React Less. Defend More.
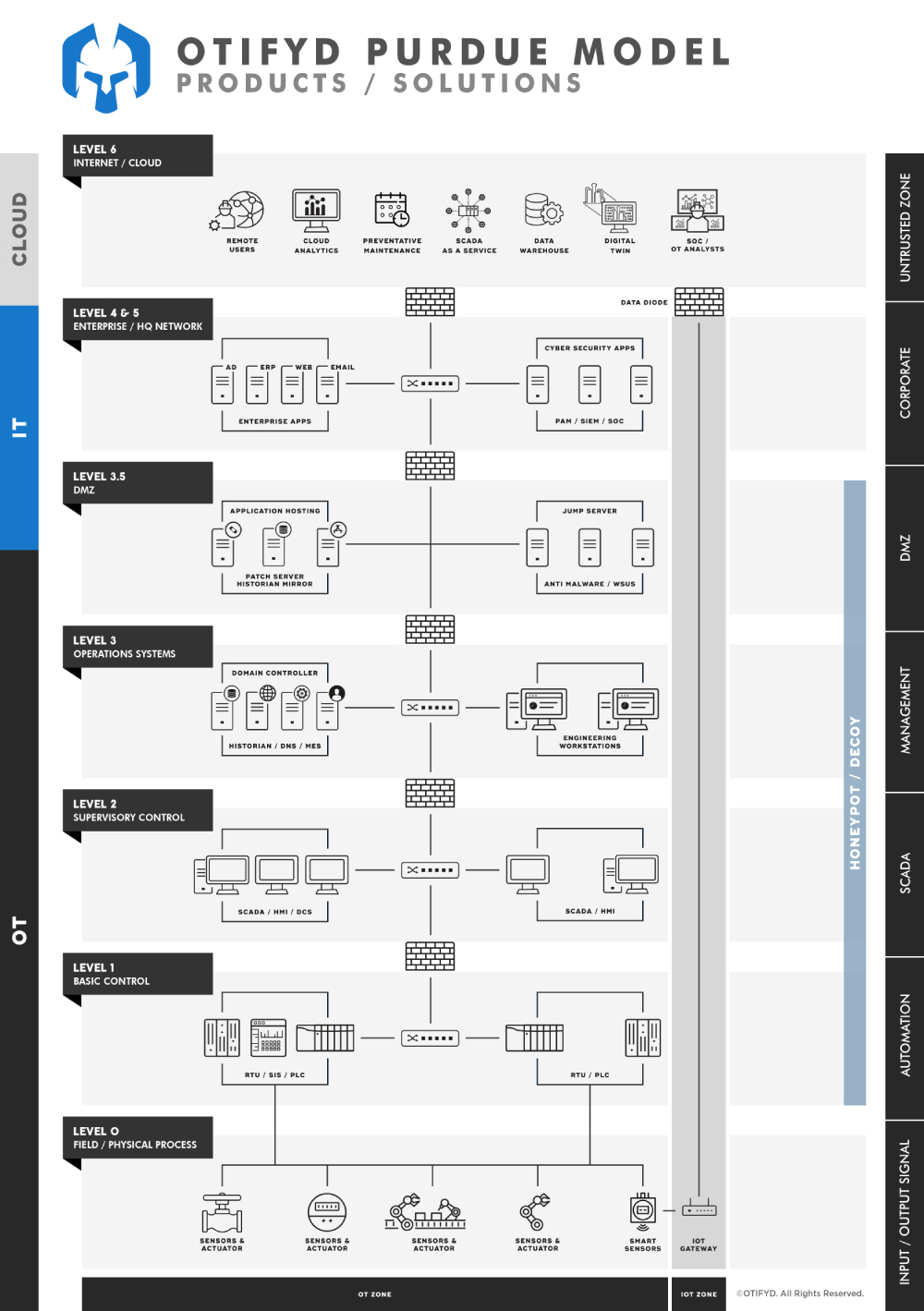
INDUSTRIAL HONEYPOT / DECOY
Detect malicious network activities in the recognisance phase of the “Cyber Kill Chain” via decoys and honeypots and receive high-fidelity alerts.
Honeypots & Decoys
The use of honeypots in Operational Technology (OT) networks is crucial because they help to improve the overall security posture of these networks. A honeypot is a decoy system that is designed to imitate a vulnerable system or a high-value target, with the aim of attracting and detecting malicious activity.The concept is simple. Honeypots or decoys both rely on setting traps for attackers. However, contemporary deception technology has evolved far beyond its roots in simple honeypots typically used for research.
The technology has matured into deception platforms that include decoys, lures, applications, data, database and active directory and ICS assets deceptions for comprehensive threat detection. Additionally, deception platforms can now provide extensive attack analysis and response automation capabilities. These solutions have removed the management and scalability complexity seen previously with honeypots so that companies, both small and large, can deploy and manage deception environments easily across cloud, on-premises, and operational technology networks.
Deception Technologies
Deception technology uses full operating systems, services, and applications to create an environment where decoys blend thoroughly into the production environment and are not identifiable as decoys to the attacker.
The ability to run the same software as production assets takes authenticity to the next level. This authenticity extends beyond the computing assets to include deceptive file shares and user credentials that appear identical to production assets. Deception can also include emulations for Industrial Control systems and network assets, covering the entire scope of devices and systems an attacker could encounter.
Modern deception platforms place decoys out-of-band, rather than in-line on the network. This deployment model prevents an attacker from using them as a pivot point to attack the rest of the environment. Advanced deception platforms also offer the option to route attacker traffic out through a dedicated connection, allowing the incident response team to observe and analyse the activity safely without risking internal assets.
In the context of OT networks, honeypots can play a significant role in the following ways:

Deception for Visibility
Organisations place deceptive decoys, breadcrumbs, and lures throughout the network to make the entire environment a trap, turning the entire environment into a virtual minefield to proactively lure and misdirect an in-network attacker into engaging and revealing their presence.
By mimicking real systems and infrastructure, honeypots can attract attackers and give security teams a window into the tactics, techniques, and procedures that attackers are using. This information can be used to improve the overall security posture of a network and detect threats in real-time.
One of the key benefits of using deception for visibility is that it allows security teams to detect threats early, before they have a chance to spread or cause significant damage. This can help to minimize the overall impact of an attack and improve the ability of security teams to respond to security incidents.
Additionally, deception for visibility can also help security teams to understand the motivations and objectives of attackers. By observing the behavior of attackers when they interact with honeypots, security teams can gain insights into the types of targets that attackers are interested in, the methods that they are using to carry out attacks, and the techniques that they are employing to evade detection.
Deception for visibility is an effective tool for improving the visibility and security of networks. By using honeypots and other decoy systems, security teams can detect threats early, understand the motivations and objectives of attackers, and improve their ability to respond to security incidents.
Deception for Early Detection
Honeypots can help to detect malicious activity at an early stage, before it has the opportunity to spread or cause significant damage. This is because honeypots are designed to be highly attractive to attackers, who are likely to target them before any other systems in the network.
By making the whole network a trap, information security teams can go on the offence against attackers, allowing them to detect an attack early in the cycle, gather company-specific threat intelligence, and derail the attacker before they can do any serious damage.
One of the key advantages of using deception for early detection is that it can help to reduce the dwell time of an attack. Dwell time is the amount of time that a threat goes undetected on a network before it is discovered. By detecting threats early, security teams can reduce the dwell time and minimize the impact of an attack.
Additionally, deception for early detection can also help to improve the overall security posture of a network. By providing a view into the methods that attackers are using, security teams can identify and patch vulnerabilities, deploy countermeasures, and improve their ability to respond to security incidents.
Another benefit of deception for early detection is that it can provide a controlled environment for security teams to observe and contain malicious activity. Because honeypots are isolated from the rest of the network, they provide a safe place for security teams to study the behavior of attackers and develop strategies for mitigating the threat.
Deception for Risk Mitigation
Deception platforms are also instrumental in attack analysis, forensics, and remediation. Deception systems automate the correlation of attack data and raise only substantiated alerts that are backed by details on the attacker’s tactics, techniques, and procedures. They can also collect accurate Indicators of Compromise (IOC) information to gain enhanced adversary intelligence and build better overall defences.
Modern deception platforms can extend onto the endpoints, where attackers frequently leverage stolen credentials or misconfigurations to expand their foothold across the environment. By inserting deceptive credentials into the host, or even intercepting an attacker’s efforts to leverage network authentication systems such as Active Directory, the information security team gains valuable insights and visibility into an attacker’s activities while making the task much more complicated for a malicious actor.
One of the key benefits of using deception for risk mitigation is that it can help to reduce the impact of an attack. By detecting threats early and containing them in a controlled environment, security teams can minimize the damage that is done and reduce the overall risk to the network.
Another benefit of deception for risk mitigation is that it can provide security teams with valuable information about the tactics, techniques, and procedures that attackers are using. This information can be used to improve the overall security posture of the network by patching vulnerabilities, deploying countermeasures, and improving the ability of security teams to respond to security incidents.
Additionally, deception for risk mitigation can also help to increase the visibility of a network. By attracting and observing attackers, security teams can gain a better understanding of the types of threats that they are facing and the methods that they are using to carry out attacks. This information can then be used to improve the security posture of the network and reduce the overall risk of a breach.
What’s an ICS Honeypot?
A honeypot is part of deception technology to simulate an asset on a network to lure intruders to believe it’s a legitimate target. Their primary job is to collect intelligence in the earliest phase of cyber kill chain, reconnaissance. Once triggered by a network scanner or failed login attempt, it will send a high fidelity alert to the SOC which leads into taking immediate action.
Is a Honeypot an IDS?
Honeypots are part of an organisation’s intrusion detection system, but they are not IDS or IPS. Honeypot is a decoy simulating an asset like an active directory, historian server, workstation or even HMI or PLC, but they are not an inline device monitoring an entire network.
Can a Honeypot Detect Malware?
Honeypots are not designed to detect malware. Consider them a workstation, a server or PLC, connected to a network. If an attacker attempt to connect to these decoys, they will trigger an alert.
What’s the Benefit of using Honeypots in Network Security?
Early detection of malicious activity in the cyber kill chain reconnaissance phase.
What’s Threat Deception Technology?
Deception technology is part of proactive defence cybersecurity solutions by populating your environment with decoys (fake endpoints, PLCs, servers, files, services, and databases that detect threats early with low rates of false positives.
Why Should I use a Honeypot in my OT network?
Honeypots are an important part of a comprehensive ICS cybersecurity strategy. Their main objective is to expose malicious activities and vulnerabilities in the existing system and draw a hacker away from legitimate targets.
What´s an industrial honeynet?
An industrial honeynet is a specialized type of honeynet that is used to protect and monitor industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems. These systems are used in various industries such as manufacturing, energy, and transportation, and are critical for the operation of infrastructure and facilities.
The primary goal of an industrial honeynet is to detect and prevent cyber attacks that target these systems, which can have serious consequences such as equipment damage, production downtime, and even safety risks. Industrial honeynets are designed to mimic the operation of real ICS and SCADA systems, with the aim of attracting and detecting attackers who are attempting to exploit vulnerabilities in these systems.
