React Less. Defend More.
SECURE REMOTE
ACCESS FOR OT
Remove the complexity, security risks and administrative barriers to provide effective, efficient secure remote access to industrial environments.
Secure Remote Access
Remote Access allows controlled access for remote maintenance in order to maintain operational efficiency.
Considering the requirements of secure remote access, everyone is looking for a solution that helps simplify daily operations without having to worry about cybersecurity. While there are many pieces of software available designed for remote access they often cater to IT networks and are rarely part of larger, consolidated solutions.
However, OT and IT networks have different characteristics and priorities. While IT prioritises data confidentiality, OT focuses on network availability and zero tolerance for downtime. This difference in approach makes it difficult for OT networks to adopt IT practices. Another hurdle is that many automation engineers are not familiar with VPN technologies or know the necessary configuration for setting up remote access securely.
Secure remote access is important in an operational technology (OT) environment for several reasons:
Improved management: Secure remote access enables administrators to manage and maintain OT systems and devices from a remote location, reducing the need for on-site visits and increasing the efficiency of operations.
Enhanced security: By providing secure remote access to OT systems and devices, organizations can help ensure that only authorized individuals have access to sensitive information and systems. This helps prevent unauthorized access to critical systems and data, and reduces the risk of security incidents.
Increased availability: Secure remote access enables administrators to access and manage OT systems and devices from anywhere, at any time. This increases the availability of systems and devices, and helps ensure that they remain operational even in the event of an on-site failure or outage.
Simplified maintenance: Secure remote access enables administrators to perform maintenance and updates on OT systems and devices from a remote location, reducing the need for on-site visits and increasing the efficiency of operations.
Better monitoring: By providing secure remote access to OT systems and devices, administrators can monitor the performance and status of systems and devices from a remote location, enabling them to respond more quickly to potential issues and improve the overall health of the network.
Security vs. Convenience
For OT engineers, cybersecurity remains the number one concern when it comes to remote access. A solution with flexible access control could fulfil different OT scenarios and enhance network security. balancing the trade-off between security and convenience is an important consideration in the context of secure remote access in an OT environment. The goal is to implement appropriate security measures while also providing convenient and flexible access options for users to help ensure that the OT network remains secure, stable, and operational.
There are several reasons why remote access is important in an industrial network:
- Increased efficiency: By providing remote access to industrial systems and devices, administrators and engineers can manage and maintain systems from a remote location, reducing the need for on-site visits and increasing the efficiency of operations.
- Better monitoring: Remote access enables administrators to monitor the performance and status of industrial systems and devices from a remote location, allowing them to respond more quickly to potential issues and improve the overall health of the network.
- Improved maintenance: Remote access enables administrators to perform maintenance and updates on industrial systems and devices from a remote location, reducing the need for on-site visits and increasing the efficiency of operations.
- Increased availability: By providing remote access to industrial systems and devices, administrators can access and manage systems from anywhere, at any time. This increases the availability of systems and devices, and helps ensure that they remain operational even in the event of an on-site failure or outage.
- Enhanced collaboration: Remote access can enable collaboration between different teams and individuals who may be working on the same industrial systems and devices, improving communication and coordination and helping to ensure that systems and devices remain operational.
For example, customisable access control lets facility owners decide when and for how long third-party engineers can access their network.
Furthermore, access can be restricted to specific network areas. These measures can ensure the safety of their network when opening the door for remote maintenance services. Remote services for OT should also be accessible and easy to use. An ideal solution lets OT engineers easily set up remote access when needed, even if they are not familiar with VPNs or know the public IP.
- Asset Owners
Manufacturers with facilities scattered across multiple locations require expansive networks to sustain operational effectiveness and efficiency. To manage such large and dispersed networks, the network management software installed at the remote sites monitors the local network and sends data back to the HQ control centre through an encrypted tunnel. This gives engineers a complete view of the network from a central location for remotely managing operations at each site. If any incident occurs, engineers at the headquarters can remotely access the on-site network device via a secure VPN connection or call in the help of third-party support services if necessary using an on-demand encrypted VPN tunnel.
- Service Providers/System integrators
To better help their customers manage and maintain their network smoothly, network service providers require a simple solution for responding to service requests from multiple customers and solve issues as quickly as possible. Real-time remote service allows service providers to overcome geographical limitations and streamline their customer service. An on-demand encrypted VPN tunnel can let support engineers easily access the network management software at the customer’s site without jeopardizing the safety of the customer’s network.
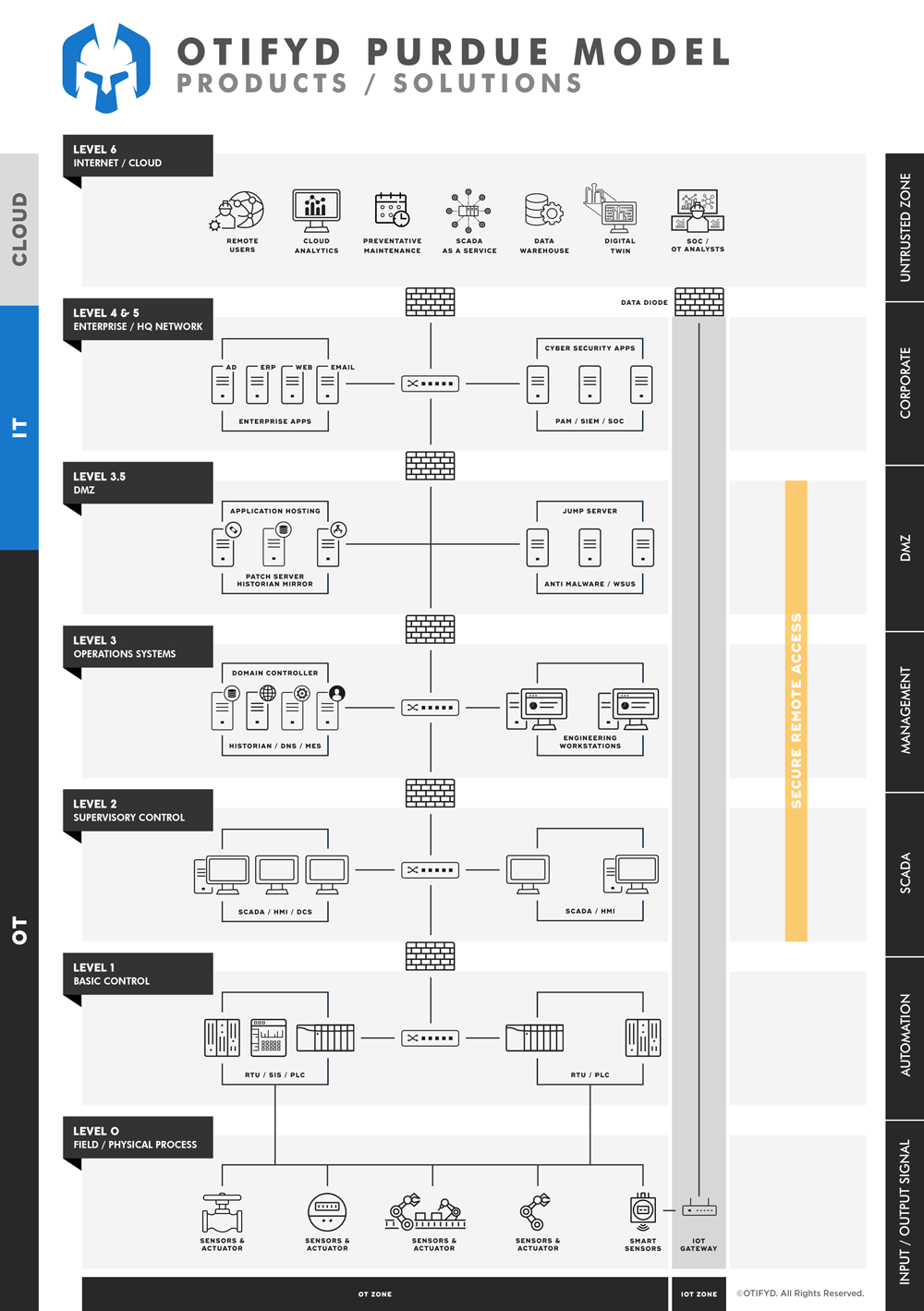
Key Characteristics of OT Secure Remote Access
Most remote access solutions are designed for the IT environment. Modern OT secure remote access solutions are both convenient for users and compliant with IEC 62443 recommended architecture.
Streamlines Access for Internal & Third-Parties
Secure Remote Access should remove the complexity and administrative barriers to effective, efficient remote access to industrial environments for both internal and third-party users.
Extends Zero Trust-based Access Controls
Remote access is the most commonly exploited attack vector for industrial environments. Secure Remote Access should eliminate this with a secure architecture.
Offers Full Auditing & Response Capabilities
Secure Remote Access should support user sessions that enable live, over-the-shoulder monitoring, live disconnects if needed, and full-length recordings to support audit requests and investigations.
Delivers an Ideal UX that Reduces MTTR
Secure Remote Access should include a purpose-built user experience that makes connecting, troubleshooting, and repairing assets fast and easy, no matter where assets or users are located.
What’s Secure Remote Access?
Secure remote access allows authorised and controlled access by remote engineers or users outside of an industrial plant to connect to a network, application or resource using their remote device from the internet or even a corporate network.
Why do we need a Secure Remote Access in our OT environment?
Industrial networks are no longer isolated. The increased connectivity of industrial control systems makes them more exposed to potential cyberattacks. Therefore, it is important to keep the OT network as isolated as possible from the enterprise network, especially from the public internet while still providing access for more productivity and maintenance.
Secure remote access is a crucial part of any organisations, specially during COVID-19 era to allow employees and IT personnel to safely connect to and manage other assets from different locations.
Is Remote Access Safe?
If you don’t have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data and leave you vulnerable.
A solid secure remote access should provide controlled reliable and frictionless access using multiple layers of security and monitoring in place.
Is Remote Access to an OT environment really necessary?
The safest approach for an organisation is to avoid any remote access and if an organisation can survive without providing remote access, then it shouldn’t. However, this often is not the case. Secure remote access ensures that remote users are connecting based on their role and privileges, authenticated and only access the assets they are intended for during the time scheduled while being monitored and recorded.
What are the different methods of Remote Access in OT Environments?
For quite some time, OT environments followed the most common method of secure remote access, VPN still is one of the most common methods used across the industrial network, but certainly not recommended.
It lacks granularity in access level and monitoring features provided by vendors focused on ICS solutions which provide connectivity via a 3rd party server.
Another recent method used in ICS networks is “Moving Target Defence” using one-time cloud network to replace static remote servers.
Why is secure remote access important in OT environment?
Secure remote access is important in OT environment because it allows authorised personnel to remotely access and control the OT devices and systems, which can improve operational efficiency and reduce costs. However, without proper security measures in place, remote access can also create vulnerabilities that could be exploited by cyber attackers, leading to data breaches, system failures, and other consequences that can affect not only the organisation but also public safety and national security.
What are the security challenges of remote access in OT environment?
The security challenges of remote access in OT environment include authentication and authorisation of remote users, encryption of data transmitted over the network, protection of credentials and configuration data, monitoring and logging of remote access activities, and isolation of the OT network from the enterprise network and the internet to prevent unauthorised access.
What are the best practices for secure remote access in OT environment?
The best practices for secure remote access in OT environment include using multi-factor authentication (MFA), enforcing strong password policies, implementing encryption for data in transit and at rest, limiting access privileges to only what is necessary for each user, logging and monitoring remote access activities, regularly updating software and firmware, isolating the OT network from the enterprise network and the internet, and conducting regular security assessments and penetration testing. Additionally, organizations should have an incident response plan in place to quickly respond to and mitigate any security incidents.
