React Less. Defend More.
intrusion & anomaly
detection
Find unknown and malicious activities while avoiding alert storms & false positives. Focus on what matters by monitoring your OT assets to detect anomalous behaviour and misuse in your environment.
Intrusion & Anomaly Detection
As operational technology (OT) becomes more pervasive across critical infrastructure sectors such as energy, manufacturing, mining, and transportation, industrial operations are increasingly at risk of cyber attacks. These attacks can lead to operational disruptions, equipment damage, and even physical harm to workers. As such, ensuring the security of OT systems is a critical priority for industrial organizations.
One of the key strategies for securing OT systems is the use of intrusion detection and anomaly detection technologies. These tools provide real-time visibility into the network and device activity, allowing security teams to detect and respond to threats quickly.
Intrusion detection systems (IDS) monitor network traffic and devices for signs of unauthorized access or malicious activity. They can detect known attack patterns, such as malware infections and unauthorised access attempts. IDS can also be configured to monitor for specific types of activity, such as changes to critical files or system configurations, that may indicate a compromise.
Anomaly detection systems (ADS), on the other hand, use machine learning algorithms to identify patterns of behavior that are outside of the norm. This can include deviations from expected traffic patterns, unusual system or user behavior, or other anomalies that may indicate a threat. ADS can be particularly useful for detecting previously unknown or “zero-day” attacks that may not be detected by traditional signature-based IDS.
The combination of IDS and ADS provides a comprehensive approach to OT security, allowing organizations to detect a wide range of threats in real-time. With improved operational visibility, security teams can respond quickly to security incidents, minimizing the impact of attacks and reducing the risk of damage to critical infrastructure.
As the Internet of Things (IoT) continues to expand, the importance of OT and IoT security solutions will only grow. OT systems are increasingly connected to the internet and other networks, creating new avenues for attack. As such, industrial cybersecurity solutions must evolve to address the unique challenges of securing OT environments.
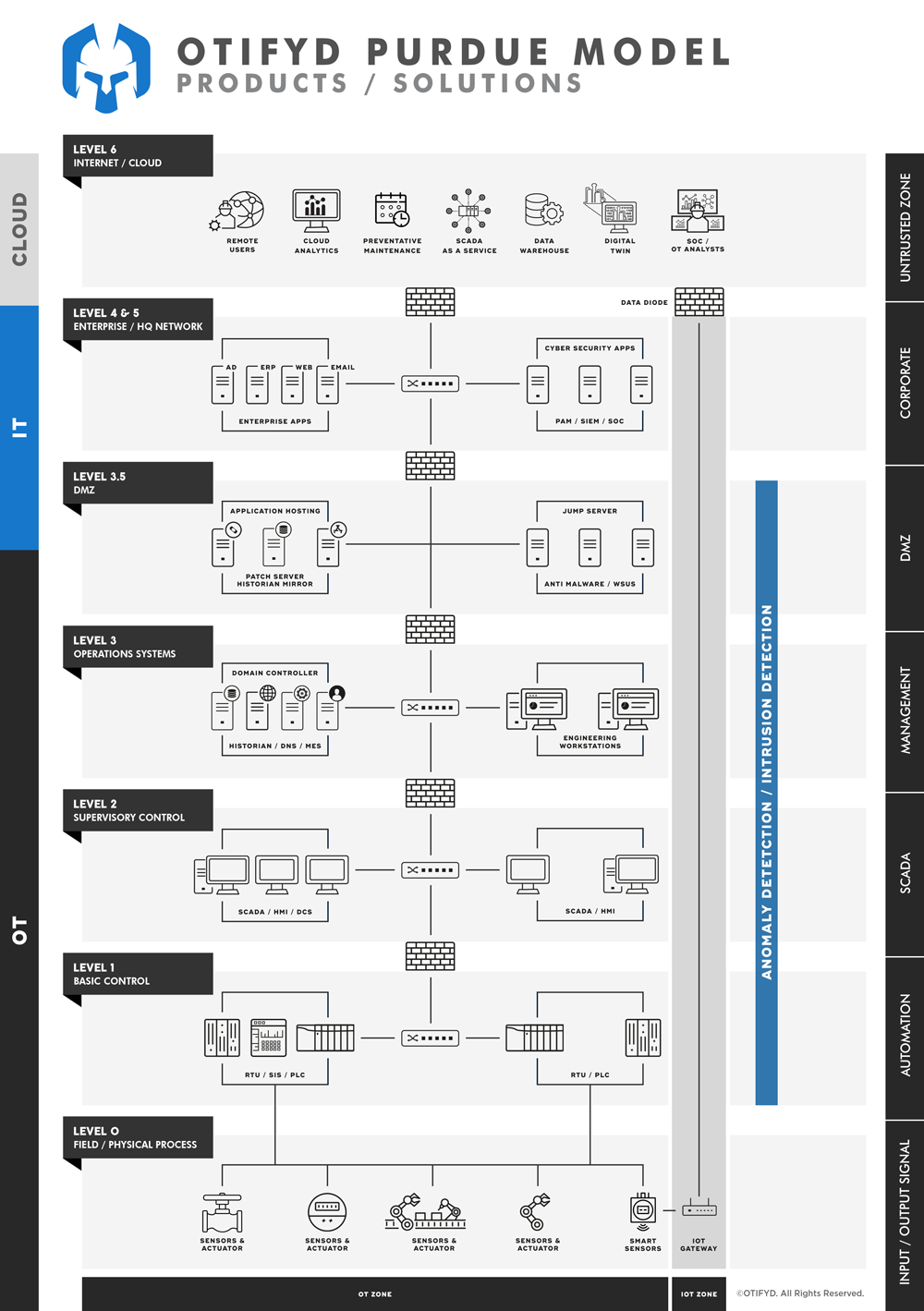
As cyber-attacks evolve, industrial network security requires unparalleled visibility and intelligence covering all threats for comprehensive protection. Effective industrial cybersecurity starts with knowing what needs to be secured. A continuous threat detection solution should be able to offer discovery capabilities to provide comprehensive visibility via a highly detailed, centralised inventory of all OT and IoT as well as IT assets.
With differing organisational responsibilities and agendas, you need a consistent security enforcement mechanism. These increasing operational demands call for a renewed focus on dedicated anomaly and intrusion detection to provide a deeper level of security and visibility for the whole enterprise.
Intrusion and anomaly detection in industrial networks refers to the process of identifying unauthorized access or any unusual behavior that could potentially harm the network or its components. This is important in industrial environments, where network security and stability are critical to the smooth operation of processes and equipment.
The main methods used for intrusion and anomaly detection in industrial networks include:
Signature-based detection: This method uses a database of known threats and compares network traffic to detect any matches.
Anomaly-based detection: This method uses machine learning algorithms to learn the normal behavior of the network and identifies any deviations as anomalies.
Behavior-based detection: This method analyzes the behavior of network devices and users to detect any suspicious activities.
Honeypot-based detection: This method involves setting up a decoy system to lure attackers and gather information about their techniques and tactics.
It’s important to note that no single method is foolproof, so a combination of these methods is often used to provide a more comprehensive security solution. Additionally, continuous monitoring and updating of the system is crucial to keep up with the evolving threat landscape.
Purpose-Built Monitoring for OT Environments
Anomaly detection purpose-built for Operational Technology (OT) environments refers to the use of specialized tools and techniques designed specifically to monitor and detect any unusual or suspicious activities in these environments.
OT environments typically include industrial control systems (ICS) such as Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and Programmable Logic Controllers (PLCs). These systems are often critical to the safe and efficient operation of critical infrastructure such as power plants, water treatment facilities, and manufacturing plants.
Overall, the use of intrusion detection and anomaly detection technologies is a critical component of a comprehensive OT security strategy. By providing real-time visibility into network and device activity, these tools allow organizations to detect and respond to threats quickly, reducing the risk of operational disruptions and physical harm to workers. As industrial operations continue to rely on OT systems, improved cybersecurity solutions will be essential to ensuring the safety and security of critical infrastructure.
An anomaly detection solution automatically compares each asset in your industrial environment to an extensive database of insecure protocols, known configurations, substandard security practices, and other vulnerabilities tracked by its vendor, as well as to the latest CVE data from various National Vulnerability Database sources. As a result, users can more effectively identify, prioritise, and remediate vulnerabilities in industrial networks.
One of the clearest indicators of potentially threatening activity in your industrial environment is communication between an industrial asset and an external malicious IP address. Our portfolio’s Network Policy Management capability makes it easy to alert on such communications and then automatically define and enforce policies to prevent future violations, thereby eliminating this type of attack vector.
Anomaly detection in OT environments requires a unique set of features and capabilities that are different from those required for Information Technology (IT) environments. This includes the ability to:
- Analyze real-time data from a variety of sources, including PLCs, DCS, and other industrial devices.
- Detect anomalies in industrial protocols such as Modbus, DNP3, and Profinet.
- Integrate with other security systems, such as firewalls, intrusion detection systems (IDS), and security information and event management (SIEM) systems.
- Provide actionable alerts and notifications in real-time to ensure rapid response to any potential threats.
Purpose-built anomaly detection solutions for OT environments are essential to ensuring the security and stability of these critical systems. They can help detect potential threats before they can cause harm, allowing organizations to respond quickly and effectively to any security incidents.
Asset Inventory
Creating an accurate OT asset inventory, and keeping it current can be difficult and extremely time-consuming. Not only do industrial networks contain a large number of devices from multiple vendors, but assets can also get added and changed frequently. These complex environments typically contain OT and IoT security vulnerabilities you’re not even aware of.
An accurate, centralised asset inventory is crucial for effective cybersecurity and operational monitoring.
Vulnerability Assessment
Industrial networks contain thousands of OT and IoT devices from a variety of vendors. Unfortunately, most of those devices aren’t designed for the level of security required in an IIoT-connected world. Many ICS devices are in fact insecure by design – lacking authentication, encryption, and other security standards that typically apply to IT applications and systems. This leaves you wondering – which devices on your network are vulnerable and in need of special protection and which ones require firmware updates or other actions to close the door on cyber risks.
Risk Assessment
Risk Assessment should be your first step to securing your OT environment. Risk assessment can identify risks and enable OT security stakeholders to understand the current security baseline. Acknowledging the current status of the plant is fundamental and is the starting point of your security journey.
Risks come from many different directions and categories, so a risk assessment that only focuses on high-level business processes might fail to identify risks due to flaws in technical implementations. Insufficiently defined security leadership/governance in the boardroom is a risk, but so is a poorly configured firewall. Therefore, it is essential to have a scope that is sufficiently broad and incorporates different parts of the organisation. Furthermore, a combination of a paper review with an onsite, technical assessment are vital components for a comprehensive risk assessment.
What is the ICS intrusion detection system?
Intrusion detection systems (IDS) a monitoring system that detects malicious attacks or suspicious activities and generates alerts when they are detected.
An ICS intrusion detection system typically consists of a combination of hardware and software components that work together to monitor network traffic, detect anomalies and suspicious activity, and provide real-time alerts to security personnel. The system may use various techniques such as signature-based detection, behavioural analysis, and traffic analysis to identify and isolate malicious activity, and may also include capabilities for incident response, forensic analysis, and reporting.
Can we use IT Intrusion Detection System in OT environment?
OT environments typically have different requirements and constraints compared to IT environments, such as real-time control and monitoring of critical infrastructure, the need for high availability and reliability, and the use of specialised hardware and software. As a result, IT IDS systems may not be fully optimised or suitable for use in an OT environment, and may require modifications or customisation to meet the specific needs of the industrial control system.
Additionally, IT IDS systems may not be designed to detect the types of threats that are specific to OT environments, such as control system protocols, or have the ability to process large amounts of real-time data. Therefore, it may be necessary to supplement the use of IT IDS with specialised OT security tools, such as ICS (Industrial Control System) intrusion detection systems, to provide a more comprehensive security solution for the industrial control system.
What’s the difference between IDS (intrusion detection system) and IPS (intrusion prevention system)?
Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) are both security systems used to protect computer networks and systems from unauthorized access and cyber attacks. However, they differ in their primary functions and the way they respond to security incidents.
An IDS monitors network traffic and alerts security personnel when it detects suspicious or malicious activity, but does not take any action to block or prevent the attack. The primary function of an IDS is to detect potential security threats, provide real-time alerts to security personnel, and enable incident response and forensic analysis.
An IPS, on the other hand, goes one step further by not only detecting but also blocking security threats in real-time. An IPS uses various techniques such as signature-based detection, behavioUral analysis, and traffic analysis to identify and isolate malicious activity, and then takes action to block the attack, such as dropping packets, resetting connections, or triggering an alarm.
What’s the difference between Intrusion Detection and Anomaly Detection Systems?
Intrusion Detection Systems (IDS) and Anomaly Detection Systems (ADS) are both used to detect potential security threats in computer networks and systems. However, they differ in the way they identify security incidents.
Intrusion Detection Systems use signature-based detection and/or behavioral analysis to identify known security threats. These systems compare incoming network traffic to a database of known attack signatures, and alert security personnel when a match is found.
Anomaly Detection Systems, on the other hand, work by monitoring network traffic and identifying deviations from normal behaviour patterns. These systems use statistical analysis and machine learning algorithms to create a profile of normal network behaviour, and then alert security personnel when the network traffic deviates from this normal behaviour.
Is IPS (Intrusion Prevention System) used in OT environment?
While Intrusion Prevention Systems (IPS) can be used to secure industrial control systems in an OT (Operational Technology) environment, their use is generally not recommended for several reasons:
Interference with normal operations: An IPS system may block network traffic that is necessary for normal control system operations. This can interfere with real-time control and monitoring of critical infrastructure, and could cause harm to equipment or processes if the IPS system blocks the wrong traffic.
Latency: Industrial control systems require low latency and high availability, and an IPS system can introduce additional latency in the network, which could affect the performance of real-time control and monitoring applications.
Complexity: An IPS system can be complex to configure and manage, particularly in an OT environment where specialized hardware and software are used. This complexity can increase the risk of misconfigurations that can cause harm to the industrial control system.
Lack of interoperability: Industrial control systems use specialised protocols and communication methods, and not all IPS systems are capable of processing and analysing these types of traffic.
Can Intrusion Detection Systems block traffic?
Yes, some Intrusion Detection Systems (IDS) have the capability to block network traffic in response to a detected security threat. These systems are sometimes referred to as Intrusion Prevention Systems (IPS), and they combine the detection capabilities of an IDS with the ability to take action to prevent the attack from succeeding.
In general, IDS systems are designed to detect security threats and alert security personnel, while IPS systems are designed to detect and prevent security threats. When an IPS detects a security threat, it can take a number of actions to prevent the attack, such as blocking malicious traffic, resetting connections, or triggering an alarm.
However, it’s important to note that not all IDS systems have the capability to block traffic. Some IDS systems are designed to only detect security threats and alert security personnel, and do not have the ability to take any action to prevent the attack.
Why do we need Intrusion Detection Systems?
Intrusion Detection Systems (IDS) are an important component of a comprehensive security strategy for protecting computer networks and systems from unauthorized access and cyber attacks. There are several reasons why organizations need IDS:
Early detection: IDS can help detect security threats early in the attack cycle, providing organizations with an early warning of an attack and enabling a rapid response to prevent further damage.
Continuous monitoring: IDS can monitor network traffic 24/7, providing organizations with continuous visibility into their networks and systems, and enabling them to detect security threats in real-time.
Compliance: In some industries, regulatory compliance mandates the use of security measures such as IDS to protect sensitive information. An IDS can help organizations meet these compliance requirements by providing evidence of the security measures in place to protect their systems.
Protection against evolving threats: Cyber threats are constantly evolving, and organizations need to have up-to-date security measures in place to protect against these threats. IDS can help organizations stay ahead of the curve by detecting new and emerging threats and providing early warning of potential attacks.
Can Intrusion Detection Systems detect malware?
Yes, Intrusion Detection Systems (IDS) can detect malware in computer networks and systems. There are two main methods for detecting malware using IDS: signature-based detection and behavioral analysis.
Signature-based detection involves comparing incoming network traffic to a database of known malware signatures. When a match is found, the IDS alerts security personnel to the presence of malware. This method is effective for detecting well-known malware, but may not detect new or emerging malware threats.
Behavioural analysis involves monitoring the behaviour of network traffic and identifying anomalies that may indicate the presence of malware. For example, an IDS may detect an unusual increase in network traffic, or an unusual pattern of communication between two systems, that could indicate the presence of malware. Behavioural analysis is effective for detecting new and emerging malware threats, but can also result in a higher number of false positive alerts.
Can Intrusion Detection Systems detect spyware?
Yes, Intrusion Detection Systems (IDS) can detect spyware in computer networks and systems. Spyware is a type of malicious software that is designed to covertly gather information from a computer system without the user’s knowledge or consent.
IDS can detect spyware in several ways, including:
Signature-based detection: IDS can compare incoming network traffic to a database of known spyware signatures. When a match is found, the IDS alerts security personnel to the presence of spyware.
Behavioral analysis: IDS can monitor the behavior of network traffic and identify anomalies that may indicate the presence of spyware. For example, an IDS may detect an unusual increase in network traffic, or an unusual pattern of communication between two systems, that could indicate the presence of spyware.
Heuristics-based detection: IDS can use heuristics to identify potentially malicious activity that may indicate the presence of spyware. Heuristics-based detection involves analyzing the behavior of software to identify potential threats.
