React Less. Defend More.
ot, iot, XIOT & ics cyber security solutions
Gain visibility and control over your Operational Technology (OT) and build comprehensive cyber security defence capabilities.
Best of Breed OT & IoT Solutions
So you have already assessed your Operational Technology (OT) security posture and identified your risks. You may have already identified all your OT assets, including the connectivity associated with them, and now need to build a defensible network. Whether you’ve used our consultancy services or not, we can sit and work with your team to conduct an architectural review in order to determine your existing capabilities and give you a comprehensive, step-by-step roadmap to secure your OT environment.
Whether you’re building your industrial DMZ, creating security zones and conduits, or migrating to a zero-trust micro-segmentation strategy, OTIFYD has you covered.
As the world becomes increasingly interconnected, the need for robust security in critical infrastructure and industrial control systems (ICS) has become more pressing. Industrial cybersecurity is a field dedicated to protecting these systems from cyber threats, and it involves a range of security tools and practices.
One important concept in industrial cybersecurity is the “single pane of glass,” which refers to a unified interface for managing security across all devices and systems. This approach enables security teams to gain real-time visibility into their network and respond quickly to any security incidents.
OT devices, or operational technology devices, are a key component of industrial networks, and they require specialized security measures. Unlike traditional network devices, which are primarily designed for communication, OT devices are responsible for controlling physical processes, such as machinery and industrial equipment. This means that any security breach in an OT device can have serious real-world consequences.
To protect these devices and the larger industrial network, a range of security tools are employed, including firewalls, intrusion detection systems, and antivirus software. However, it is not enough to simply implement these tools and hope for the best – ongoing monitoring and proactive threat hunting are essential for maintaining a secure industrial network.
The rise of IoT devices has added another layer of complexity to industrial cybersecurity. These devices, which are often small and easy to deploy, can create new entry points for attackers. Industrial networks must carefully manage IoT devices to ensure they are properly secured and monitored.
Comprehensive Product Range
Clients often ask us about the best industrial firewall or the best OT intrusion detection system, or what should be the first security technology to deploy in our network. Unfortunately, the simple answer is, there is no “one size fits all” solution.
Our approach for products and services recommended are based on the following key factors:
- Client’s security maturity level;
- Client’s industry;
- Client’s resources, both budget and human resources.
Based on the above information, we create a bespoke roadmap which clearly marks the extent of the offered security, its shortcomings and the level of risk our clients would be taking.
For security professionals, the term “best-of-breed” is used often to describe the latest and greatest technologies. Obviously, we partner with leading OT and IoT security vendors, with which we have worked for a number of years and we are confident about their performance.
Our value-add comes from identifying which products suit your needs best, resulting in tangible OT cyber security advancement.
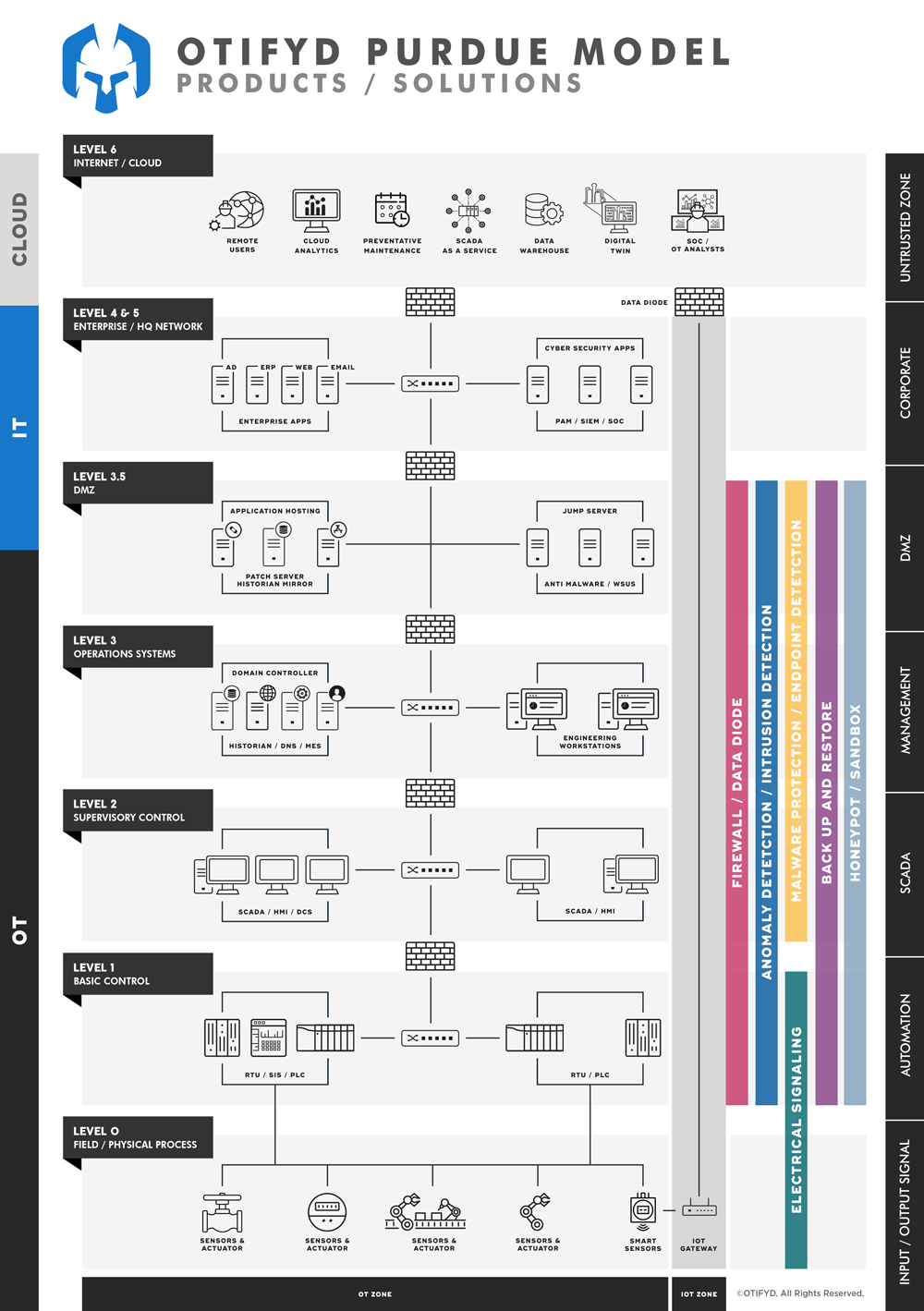
ICS Firewall / OT Firewall
Firewalls are a ubiquitous part of Information Technology (IT) and Information Security (InfoSec), especially in situations where only one security measure is chosen.
Firewalls secure systems and data by monitoring and controlling the flow of traffic in, out and between networks using defined firewall rules (also known as policies) that filters traffic appropriately. This is true for both enterprise IT and industrial OT firewalls, which are normally used within OT/ICS environments.
Intrusion & Anomaly Detection and Prevention
Anomaly Detection is an innovative method for IT and OT security.
Unlike common security solutions, anomaly detection is not limited to detecting known threats or working along a generalised “allow-list”. The primary aim of this solution is to detect any anomaly in a network. An anomaly can be defined as any change in the specific established standard communication of a network. An anomaly may include both malware and cyberattacks, as well as faulty data packets and communication changes caused by network problems, capacity bottlenecks, or equipment failures.
Thus, anomaly detection enables holistic malfunction prevention, secures productivity and guarantees complete digital transparency.
End Point Security / Malware Protection
OT Endpoint Protection is a necessity to protect the world’s OT infrastructure, but in many cases, it is not deployed due to several key challenges.
Endpoint protection is a foundational element in every industrial/OT cybersecurity strategy. Despite the known limitations, most industrial companies still use anti-malware and anti virus software wherever possible in their OT environments. Some also use application “allow-listing” solutions to further protect assets.
Automation vendors are likewise applying these security products as part of their standard reference architectures. Endpoint protection solutions used in industrial/OT systems are generally the same as those used for corporate IT. However, there are constraints on the products that are applicable for use in industrial control systems because users have unique challenges in maintaining malware signatures, etc. These differences impact the features industrial users want and the value they place on the new developments occurring in the endpoint protection market.
Unidirectional Gateway / Data Diode
Unidirectional gateways are a combination of hardware and software, generally an appliance that allows data to travel in only a single direction, also known as data diode or diode firewall.
OT/Industrial Control Systems typically benefit from data diodes where secure historian replication is required, emulating protocol servers and devices (e.g. data feed to a simulator or digital twin) or simply for unidirectional file sharing.
Although sometimes referred to as a unidirectional firewall, technically they are not a firewall, they do not route traffic and they do not replace firewalls.
Active Defense with Honeypots and Decoys
Active defence remains one of the most accurate methods to detect the presence of adversaries and malicious activities in your network.
The honeypot serves as a decoy, distracting cybercriminals from actual targets. It can also serve as a reconnaissance tool, using their intrusion attempts to assess the adversary’s techniques, capabilities and sophistication.
Modern deception defences use breadcrumbs as lures as decoys to make deception deterministic and more effective. Knowing attackers desire access credentials and information to learn and expand within an environment, these elements make perfect lures or bait leading to decoys or honeypots.
Security defences make too much noise, however, deception defences are pretty quiet in comparison to well-known security defences.
When it comes to internal blue teams being tested by external red teams for security preparedness, deception defences prove their value quickly for blue teams.
OT Sandbox
Sandboxing helps run a safe, isolated environment to test code, analyse files, updates and patches for malware and compatibility. Industrial sandbox confines a file/program/script to a test environment, preventing it from infecting or harming the host device or operating system.
As the name implies, this confined test environment functions as something like a “sandbox,” in which you can experiment with various variables to see how the system works or behaves. It is also a secure environment where anything that goes wrong cannot directly hurt your host machines or production environment.
Some of the benefits of OT sandbox are:
- Preventing zero-day attacks;
- Minimise risk;
- Update and patch assets in a safe environment before enabling them in the operational network.
Secure Remote Access
OT remote access allows users to access the hardware and software that controls industrial equipment without being on-premises. Whether they’re working from home or at another location within the company, remote access enables employees to adjust processes, update software, troubleshoot problems or perform other tasks necessary to maintaining business operations.
When defined in broad strokes, it’s a simple concept. But in practice, it is a complex undertaking that introduces risks to the enterprise via OT systems—many of which lack cybersecurity protections.
In today’s threat landscape, remote access is (or should be) inseparable from secure remote access.
