React Less. Defend More.
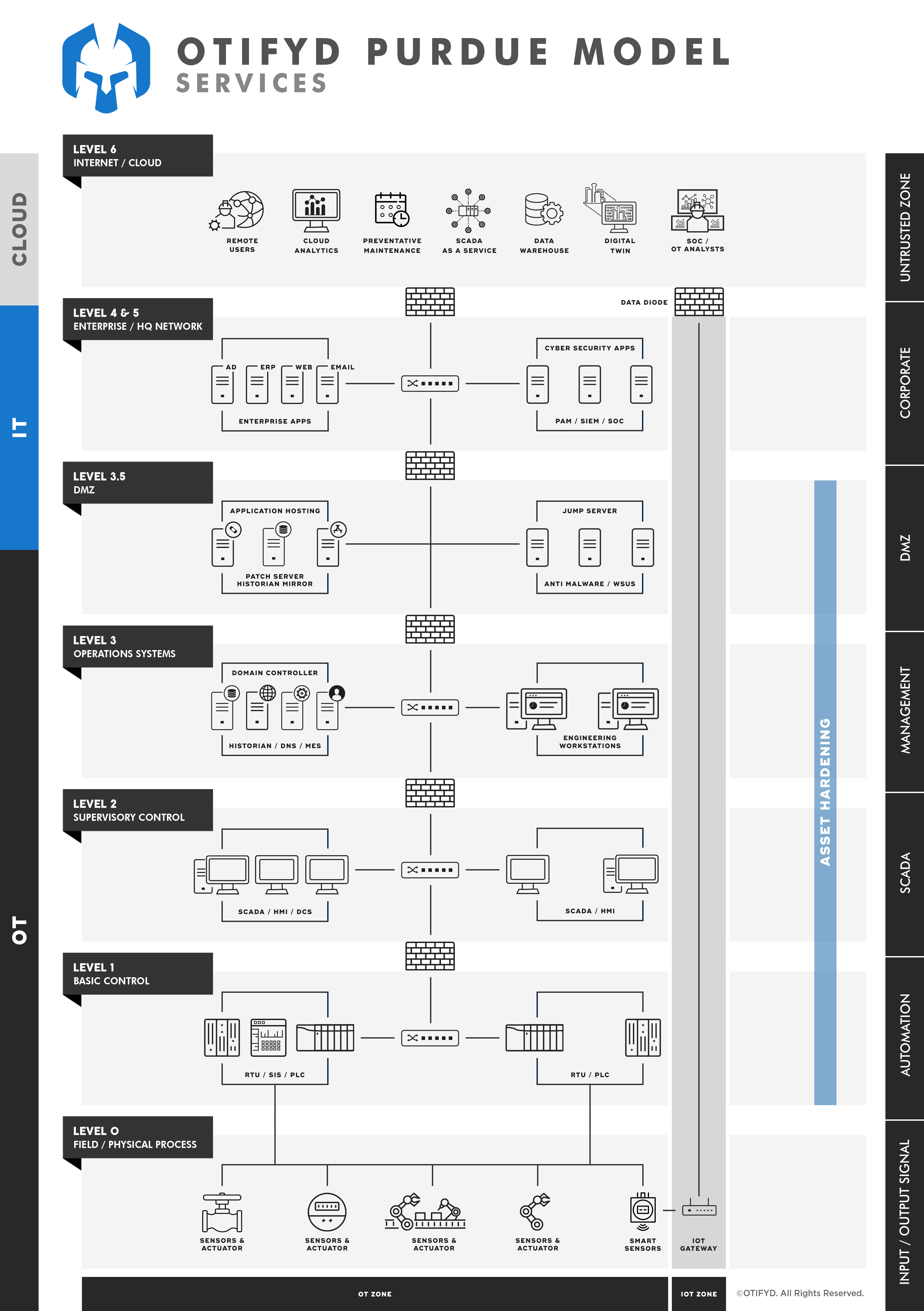
OT Asset Hardening
Reduce security risk by eliminating potential attack vectors across your OT environment.
OT Asset Hardening Overview
Asset Hardening (also known as “System Hardening”) is a collection of tools, techniques, and best practices to reduce vulnerability in technology applications, systems, infrastructure, firmware, and other areas (e.g., physical access).
The goal of our Operational Technology (OT) Asset Hardening service is to reduce security risk by eliminating potential attack vectors and condensing the environment’s attack surface. By removing unnecessary programs, user accounts, functionality, connectivity, ports, permissions, physical access, etc. malicious attackers and malware have fewer opportunities to gain a foothold within your OT environment.
Asset Hardening demands a methodical approach to audit, identify, remove and control potential security vulnerabilities throughout your OT environment. Our OT Asset Hardening service considers:
- Application hardening;
- Operating System (OS) hardening;
- Server hardening;
- Endpoint hardening;
- Database hardening;
- Network hardening.
Although the principles of Asset Hardening are universal across both OT/IT environments, specific tools and techniques do vary depending on the type of hardening you are carrying out and also the OT assets being hardened. How the OT assets are used in day-to-day operations must also be considered, as removing functionality without the proper review and analysis can lead to unexpected issues and system behaviour.
Asset Hardening is needed throughout the lifecycle of OT assets, from initial installation, through configuration, maintenance and support, to end-of-life decommissioning. Asset Hardening is also a requirement of regulatory mandates and is increasingly demanded by cyber insurers.
Why Conduct OT Asset Hardening?
OT Asset Hardening is critical for cyber security for several reasons, these include:
- The fact that many OT assets and supporting network infrastructure were not built with security in mind makes them more vulnerable to malicious and non-malicious cyber threats;
- Regular software patching of OT assets is often challenging, requiring alternative compensating controls to provide security;
- Over time, systems that were originally commissioned as secure become less secure as changes are made throughout their operational lifecycle;
- Often, organisations deploy assets within OT environments with IT-standard software and/or configuration, which is unnecessary and potentially increasing risk exposure by widening the cyber attack surface;
- In many cases, OT assets are not connected to directory services (e.g. ActiveDirectory or equivalent) and lack standardised policies required for security management, enforcement and auditing.
Executing operationally safe OT Asset Hardening remediation requires deep knowledge of industrial assets, systems and the processes they manage. Many policies and settings that would work well in a typical IT environment create operational reliability issues in OT. Therefore, it is critical that those conducting OT Asset Hardening activities are experienced and trained in the complexities of OT and its nuances.
OTIFYDs deep experience across OT vendors and different industries enable us to effectively harden assets while maintaining operational availability and reliability. Documentation cannot provide all of the potential implications of hardening configuration settings in a certain way or why certain service or user accounts exist. It is only with experience and the learnings gained by years of working with OT assets that you come to understand “what is” and “what is not” feasible or pragmatic when it comes to Asset Hardening.
We partner with our clients to accelerate their OT cyber security maturity through our Asset Hardening service. We achieve this by using best-in-class vulnerability assessment tooling and our deep industry experience to rapidly improve risk exposure of their OT environments.
Key Benefits of OT Asset Hardening
- Enhanced OT asset/system functionality: Since fewer applications and less functionality means there is less risk of operational issues, misconfigurations, incompatibilities, and malicious compromise.
- Significantly improved security: A reduced attack surface translates into a lower risk of data breaches, unauthorised access, systems hacking, misuse, or malware. Ultimately this enhances operational resilience, maximising the availability and integrity of your OT environment.
- Simplified compliance and audit demands: Fewer applications and user accounts coupled with a less complex environment means auditing the OT environment will usually be more transparent and straightforward.
Deliverables from our OT Asset Hardening Service
We provide consultation and expertise to natively secure and harden your OT environments, this typical entails:
- High-level vulnerability assessment;
- Analysis of the current situation using trusted tooling, our expertise and industry best practices;
- Establishment of current security posture and remediation roadmap;
- Patching and risk reduction recommendations/plans.
We can also provide proactive consultation on OT environments still in the planning or project phases.
What is Operating System Hardening?
The practice of minimising the attack surface of a computer system or server. The goal is to reduce the number of security weaknesses and vulnerabilities that threat actors can exploit.
What is Asset Hardening?
Asset hardening refers to the process of improving the security of an asset or system by making it more resistant to various types of attacks and threats. This can be done through a variety of techniques, such as implementing physical security measures, using stronger passwords and authentication protocols, installing software updates and patches, and limiting access to sensitive information.
Asset hardening is often used in the context of cybersecurity, where it is used to protect computer systems, networks, and other digital assets from hackers, viruses, and other types of malicious attacks. By hardening assets, organisations can reduce the risk of cyberattacks, minimise the impact of any attacks that do occur, and ensure that critical data and systems remain secure and operational.
In addition to digital assets, asset hardening can also be applied to physical assets, such as buildings, vehicles, and other infrastructure. This can include measures such as reinforced walls and doors, surveillance cameras, alarms, and other security features designed to prevent theft, vandalism, and other types of physical attacks.
Why is Asset Hardening Important?
Asset hardening is important for several reasons:
Protection against cyberattacks: With the increasing prevalence of cyberattacks, it is crucial for organisations to harden their assets to prevent unauthorised access, data theft, and other forms of cybercrime. By implementing various security measures, organisations can reduce the risk of cyberattacks and protect their critical assets.
Compliance with regulations: Many industries, such as healthcare and finance, are subject to strict regulations that require them to implement certain security measures to protect sensitive data. Asset hardening can help organisations comply with these regulations and avoid penalties for non-compliance.
Business continuity: Hardening assets can help ensure that critical systems remain operational in the event of an attack or other disruptive event. By reducing the risk of downtime and data loss, organisations can maintain business continuity and minimise the impact of any security incidents.
Reputation management: Security incidents can damage an organisation’s reputation and erode customer trust. By hardening assets, organisations can demonstrate their commitment to security and protect their reputation in the event of a security breach.
Overall, asset hardening is an essential aspect of modern cybersecurity and is critical for protecting assets from a wide range of threats, including cyberattacks, theft, and vandalism.
How do you Harden an Asset?
You harden an Asset by reducing its “attack surface,” which is the combination of all the potential flaws and backdoors in technology that can be exploited by threat actors. These vulnerabilities can occur in many ways. Common attack surface vulnerabilities include:
- Default passwords.
- Hardcoded passwords and other credentials stored in plain text files.
- Unpatched software and firmware vulnerabilities
- Lack, or deficiency, of privileged access controls.
- Poorly configured BIOS, firewalls, ports, servers, switches, routers, or other parts of the infrastructure.
- Unencrypted, or inadequately encrypted, network traffic or data at rest.
What are the Benefits of Asset Hardening
While system hardening requires a large, continuous effort, it provides substantial benefits for organisations. Here are several notable benefits:
- A higher level of security—the main purpose of system hardening techniques and tools is to reduce the attack surface. This translates into a significantly lower risk of malware, unauthorised access, data breaches, or other malicious activity.
- Better system functionality—system hardening best practices often involve reducing the number of programs and functionality. This translates into fewer operational issues, reduced chance of misconfiguration which can affect user operations, fewer incompatibilities, and also reduced chance of cyber attacks, which in themselves hurt user functionality.
- Simplified compliance and auditing—system hardening techniques can help turn a complex environment into a simpler one with fewer programs and accounts, and stable, predictable configuration. This translates into a more straightforward and transparent environment which is simpler to monitor and audit.
Is "OT Asset Hardening" the Same as "ICS Asset Hardening"?
OT (Operational Technology) asset hardening and ICS (Industrial Control Systems) asset hardening are related concepts.
Both OT and ICS asset hardening focus on improving the security of digital assets, such as industrial control systems, SCADA (Supervisory Control and Data Acquisition) systems, and other software applications that are used to control and monitor industrial processes. This can involve implementing various security measures, such as firewalls, intrusion detection systems, and encryption, to prevent unauthorised access, data breaches, and other types of cyberattacks.
Also considered are all physical assets, such as machinery, equipment, and other infrastructure, that are used to control and monitor various industrial processes. This can involve implementing physical security measures, such as surveillance cameras, access controls, and perimeter fencing, to prevent unauthorised access and protect the equipment from damage or tampering.
OT / ICS asset hardening is important for protecting industrial processes and infrastructure from various threats. Many organisations use a combination of physical and digital security measures to harden their assets and minimise the risk of security incidents.
What is CIS Benchmark for Hardening?
CIS benchmarks are configuration baselines and best practices for securely configuring a system. Each of the guidance recommendations references one or more CIS controls that were developed to help organisations improve their cyber defence capabilities.