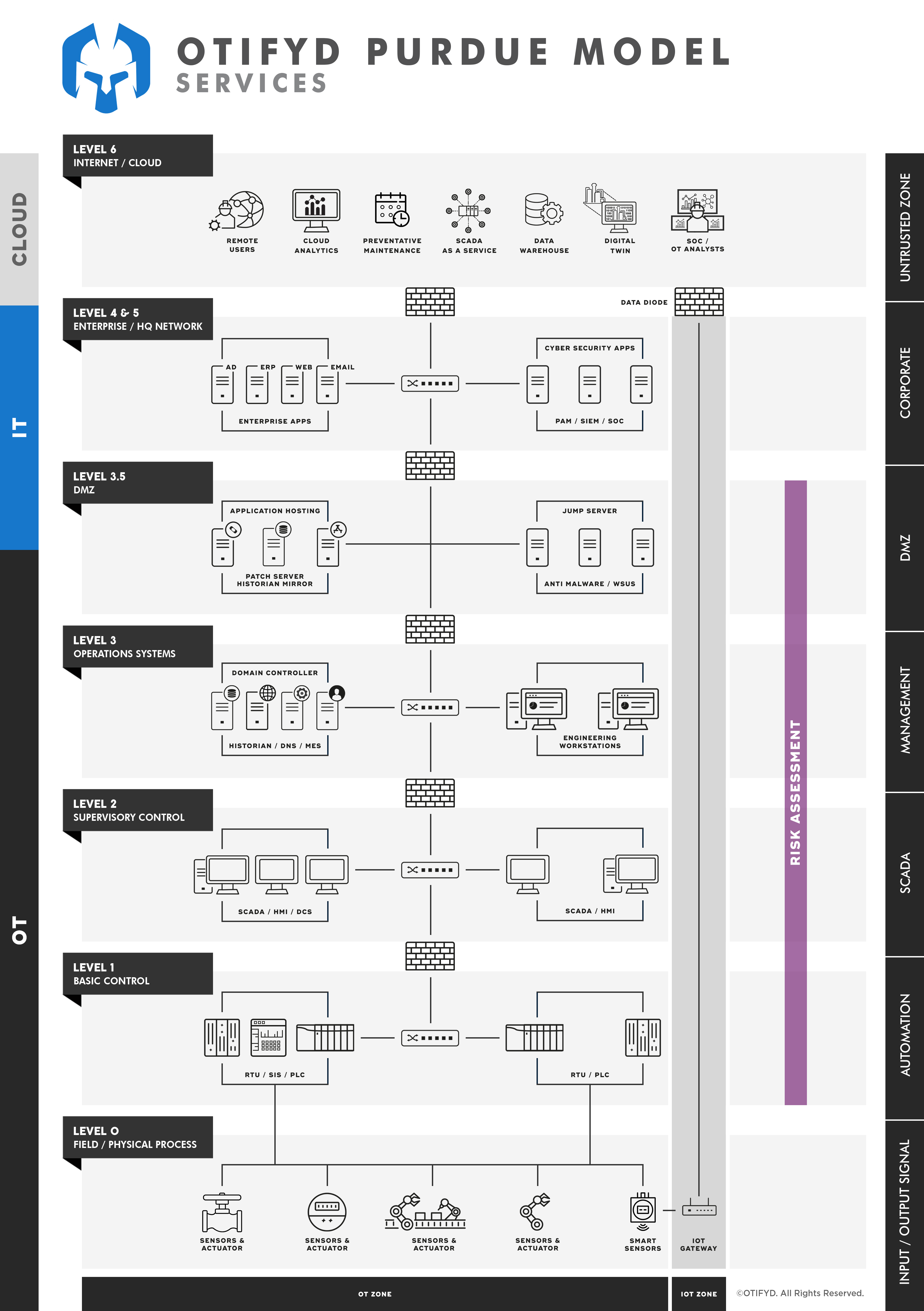
Gain an accurate understanding of your risk exposure and determine controls to effectively reduce it.
OT Risk Assessment Services
Operational Technology (OT) systems are the backbone of modern industry, responsible for controlling and monitoring critical processes. However, these systems are increasingly being targeted by cyber criminals, leading to an urgent need for OT risk management to identify and mitigate potential vulnerabilities. This is achieved through risk assessment processes.
OTIFYD offers comprehensive IEC 62443 compliance risk assessment services that accurately identify cyber security risks for your OT environment. Our risk assessment services include:
- Identification of assets that makeup the OT environment under consideration;
- Identification and partitioning identified assets into security zones and conduits;
- Business Impact Assessment (BIA) to determine critical OT assets;
- Identification and analysis of threat sources/actors and applicable scenarios;
- Identification and evaluation of current (as-is) controls;
- Identification and evaluation of gaps and vulnerabilities;
- Identification and evaluation of additional mitigating controls;
- Risk rating, prioritisation and remedial recommendations;
- Formalised assessment report.
Our assessments are “outcome-focused” which means any remedial recommendations proposed are aimed at providing tangible risk reduction. This approach helps organisations justify OT cyber security improvements and the associated costs by being armed with better information and understanding of the “What, Why and How?”
Finally, our assessments are conducted according to industry best practices and standards/frameworks such as ISO/IEC 62443, ISO/IEC 27001, NIST and ISF but can also be tailored to your specific needs
Why Conduct an OT Risk Assessment?
At a high level, a “cyber” risk assessment builds a structured understanding of risks in your OT environment, and the potential impact they could have on your organisation if realised through both malicious and non-malicious means.
The assessment process is outcome-focused and derives a “risk rating” per worst-case threat scenario (also referred to as “Top-Event”, or “Boom Event”). The assessment considers each threat scenario under each of the following situations:
- No mitigating controls (inherent risk rating);
- With current (as-is) mitigating controls (residual risk rating);
- With additional mitigating controls (target risk rating).
Through detailed discovery and analysis, an informed evaluation is made to determine the effectiveness of existing controls for each threat scenario. The evaluation may determine that existing controls sufficiently reduce the risk to an acceptable level or that the risk presented is acceptable and requires no additional controls or action. Conversely, it may highlight vulnerabilities (i.e. gaps) where enhancements or additional controls are required to bring the risk into organisational tolerance.
The assessment process also factors in “risk vs benefits vs cost and complexity” which enables the pragmatic prioritisation of remedial efforts. This in turn allows the correct focus on items that provide the most risk reduction both tactically (short-term mitigations commonly referred to as “low-hanging fruit”) and strategically (medium to long-term mitigations that require more effort to plan, design and implement).
Risk Ratings are commonly derived using a 5 x 5 grid format known as a “Risk Assessment Matrix” (RAM). The RAM provides a simple and effective way to present a holistic view of the cyber risks for all team members and key stakeholders. “Risk Tolerance” is the degree of risk or uncertainty that is acceptable to an organisation and varies greatly across industries. Many organisations derive their own RAMs that are tuned against applicable consequence categories and likelihood scales based on historical occurrences.
A high-level summary of key steps that make up our risk assessment process is described and visualised below:
01: Discover: Identify Assets
Identify and catalogue all assets that make up the OT environment under consideration. Categories OT assets based on criticality to the organisation’s business operations (e.g. High, Medium & Low).
02: Discover: Identify Threats
Identify and prioritise threat scenarios that result in high-consequence events for the organisation. Consider all applicable real-world cyber scenarios seen across industries for completeness.
03: Analyse: Threats & Controls
Conduct an evaluation of existing (as-is) controls’ effectiveness for each threat scenario. Agree on risk rating for each threat scenario based on organisational impact and likelihood.
04: Analyse: Additional Controls
Consider which additional controls can provide tangible risk reduction for each threat scenario. The controls must be realistic. Agree on an updated risk rating possible with additional remedial controls.
05: Analyse: Prioritise Risk
Prioritise risks determining which warrants immediate action, where to invest time and resources, and which risks can be addressed later. Prioritisation is based on the highest risk rating in descending order.
06: Formalise: Create Report
Assessment documented within a formal report. The report includes an executive summary, description of the current situation, risk exposure to the organisation, findings, observations and recommendations.
07: Formalise: Readback
A high-level feedback session to provide a general overview of the assessment outcome to executive-level stakeholders, plan next steps and conclude the engagement.

Why is an OT Specific Risk Assessment Necessary?
Traditional IT information security models prioritise Confidentiality, then Integrity and lastly Availability (commonly known as the “CIA Triad”), whereas OT cyber security models prioritise Availability, then Integrity and lastly Confidentiality (commonly known as the “AIC Triad”).
This is because the assets and systems that make up an OT environment (e.g. manufacturing plant, upstream oil asset etc) rely heavily on being available and their integrity dependable for both process control and safeguarding. In some cases, the loss of availability or system integrity could jeopardise the safety of the workforce, consumers, physical assets and the environment. Depending on the type and length of availability loss, this can result in economic, ecological, and life-threatening situations. Examples of availability attacks include the 2021 Colonial Pipeline attack, the 2019 Springhill Memorial Hospital ransomware attack, and the 2015 Sandworm attacks on Ukrainian critical infrastructure.
These differences between OT vs IT environments should be considered to correctly assess risks and propose appropriate countermeasures, hence why an OT-specific risk assessment is necessary.
Key Benefits of Conducting an OT Risk Assessment
- Understand and benchmark your current risk exposure and the potential consequences of cyber attacks.
- Identifies gaps covering People, Processes and Technology which aids prioritise high-risk areas for remediation and improvement.
- Provides supporting information to make informed decisions in relation to cyber security investment.
- Provides compliance evidence of cyber risk management to regulatory authorities.
Deliverables from an OT Risk Assessment
As part of this service offering, OTIFYD delivers a formalised report that includes:
- Assessment methodology;
- Executive summary;
- Description of the current situation, risk exposure and potential consequences to the organisation;
- Assessment findings and observations;
- Remediation recommendations with associated priorities.
Additionally, the following items will also be provided:
- High-level presentation for executive-level stakeholders;
- Any supporting materials produced during the assessment (e.g. risk assessment analysis worksheets etc).
What is OT Cyber Security?
OT Cyber Security refers to the specific practices and processes used to protect the Operational Technology (OT) systems that control industrial processes from cyber threats.
OT Cyber Security is critical for ensuring the safety and reliability of industrial processes, and involves the implementation of measures such as access control, network segmentation, encryption, and intrusion detection to name but a few.
What is OT Risk Management?
OT Risk Management involves the identification, assessment, and management of risks associated with Operational Technology (OT) systems. The goal of OT risk management is to ensure the safety and reliability of industrial processes by implementing appropriate security controls to manage the risks associated with cyber threats.
What is OT Risk Assessment?
OT Risk Assessment is the process of identifying potential risks to Operational Technology (OT) systems, assessing the likelihood and impact of those risks, and developing strategies for managing the risks. The process involves identifying vulnerabilities in the system, assessing the likelihood and impact of an attack, and developing strategies for managing the risks.
What are the Differences Between IT and OT Security?
One major constraint for industrial companies towards protecting industrial systems is a misunderstanding of the difference between IT and OT security. Here’s a rather simplistic way to think about it.
IT stores, retrieves, and transmits data whereas OT uses that data to monitor, control, and operate physical devices, processes, and events. In IT, the confidentiality of data is a key concern whereas in OT the safety of equipment and availability of processes is the main concern.
IT is dynamic, that it has many moving parts and it means that IT has an incredible number of exploit variants. Hence, IT incidents are more frequent. By contrast, OT has a lower number of gateways, making it comparatively safer. OT is engineered for prescribed actions based on content which means things only happen one way. If given a certain input, OT always produces a specific output again and again.
Another difference between IT and OT security concerns security patching. Since IT components progress so fast and have relatively short life spans, IT security updates happen frequently which doesn’t work the same way in OT. In fact, patching OT components can require complete shutdowns and are rarely updated. It is true that many OT systems are “insecure by design” and would be at risk from a sophisticated attacker even after vulnerability patching.
The differences outlined above make it clear that IT and OT have different security priorities and different goals for the maintenance of their systems. 80% of organisations surveyed see the expanding interconnectedness of OT and IT as a challenge. This is a result of the digitalisation of OT which can expose industrial systems that might not be properly secured to cyber threats.
Why does OT Cyber Security Matter?
As a society, we all depend on operational technology for a wide range of critical industrial processes. The growing costs of industrial machinery and the serious devastation that an attack could deliver for the economy are crucial factors to consider for organisations that want to boost the protection of their industrial networks.
Considering the increasing cybersecurity risk exposure, OT systems have become a more lucrative target. This interest is noticeable in the growing availability of exploit kits and new monetisation opportunities such as ransomware particularly developed to hack industrial systems.
What are the Three (3) Main OT Cyber Security Attack Vectors?
Network attack surface: it presents exposure related to ports, protocols, channels, services, network applications and firmware interfaces. Depending on the organisation’s infrastructure, cloud servers and data could also be included.
Software attack surface: its surface is comprised of the software environment and its interfaces. The software attack surface is calculated across a number of different types of code, such as applications, email services, configurations, databases, executables, web pages, mobile device OS, etc.
Human attack surface: one of the important strengths of highly secure organisations is their emphasis on delivering security awareness and safety principles to their employees, partners, supply chain and even their customers.
Why do Organisations Need OT Cyber Security Assessment in the First Place?
Assessing OT security risks will yield a number of benefits. Firstly, it will give a thorough understanding of various OT devices and their functionality. Secondly, this assessment will help the organisation discover threats to its OT environment and prioritise remediation efforts using a consequence-led approach.
What OT Cybersecurity Risk Assessment Methodologies are Commonly Used?
Detailed below are some Risk Assessment methodologies used for OT:
NIST Risk Management Framework (RMF): The NIST RMF is a framework that provides guidelines for managing the risks associated with information security. The framework is structured into six steps that include categorizing information and information systems, selecting and implementing security controls, assessing security control effectiveness, authorising information systems, monitoring security controls, and responding to security incidents.
ISA/IEC 62443: A series of standards that provide guidelines for the security of industrial automation and control systems. The standards include a methodology for conducting a security risk assessment that involves defining the scope of the assessment, identifying the assets and threats, analyzing the risks, and implementing the appropriate security controls.
FAIR: The Factor Analysis of Information Risk (FAIR) methodology is a quantitative risk analysis framework that provides a structured approach to identifying, analysing, and prioritising risks. The methodology involves identifying and quantifying the assets, threats, vulnerabilities, and impacts, and then calculating the risk by applying a set of standard formulas.
OCTAVE: Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) is a methodology that provides a structured approach to risk assessment and management. The methodology involves identifying the assets, threats, vulnerabilities, and impacts, and then developing a risk management plan to mitigate the identified risks.
STRIDE: STRIDE is a methodology used to identify and prioritise the security threats to a system. The methodology involves analysing the system for potential threats and then prioritising the risks based on their likelihood and impact.
The OT risk assessment methodology should be tailored to the specific requirements and risks of the organisation. The methodology should be flexible enough to incorporate the organisation’s unique requirements and should be periodically reviewed and updated to reflect changes in the threat landscape.
In addition to the above-mentioned methodologies, the use of automated risk assessment tools is becoming increasingly popular. Automated tools can help organisations to quickly identify vulnerabilities and risks and provide prioritised recommendations for remediation.
Some of the commonly used automated risk assessment tools (risk assessment technology) in the OT environment include Nozomi Networks, Claroty, Armis, Tenable Nessus and Rapid7.
Why is OT risk assessment important?
OT risk assessment is important for several reasons. Firstly, it helps organizations identify potential risks and vulnerabilities in their OT infrastructure, which is essential for effective risk management. Secondly, it enables organisations to prioritise their security investments based on the risks that pose the greatest threat to their OT systems. Finally, it helps organisations comply with various regulations and standards that require a comprehensive risk assessment of their OT infrastructure.
What are the key steps involved in conducting an OT risk assessment?
The key steps involved in conducting an OT risk assessment include:
Scoping: Defining the scope of the assessment, including the assets and systems that will be included in the assessment.
Threat identification: Identifying potential threats to the OT infrastructure, such as cyberattacks, natural disasters, and human error.
Vulnerability assessment: Assessing the vulnerabilities and weaknesses in the OT infrastructure that could be exploited by a threat.
Risk analysis: Analysing the likelihood and impact of potential risks to the OT infrastructure.
Risk evaluation: Evaluating the risks based on their likelihood and impact, and determining the appropriate risk management strategies.
Risk treatment: Developing and implementing strategies to mitigate the identified risks.
Monitoring and review: Monitoring the effectiveness of the risk management strategies and reviewing the risk assessment periodically to ensure it remains up-to-date.
What are some common challenges associated with conducting an OT risk assessment?
Some common challenges associated with conducting an OT risk assessment include:
Limited visibility: It can be difficult to identify all OT assets and systems, especially in large and complex environments.
Lack of expertise: Conducting an OT risk assessment requires specialized expertise in both OT and IT security, which can be difficult to find within an organization.
Rapidly evolving threats: The threat landscape for OT systems is constantly evolving, making it difficult to keep up with new and emerging threats.
Limited resources: Conducting an OT risk assessment can be time-consuming and resource-intensive, which can be a challenge for organizations with limited resources.
What are some best practices for conducting an OT risk assessment?
Some best practices for conducting an OT risk assessment include:
Engaging cross-functional teams: Bringing together teams with expertise in both OT and IT security can help ensure a comprehensive risk assessment.
Using automated tools: Automated tools can help identify and track OT assets and vulnerabilities, making the risk assessment process more efficient and accurate.
Prioritising critical assets: Critical assets should be given priority in the risk assessment process, as they pose the greatest risk to the organization.
Regularly reviewing the assessment: The assessment should be reviewed periodically to ensure it remains up-to-date and reflects changes in the OT infrastructure.
Ensuring senior management support: OT risk assessment should be supported by senior management to ensure the necessary resources are allocated and the risk management strategies are effectively implemented.