React Less. Defend More.
Next-gen ot
firewall
Best-of-breed next-generation threat protection firewalls for industrial environments, providing visibility, control, and automated real-time analytics detection.
Industrial Firewall
Across different industrial verticals, organisations are experiencing sweeping technological changes. As the shift towards Digital Transformation (DX) and Industry 4.0 accelerates, the need to rethink security while designing networks grows only stronger.
While many businesses plan proactively for such disruptions and embrace such changes strategically, there will always be times when they get taken by surprise. The sudden and forceful wave of DX, increased demand for providing remote access and the immanent threat of ransomware have made OT Firewalls a must-have security item in every CISO’s shopping list.
An industrial firewall is a specialised firewall device designed for use in industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems protecting all sort of OT devices. Unlike traditional IT firewalls, industrial firewalls are designed to protect against specific security threats that are unique to industrial environments, such as cyber attacks on critical infrastructure. They are built to withstand harsh industrial conditions, such as extreme temperatures, vibrations, and electromagnetic interference.
Industrial firewalls typically provide network security functions such as stateful inspection, intrusion detection and prevention, virtual private network (VPN) support, access controls and application layer filtering. They are also designed to integrate with other security measures, such as intrusion detection systems and security information and event management (SIEM) solutions, to provide a comprehensive security solution for industrial networks.
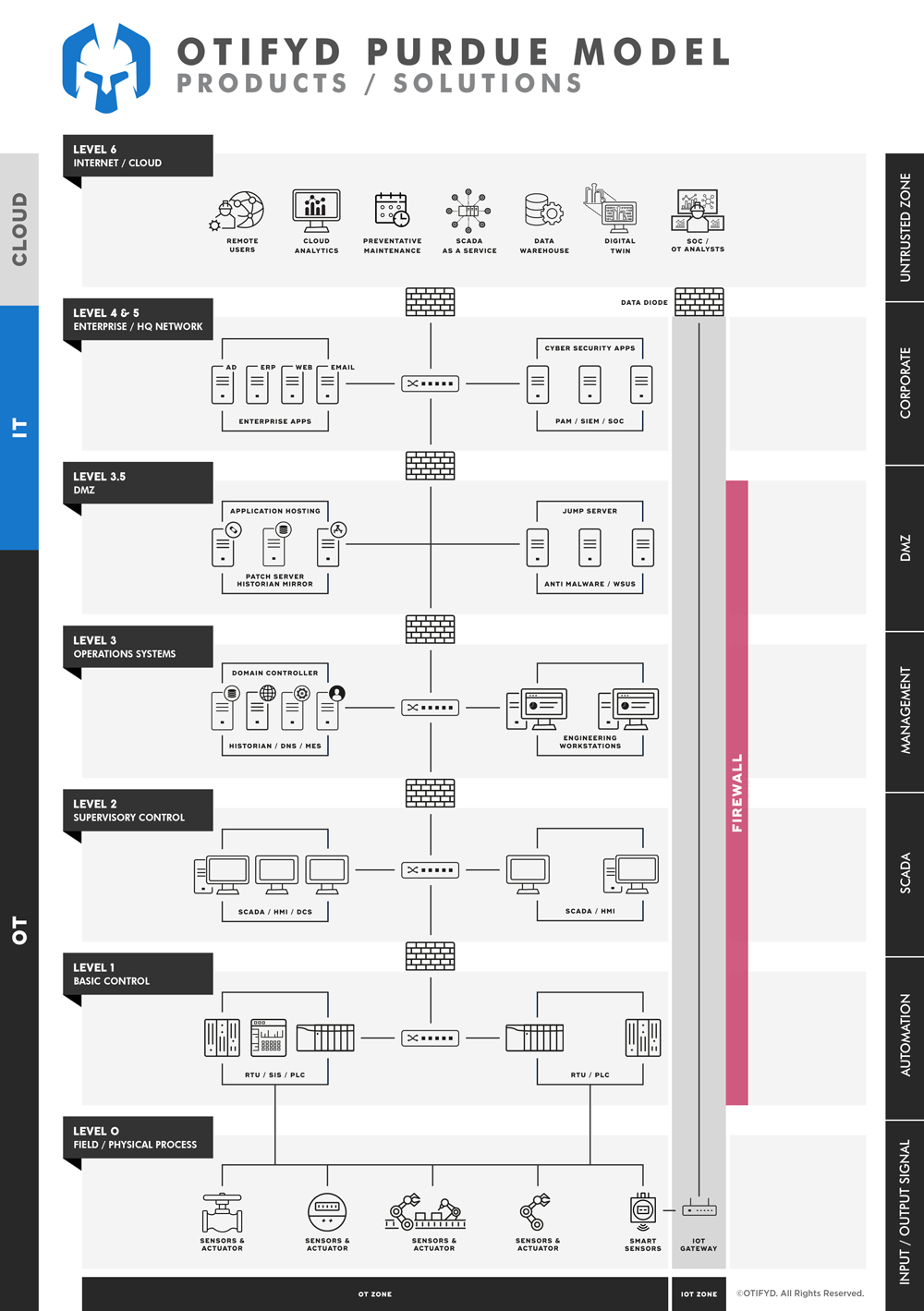
Operational Technology (OT) firewalls and Information Technology (IT) firewalls are two different types of firewalls designed to meet the specific security needs of their respective industrial network and OT environments, IT and OT convergence in particular and in some instances, industrial internet of things IIoT and XIoT or Extended Internet of things.
IT firewalls are designed to protect IT networks, such as enterprise networks and data centers, from various types of cyber threats, such as malware, unauthorised access, and network intrusions. They are typically deployed at the perimeter of an IT network and use traditional security measures, such as stateful inspection, intrusion detection, and application-layer filtering, to secure the network.
OT firewalls, on the other hand, are specifically designed for use in operational technology systems, industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems. They protect these systems from cyber threats that can compromise the control and operation of critical infrastructure, such as power plants, water treatment facilities, and manufacturing plants. OT firewalls provide security functions similar to IT firewalls, but are built to withstand harsh industrial conditions and are optimized for low latency and real-time communication requirements.
In summary, the main difference between OT firewalls and IT firewalls lies in their design and the environments they are intended to protect. OT firewalls are designed specifically for industrial control systems, while IT firewalls are designed for general IT networks.
OT Firewalls vs IT Firewalls
Similar to IT network firewalls, Industrial Firewalls protect networks and network devices, such as industrial PCs, control systems and other associated devices from unauthorised access by restricting traffic to, from and between networks.
Industrial firewalls use many of the same capabilities as IT firewalls but are designed to be used in different ways. The industrial firewall’s main purpose is to ensure that OT assets are protected by only allowing the necessary connectivity to ensure the high availability and uptime requirements of such devices and systems.
Next-Generation Firewalls, available as physical or virtual appliances, provide boundary protection between the IT and the OT network and micro-segmentation among product lines and departments on the shop floor.
With granular visibility into industrial protocols and commands, these firewalls provide access control throughout the OT environments.
Operational Technology (OT) firewalls and Information Technology (IT) firewalls are two different types of firewalls designed to meet the specific security needs of their respective environments.
IT firewalls are designed to protect IT networks, such as enterprise networks and data centers, from various types of cyber threats, such as malware, unauthorized access, and network intrusions. They are typically deployed at the perimeter of an IT network and use traditional security measures, such as stateful inspection, intrusion detection, and application-layer filtering, to secure the network.
OT firewalls, on the other hand, are specifically designed for use in industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems. They protect these systems from cyber threats that can compromise the control and operation of critical infrastructure, such as power plants, water treatment facilities, and manufacturing plants. OT firewalls provide security functions similar to IT firewalls, but are built to withstand harsh industrial conditions and are optimized for low latency and real-time communication requirements.
The main difference between OT firewalls and IT firewalls lies in their design and the environments they are intended to protect. OT firewalls are designed specifically for industrial control systems, while IT firewalls are designed for general IT networks.
Any Next-Gen industrial firewalls should be able to provide the features detailed below:
OT Asset Discovery and Visibility
OT firewalls and OT asset discovery and visibility are two important components of a comprehensive security strategy for industrial control systems (ICS) and operational technology (OT) networks.
An OT firewall is a security device designed to protect industrial control systems and OT networks against cyber threats. It acts as a barrier between the ICS/OT network and other networks, such as the Internet, and monitors and controls the flow of traffic between these networks.
OT asset discovery and visibility refers to the process of identifying and tracking the assets connected to an ICS/OT network. This information is used to gain a complete understanding of the network topology and the devices and systems that are connected to it.
Together, OT firewalls and OT asset discovery and visibility provide organizations with a comprehensive view of their ICS/OT network and its security posture, enabling them to detect and respond to security incidents in a timely manner.
Auto-Generated Policy Recommendations
Auto-generated policy recommendations refer to a feature of some OT firewalls that automatically suggest and generate security policies based on network traffic and behaviour analysis. These recommendations are designed to help organizations quickly and easily deploy and maintain a secure network environment.
The benefits of auto-generated policy recommendations include:
Improved security: By automatically generating security policies based on network traffic and behaviour analysis, auto-generated policy recommendations help organizations ensure that their networks are protected against known and unknown threats.
Increased efficiency: Auto-generated policy recommendations save time and reduce manual effort by automating the process of generating security policies, reducing the risk of errors and inconsistencies.
Enhanced flexibility: Auto-generated policy recommendations can be easily customised and adjusted to meet the specific needs and requirements of an organisation.
Reduced complexity: Auto-generated policy recommendations simplify the process of deploying and maintaining a secure network environment, making it easier for organizations to manage their security policies and ensure compliance with industry and regulatory standards.
Auto-generated policy recommendations are a valuable tool for organizations looking to enhance the security of their industrial control systems and OT networks, providing a fast and efficient way to deploy and maintain a secure environment.
Virtual Patching
Virtual patching is the process of developing and deploying a temporary strategy to limit the risks of exploitation, a security feature that can be implemented in an OT firewall to provide protection against vulnerabilities in industrial control systems and operational technology (OT) networks. Virtual patching works by using software to simulate the effects of a patch or security update without actually applying the patch to the system.
The benefits of virtual patching include:
Rapid protection: Virtual patching provides rapid protection against vulnerabilities in industrial control systems and OT networks, without requiring a system shutdown or restart.
Improved security: Virtual patching helps reduce the risk of cyber-physical attacks and industrial espionage by providing an additional layer of security against known and unknown vulnerabilities.
Increased flexibility: Virtual patching can be used to protect systems and networks that are difficult to patch, such as legacy systems and critical infrastructure.
Reduced downtime: By avoiding the need to apply physical patches, virtual patching helps reduce downtime and minimize the impact on operations.
Virtual patching is a key feature of many OT firewalls, providing organizations with a flexible and effective way to secure their industrial control systems and OT networks against a wide range of threats.
What is an OT firewall?
OT (Operational Technology) firewall is a network security device designed specifically for industrial control systems (ICS) and operational technology (OT) networks. Unlike a traditional IT firewall, an OT firewall is designed to protect critical infrastructure from threats that are specific to industrial environments, such as cyber-physical attacks and industrial espionage.
IT and OT firewalls are very similar in functionality, often made by the same manufacturer like Fortinet, Checkpoint, however there are still some differences between enterprise firewalls and industrial firewalls, mainly in the form factor.
What is the difference between IT and OT Firewall?
There are several key differences between IT and OT firewalls:
Form Factor: Industrial environments are known for rough conditions, depending on industries, ICS firewalls should be able to deal with higher or lower temperatures compared to enterprise firewalls. Humidity could be high in some instances and presence of dust could destroy an IT firewall. Industrial firewalls can be recognised by their ruggedised protective appliance shape and some additional interfaces not used in enterprise environment.
Purpose: IT firewalls are designed to protect data and networks in traditional IT environments, while OT firewalls are designed specifically for industrial control systems and OT networks.
Network architecture: IT networks are typically hierarchical, with a centralized network architecture, while OT networks are often decentralized and use peer-to-peer communication.
Threats: The types of threats faced by IT and OT networks are different, with IT networks facing primarily data-based threats such as malware and cyberattacks, while OT networks face physical threats such as cyber-physical attacks and industrial espionage.
Performance: OT firewalls must meet the demands of high-speed, real-time industrial control systems, which require low latency and high reliability, while IT firewalls are typically designed for lower-speed data networks.
Can we use an IT Firewall in our OT environment?
In general, it is possible to use an IT firewall in an OT (operational technology) environment, but it’s important to consider the specific needs and requirements of the OT environment before doing so.
An IT firewall is designed to protect computer networks from unauthorized access, whereas an OT environment typically includes specialized control systems and devices that are used to monitor and control physical processes such as manufacturing, power generation, or transportation. These OT systems may have different security requirements and operate at different levels of criticality compared to traditional IT systems.
When implementing an IT firewall in an OT environment, it’s important to ensure that the firewall is configured to meet the specific needs and requirements of the OT systems. This may include ensuring that the firewall doesn’t interfere with the communication between devices and control systems, and that it doesn’t negatively impact the performance or reliability of the OT environment. It’s also important to ensure that the firewall is properly maintained and updated to ensure continued effectiveness.
What are the benefits of using an OT firewall?
There are several benefits to using an OT firewall, including:
Enhanced security: OT firewalls provide a high level of security for critical infrastructure, reducing the risk of cyber-physical attacks and industrial espionage.
Improved reliability: OT firewalls are designed to meet the demands of high-speed, real-time industrial control systems, providing low latency and high reliability for critical operations.
Compliance: OT firewalls can help organizations meet industry and regulatory compliance requirements, such as NIST SP 800-82 and NIST SP 800-53.
Ease of use: OT firewalls are typically easy to use and configure, with a user-friendly interface that makes it simple to manage security policies and detect threats.
What are some common use cases for OT firewalls?
Common use cases for OT firewalls include:
Industrial control systems: OT firewalls can be used to secure industrial control systems, including supervisory control and data acquisition (SCADA) systems and programmable logic controllers (PLCs).
Critical infrastructure: OT firewalls can be used to secure critical infrastructure, such as power plants, water treatment facilities, and oil and gas pipelines.
Manufacturing: OT firewalls can be used to secure industrial control systems and networks in manufacturing environments, including process control systems and machine-to-machine (M2M) communication.
Transportation: OT firewalls can be used to secure control systems and networks in transportation systems, such as rail and aviation.
What are some features of an effective OT firewall?
Some features of an effective OT firewall include deep packet inspection, intrusion detection and prevention, network segmentation, application whitelisting, and the ability to monitor and control traffic from a central location.
What are some common challenges when implementing an OT firewall?
Common challenges when implementing an OT firewall include identifying and mapping the industrial control network, ensuring compatibility with legacy systems, minimizing downtime during implementation, and training personnel to properly manage and maintain the firewall.
What are some best practices for implementing and maintaining an OT firewall?
Best practices for implementing and maintaining an OT firewall include conducting a risk assessment, developing a comprehensive security policy, implementing security controls in layers, regularly updating and patching the firewall, and providing ongoing training and support for personnel.
