React Less. Defend More.
MAD20's MITRE ATT&CK™ Training
Detect & respond faster. Training by the best, for the best.
Empower your Security Team to outsmart, outpace & outmanoeuvre adversaries.
MITRE ATT&CK™ Training with MAD20
In today’s digital landscape, where cyber threats loom large and security breaches can have catastrophic consequences, staying ahead of adversaries is imperative. One of the most effective strategies for fortifying cyber defences is through MITRE ATT&CK Defender Training. Originally developed by MITRE®, MAD20 certifies the world’s elite InfoSec teams on MITRE ATT&CK and advanced cyber risk mitigation to combat dynamic and persistent threats. This comprehensive training equips cybersecurity professionals with the knowledge, skills, and tools necessary to detect, analyse, and respond to threats effectively, ultimately bolstering organisational resilience against cyberattacks.
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a globally recognised framework that provides a structured taxonomy of cyber adversary behaviour. By understanding the tactics and techniques employed by threat actors, defenders can proactively identify and mitigate potential vulnerabilities within their systems. However, simply being aware of the framework is not enough. To truly harness its power, organisations must invest in specialised training tailored to their specific security needs.

Real-World Cyberattacks Simulations Training
MAD20™’s courses, assessments, and agile certification program focus on skills training and real-world mastery, enabling certified defenders to immediately adopt and leverage the MITRE ATT&CK® knowledge base in their work environment.
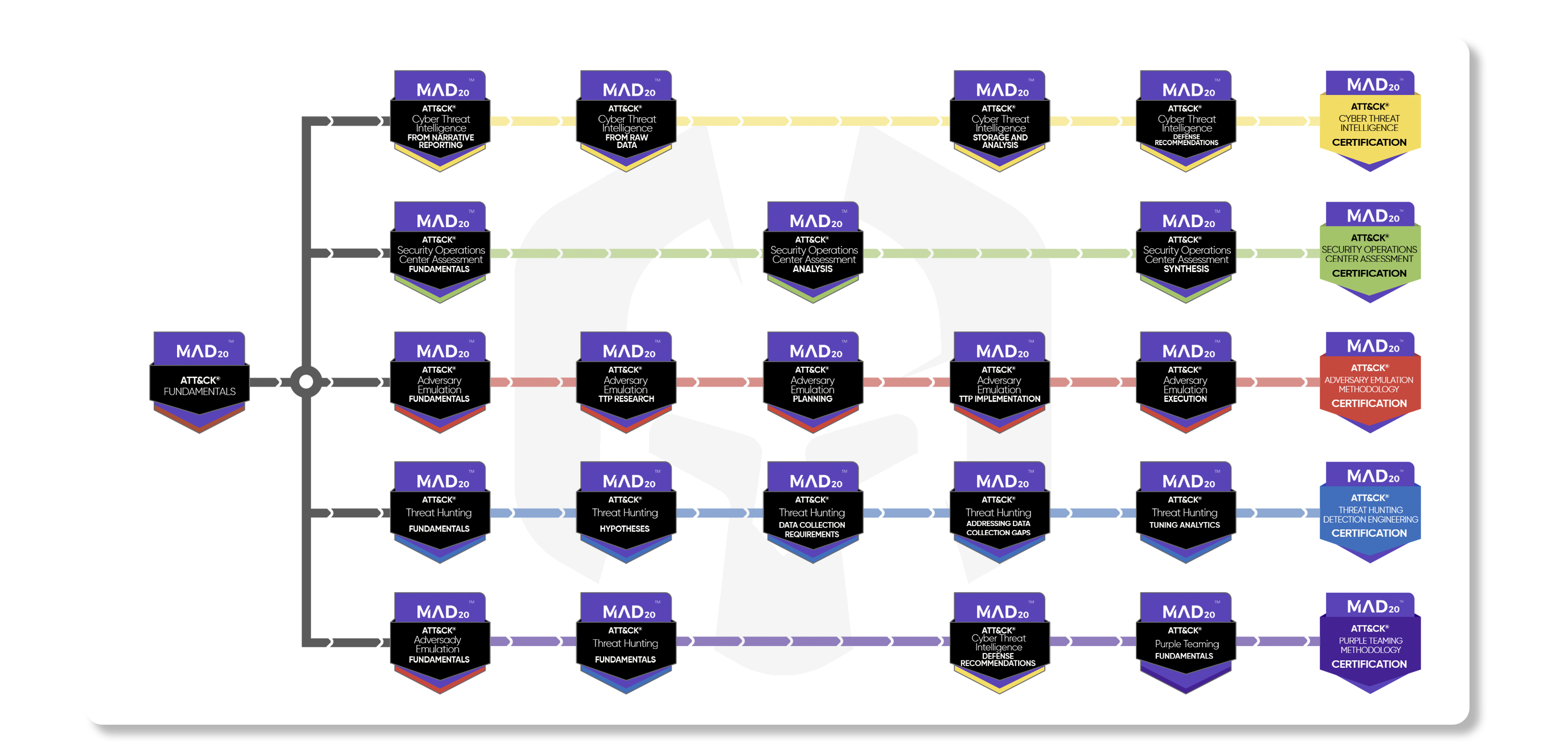
Course Modules and Cetifications
MAD20™’s courses, assessments, and agile certification program focus on skills training and real-world mastery, enabling certified defenders to immediately adopt and leverage the MITRE ATT&CK DEFENDER® knowledge base in their work environment.
ATT&CK Fundamentals
Introduces the MITRE ATT&CK framework, a globally accessible knowledge base, and a cyber adversary behavior model based on real-world observations Familiarizes learners with how ATT&CK documents real-world adversary tactics, techniques, and procedures (TTPs) Demonstrates various ways to exploit this understanding of adversary TTPs to address current (operational) and future (strategic) threats
ATT&CK Cyber Threat Intelligence (CTI)
This training course will Introduce learners to MITRE ATT&CK and why it’s useful for CTI and show learners how to map to ATT&CK from both finished reporting and raw data. It also shares why it’s challenging to store ATT&CK-mapped data and what to consider when doing so and visualises how to perform CTI analysis using ATT&CK-mapped data. It familiarize learners with making defensive recommendations based on CTI analysis.
ATT&CK Security Operations Center (SOC) Assessment
ATT&CK SOC Assessments course familiarises learners with how to implement ATT&CK for visibility into where a SOC needs improvements, and inform how to apply ATT&CK to design a rapid, low overhead, and broad SOC Assessment. It provides tips on how to analyse SOC technologies like tools and data sources, shares best practices for performing interviews and leading discussions on ATT&CK with SOC personnel and educates on how to recommend changes based on assessment results.
ATT&CK Adversary Emulation Methodology
This course prepares you to apply ATT&CK to adversary emulation activities. You will learn foundational adversary emulation concepts, as well as how to research, implement, and ethically execute adversary TTP’s based on ATT&CK. Additionally, you will be prepared to succeed in earning the MAD20 Adversary Emulation certification.
Enroll Now
ATT&CK Threat Hunting Detection Engineering
This course teaches students how to utilise knowledge of adversary TTPs as described in the MITRE ATT&CK framework to develop, test, tune, and employ robust analytics to detect and investigate malicious cyber activity. Students taking this course will learn how to leverage ATT&CK to develop hypotheses, determine data collection requirements, identify and mitigate collection gaps, test and tune analytics using purple-teaming, and conduct a threat-informed hunt.
Enroll Now
ATT&CK Purple Teaming Methodology
Do you want to learn the exciting discipline of Purple Teaming? In this MAD20 Purple Teaming Fundamentals course, you’ll learn to do collaborative purple teaming focused on prioritised malicious behaviors. Experts from MITRE show you the actionable defensive rewards that only come when red and blue teams work together.
What is the MITRE ATT&CK Defender (MAD20) training?
MAD20‘s MITRE ART&CK Training is the only training and certification program developed by the MITRE corporation to teach cybersecurity professionals about the ATT&CK framework. The training is designed to provide learners with all knowledge required to immediately implement the ATT&CK framework across critical areas of cyber operations, threat intelligence, testing and evaluation, and defensive measures.
Are there any certifications for MITRE ATT&CK Trainings?
Currently there are 5 different course modules and certifications:
ATT&CK Fundamentals
ATT&CK Cyber Threat Intelligence (CTI)
ATT&CK Security Operations Center (SOC) Assessment
ATT&CK Adversary Emulation Methodology
ATT&CK Threat Hunting Detection Engineering
ATT&CK Purple Teaming Methodology
Why should I attend MITRE ATT&CK Training?
Enhanced Understanding: Training provides a deep understanding of adversary tactics, techniques, and procedures (TTPs), enabling better comprehension of cyber threats.
Improved Threat Detection: By learning how to apply the MITRE ATT&CK framework, organizations can enhance their threat detection capabilities, identifying and responding to threats more effectively.
Proactive Defense: Training empowers security teams to adopt a proactive defense posture by enabling them to anticipate and mitigate potential threats before they escalate.
Standardized Framework: MITRE ATT&CK offers a standardized language and framework for discussing and addressing cybersecurity issues, facilitating better collaboration and communication among security professionals.
Better Incident Response: Training equips individuals with the skills to leverage the MITRE ATT&CK framework for incident response, enabling faster and more effective mitigation of cyber incidents.
Strategic Planning: Understanding the tactics used by adversaries allows organizations to develop more strategic cybersecurity plans and allocate resources more effectively to defend against emerging threats.
Continuous Improvement: Training provides the foundation for continuous improvement in cybersecurity practices, enabling organizations to adapt and evolve their defenses in response to changing threat landscapes.
Credentialing Opportunities: Completion of MITRE ATT&CK training programs may lead to certifications or credentials that validate individuals’ expertise in threat-informed defense strategies, enhancing their professional credentials within the cybersecurity field.
What is MITRE ATT&CK Framework?
The MITRE ATT&CK Framework (Adversarial Tactics, Techniques, and Common Knowledge) is a knowledge base developed by MITRE Corporation that catalogs the tactics, techniques, and procedures (TTPs) used by cyber adversaries. It provides a structured and comprehensive way to understand, categorize, and analyze the behavior of attackers across different stages of the cyber kill chain.
What are MITRE ATT&CK TTP?
MITRE ATT&CK TTP stands for Tactics, Techniques, and Procedures within the MITRE ATT&CK framework.
Tactics: Tactics represent the high-level objectives or goals that adversaries aim to achieve during a cyber attack. These objectives are organized into categories that correspond to different stages of the cyber kill chain. Some common tactics include initial access, execution, persistence, privilege escalation, defense evasion, credential access, discovery, lateral movement, collection, exfiltration, and impact. Tactics provide a structured way to understand the overall goals of cyber adversaries.
Techniques: Techniques are specific methods or actions that adversaries use to accomplish their tactical objectives. Each technique is associated with one or more tactics, indicating the stage of the attack where it is typically employed. For example, techniques under the “execution” tactic might include code execution, scripting, or command-line interface. The MITRE ATT&CK framework catalogs hundreds of techniques used by adversaries across various stages of the cyber kill chain.
Procedures: Procedures, also known as sub-techniques, represent specific implementations or variations of techniques used by adversaries. While techniques describe general methods or approaches, procedures provide more granular details about how those techniques are executed in practice. For example, a technique like “remote file copy” might have multiple procedures associated with different tools, commands, or protocols used to achieve file transfer between systems.
What is the difference between Cyber Kill Chain and MITRE ATT&CK?
Cyber Kill Chain: The Cyber Kill Chain focuses primarily on the stages of a cyber attack, from initial reconnaissance to data exfiltration, with an emphasis on understanding the sequence of events and disrupting the attacker’s operations.
MITRE ATT&CK Framework: The MITRE ATT&CK Framework covers a broader range of adversary behavior, cataloging specific tactics, techniques, and procedures used by attackers across different stages of the cyber kill chain. It provides a detailed taxonomy for understanding and categorizing adversary behavior, regardless of the stage of the attack.
Is there MITRE ATT&CK for ICS & OT Security?
Yes, there is a version of the MITRE ATT&CK framework specifically tailored for Industrial Control Systems (ICS) and Operational Technology (OT) security. This version of the framework is designed to address the unique challenges and threats faced by organizations operating in industrial and critical infrastructure sectors.
The MITRE ATT&CK for ICS framework provides insights into the tactics, techniques, and procedures (TTPs) commonly observed in attacks targeting ICS and OT environments. It covers a wide range of adversarial behaviors relevant to these sectors, including reconnaissance, initial access, command and control, impact, and more.
This specialized version of the ATT&CK framework is valuable for organizations in industries such as energy, manufacturing, transportation, and utilities, where ICS and OT systems play a critical role in operations. By understanding the specific tactics and techniques used by adversaries to target these systems, organizations can better assess and mitigate risks, enhance detection and response capabilities, and strengthen the security posture of their ICS and OT environments.
What are MITRE ATT&CK Certifications?
Currently there are 5 different MITRE ATT&CK certifications, provided by MAD20, but the curriculum is constantly growing and offers skills training and credentialing in the areas of:
- ATT&CK® Cyber Threat Intelligence Certification
- ATT&CK® Security Operations Center Assessment Certification
- ATT&CK® Adversary Emulation Methodology Certification
- ATT&CK® Threat Hunting and Detection Engineering Certification
- ATT&CK® Purple Teaming Methodology Certification
