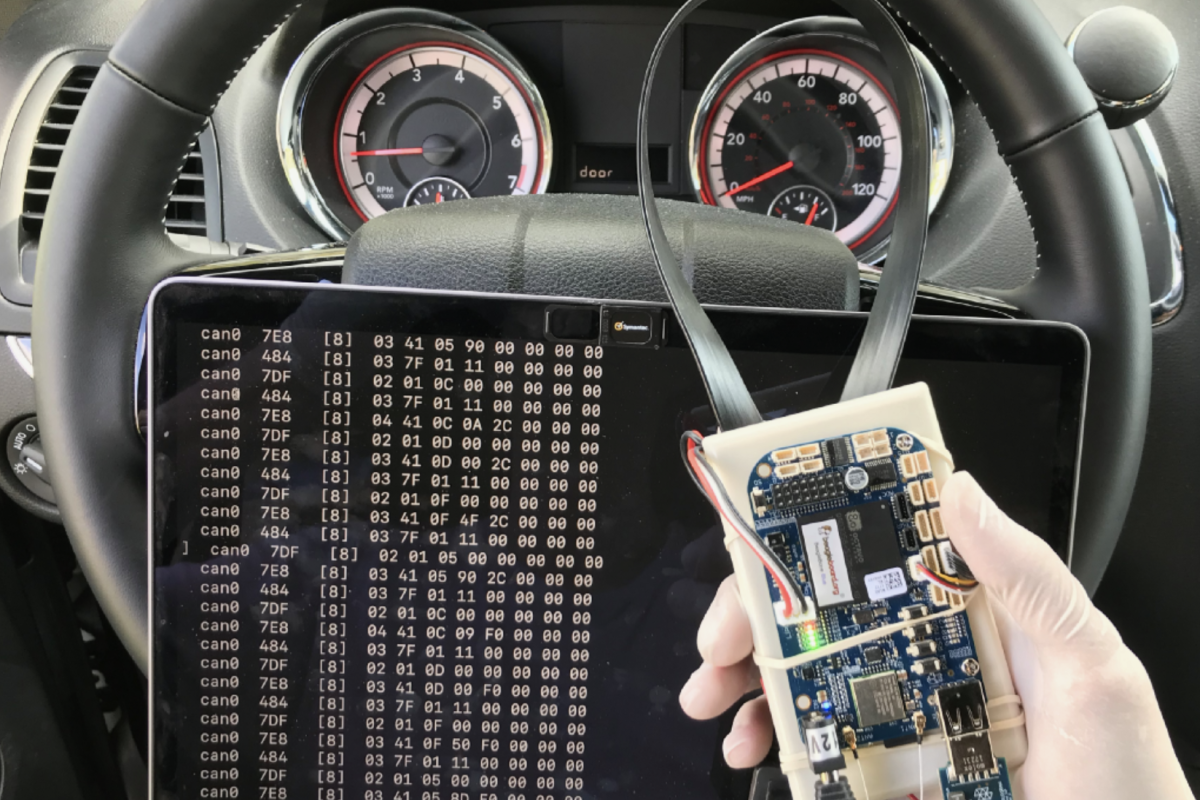
Hacking Controller Area Network (CAN Bus)
What is Controller Area Network (CAN Bus)?
In short words, it’s a communication system made for vehicle intercommunication.
It is a network protocol that is commonly used in automobiles to allow different electronic components within the vehicle to communicate with each other over a shared two-wire bus. However, CAN is also used in a wide range of other industrial and commercial applications beyond just automobiles.
Controller Area Network (CAN) hacking involves exploiting vulnerabilities in the CAN bus network, which is a communication protocol used in vehicles and other industrial systems to allow different electronic components to communicate with each other. HackerOne is a platform that allows companies to engage with ethical hackers and security researchers to identify and fix security vulnerabilities in their products and systems.
How to hack CAN bus?
To perform a CAN bus hack through HackerOne, an ethical hacker would typically follow these steps:
Reconnaissance:
The hacker would gather information about the target system, such as the make and model of the vehicle or industrial system, the firmware and software versions, and any other details that could be used to identify potential vulnerabilities.
Vulnerability Scanning:
The hacker would use specialized tools and techniques to scan the target system for known vulnerabilities and weaknesses in the CAN bus network. This could include looking for unsecured communication channels, weak encryption or authentication mechanisms, or other flaws in the network architecture.
Exploitation:
Once the hacker has identified a vulnerability in the CAN bus network, they would attempt to exploit it to gain access to the target system. This could involve injecting malicious code into the network, exploiting a buffer overflow or other memory-related vulnerability, or using other techniques to bypass security controls and gain control of the system.
Post-exploitation:
After gaining access to the target system, the hacker would typically explore the system to identify additional vulnerabilities or sensitive information that could be leveraged for further attacks. This could include stealing data, escalating privileges, or installing backdoors or other malware to maintain persistence on the system.
Reporting:
Finally, the hacker would report their findings to the company or organization through the HackerOne platform, providing detailed information about the vulnerabilities they discovered and suggestions for how to fix them. The company would then have an opportunity to address the vulnerabilities before they are exploited by malicious actors.
Controller Area Network (CAN) hacking involves exploiting vulnerabilities in the CAN bus network, which is a communication protocol used in vehicles and other industrial systems to allow different electronic components to communicate with each other. HackerOne is a platform that allows companies to engage with ethical hackers and security researchers to identify and fix security vulnerabilities in their products and systems.