React Less. Defend More.
OT Cyber Security Program
Address, reduce and sustain risk reduction across your OT environment.
OT Cyber Security Program Overview
No matter the size of an organisation, every organisation that depends on Operational Technology (OT) to conduct any part of its business should have a functioning OT Cyber Security Program.
Over recent years, digital transformation, IT/OT convergence and increased connectivity have become prevalent within OT environments. However, many organisations have failed to recognise the extent of their OT risk exposure this evolution brings. An organisation’s OT cyber risk exposure may be as simple as a small number of OT assets performing a manufacturing batch operation or as complex as a multi-network, multi-OT system, geographically dispersed and supported by cloud solutions. In either case, OT cyber security begins with protecting safety, availability and integrity and extends through all the layers of infrastructure supporting its use. OT Cyber Security Programs are setup to address reduce and sustain risk reduction through these layers.
Programs are expected to evolve as the threat landscape changes and are usually the product of initial exploration and analysis activities to understand an organisations risk exposure, vulnerabilities and deficiencies across People, Process and Technology.
Why Run an OT Cyber Security Program?
OT Cyber Security Programs are currently front and centre for many executive teams, all with the desire to achieve a multitude of key program objectives.
From a risk reduction standpoint, OT Cyber Security Programs are vital to removing or reducing the inherent vulnerabilities that an organisation may face, offering more protection against human, reputational or financial losses incurred from a successful cyber security incident or unsatisfactory audits.
Executive boards are also looking to the OT Cyber Security Programs to ensure that compliance and regulatory requirements are met, critical business operations are preserved and shielded from potential service disruptions, and the organisation’s risk exposure is established and mitigated to as low as reasonable practicable.
For these broader goals to be achieved, executive boards will often look for their OT Cyber Security Program to establish a standardised security framework for the entire organisation, one that includes the operating models and assurance processes that will be followed across the entire OT estate.
The OT Cyber Security Program must also establish robust, secure OT system and network architectures that not only support the current organisational needs and operations but also support and enable future business strategies or operations as the organisation adapts to changing market conditions.
OT Cyber Security Programs are formed upon the bedrock of a People – Process – Technology approach that balances an organisation’s overall risk against mitigating control requirements, business strategies or future plans, current business needs, and investment capital available for security purchases.
From an organisational perspective, the creation of a clearly defined OT Cyber Security Program is critical to ensuring the right balance of selected and defined security controls, while also providing sufficient investment to deploy and sustain them. All of this must be executed within specified time and budget parameters (decided upon within the organisation) to achieve tangible performance and return-on-security-investment metrics. For many organisations, that remains easier said than done; however, building an understanding of the key steps involved in the planning, implementation, execution, and long-term sustainment of an OT Cyber Security Program can begin to move these initiatives to fruition in an organisation.
Key Benefits of an OT Cyber Security Program
- Flexible Engagement Scope: We support full program lifecycle or specific parts like program development, deployment, monitoring assurance and improvement processes;
- Working in Collaboration: We ensure your program is designed practically and the people, procedural and technical requirements are achievable;
- Increased Risk Reduction and Cyber Security Maturity: A program will reduce risk exposure and increase maturity through all stages of the OT Risk Management Lifecycle;
- Meet Compliance and Business Objectives: Enables an organisation to meet regulatory requirements or strategic business objectives to proactively manage cyber security risk.
Deliverables from our OT Cyber Security Program Service
The deliverables of our OT Cyber Security Program Service typically include:
Risk Assessment Report: A comprehensive report that identifies and assesses the risks and vulnerabilities associated with the OT environment. This report provides the basis for the development of the security controls and processes.
Security Policy and Procedures: A set of policies and procedures that outline the security controls and processes to be implemented to protect the OT environment from cyber threats. This includes access controls, monitoring, incident response, and disaster recovery.
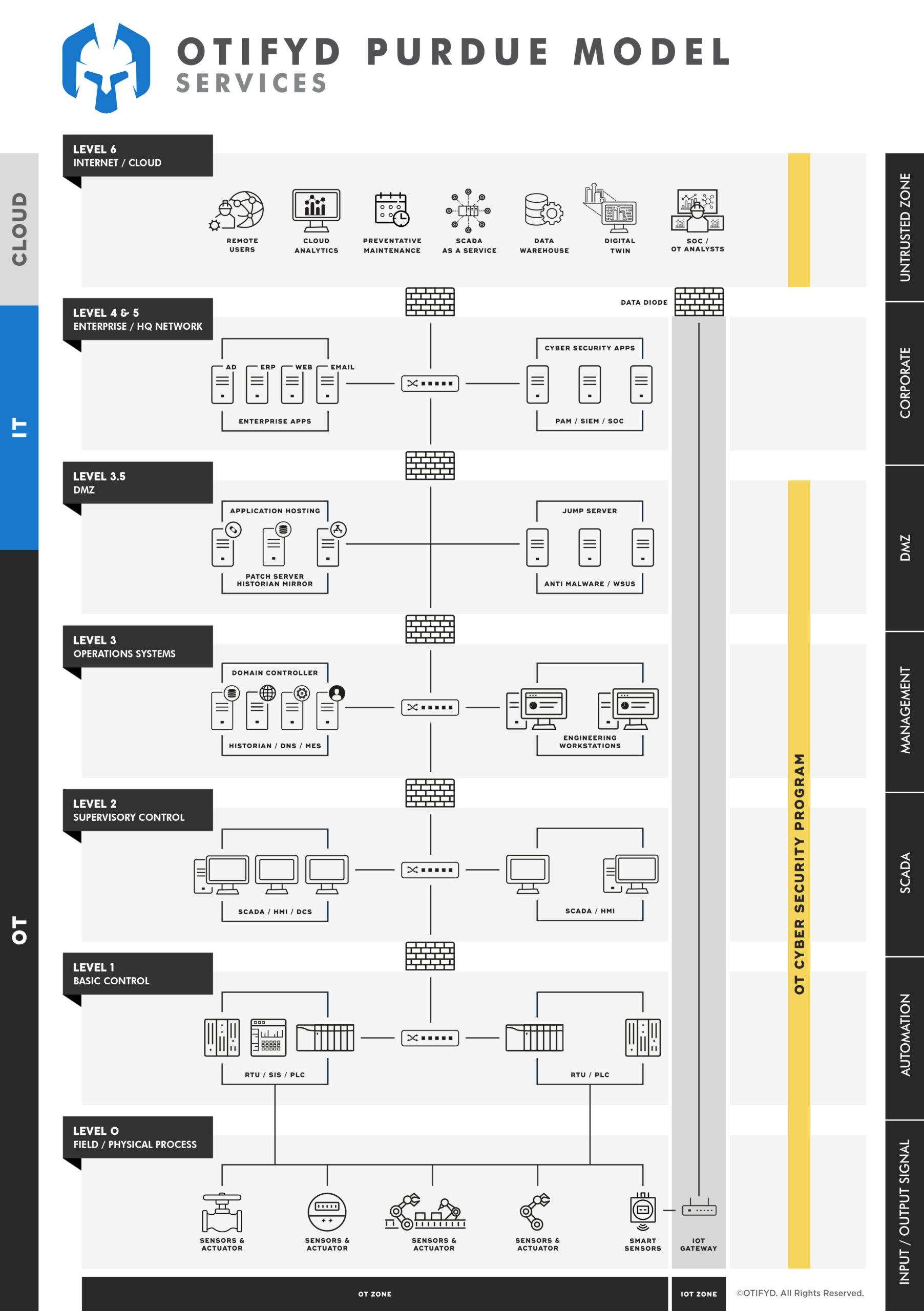
Network Architecture Diagrams: Diagrams that illustrate the network architecture of the OT environment, including the various devices and systems that are connected and how they interact.
Security Control Implementation Plan: A plan that outlines the steps to be taken to implement the security controls and processes outlined in the security policy and procedures.
Security Awareness Training: Training materials and programs designed to educate employees and contractors on the importance of cyber security and the role they play in protecting the OT environment.
Incident Response Plan: A plan that outlines the steps to be taken in the event of a security incident or breach, including how to detect, contain, and mitigate the impact of the incident.
Testing and Validation Plan: A plan that outlines the steps to be taken to test and validate the security controls and processes implemented in the OT environment, including penetration testing, vulnerability scanning, and security audits.
Overall, the deliverables of an OT Cyber Security Program are designed to establish a comprehensive security framework that protects critical infrastructure from cyber threats, while ensuring the availability, reliability, and safety of the systems and processes they control.
This service offering is tailored to your organisation’s specific needs. Get in touch to discuss further.
What is the Main Differences Between IT and OT Security Programs?
One significant difference between OT cybersecurity programs and their IT cybersecurity counterparts is that OT security programs have a cross-organisational impact. OT security programs often include stakeholders from across the organisation all of whom will want to have some say in the program guidelines, goals, and structure.
What is the Foundation of OT Security Programs?
OT Security Programs are formed upon the bedrock of a People – Process – Technology approach that balances an organisation’s overall risk against mitigating control requirements, business strategies or future plans, current business needs, and investment capital available for security purchases. From an organisational perspective, the creation of a clearly defined OT security program is critical to ensuring the right balance of selected and defined security controls, while also providing sufficient investment to deploy and sustain them.
What is a Cyber Security Program?
A cyber security program is a set of activities, security policies, and security controls that are designed to prevent a successful cyber attack against an organisation and recover from them quickly and completely.
Can you Measure the Performance of a Cyber Security Program?
OT Cyber Security Program performance can be managed but only if measured. Companies that have agreed-upon security performance metrics are more likely to manage security effectively.
Cyber security performance management is the process of evaluating your cybersecurity program’s maturity based on risks and the associated level of investment (people, process, and technology) needed to improve your security to meet regulatory requirements and business outcomes. The metrics should tell a story about your security program: how prepared you are for an attack, the attacks that have been discovered and resolved, the vulnerabilities that made those incidents possible, and steps being taken to close the holes in the security program.
Why is Developing A Cyber Security Program Important?
In a nutshell – cybercrime is becoming increasingly prevalent, persistent, and costly.
The consequences of cyber-attacks in OT environments include production downtime, safety and environmental impacts, tarnished brand reputation, and potentially large regulatory fines or lawsuits.
How Should Cyber Security Investment be Considered?
Return on Investment (ROI) is an important metric used by decision makers to calculate the value of an investment. It’s difficult to calculate the return on a security investment because they generally generate no positive return.
However, considering the veracity of today’s cyber-threat environment, businesses that implement cyber security programs are likely to benefit from costs prevented. So, instead of a traditional ROI calculation, the Return on Security Investment (ROSI) equation should be used, which incorporates the savings of security events avoided.
ROSI = (Security expense avoided – prevention cost) / prevention cost
By realistically calculating the benefit of avoided costs, investment in a cyber security program can be more clearly justified and an organisation can reap the rewards of being prepared to weather the storm of a cyber breach.