React Less. Defend More.
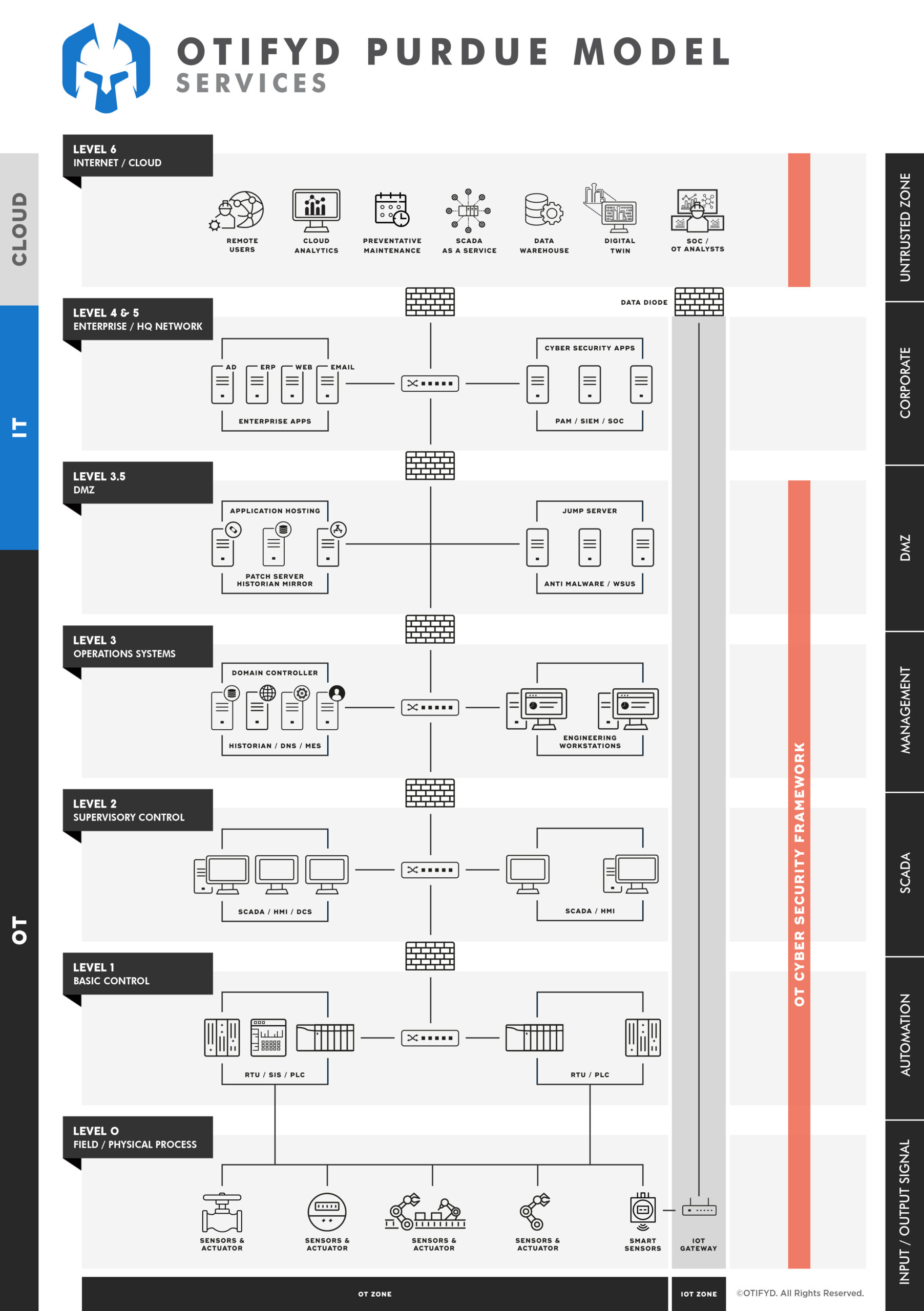
OT Cyber Security Framework
A reliable, standardised, systematic way to mitigate cyber risk, regardless of the OT environment’s complexity.
OT Cyber Security Framework (OT-CSF) Overview
Operational Technology (OT) cyber security is an overwhelming endeavour, whether you’re a business leader, such as the Chief Information Security Officer (CISO), OT Security Manager or a security engineer defending critical OT assets, data and infrastructure against advanced threats. Security frameworks can help.
Knowing which aspects of cyber security to focus on, complying with a growing number of regulations, and taking a proactive stance can be hard with limited resources and time. Security frameworks can help you by acting as a “compass” to guide you throughout your OT cyber security and compliance journey.
Why Deploy an OT Cyber Security Framework?
An OT-CSF removes the guesswork in securing OT assets. Frameworks give cyber security managers a reliable, standardised, systematic way to mitigate cyber risk, regardless of the OT environment’s complexity.
An OT-CSF helps teams address cyber security challenges, providing a strategic, well-thought plan to protect its OT assets, infrastructure and data. The frameworks offer guidance, helping security leaders manage their organisation’s cyber risks more intelligently. Organisations can adapt and adjust existing well-known frameworks to meet their own specific needs including compliance with commercial or government regulations.
In summary, organisations are increasingly expected to abide by standard cyber security practices, and using OT-CSF makes compliance easier and smarter. An OT-CSF helps organisations follow the correct security procedures which keep the organisation safe and provides tangible risk reduction.
Key Benefits of Deploying an OT Cyber Security Framework
- An OT-CSF helps save you time by providing you with a clear structure for taking action. With a framework, you can easily map where you are on your OT cyber security journey and identify gaps so you can have clear, actionable conversations with stakeholders;
- An OT-CSF facilitates communication with all stakeholders on requirements and clarifies roles and responsibilities;
- An OT-CSF provides consistency in interpreting security needs across the organisation. Without a framework, there is a risk that stakeholders across the organisation, each responsible for some aspect of cyber security, interpret requirements differently, causing errors and unforeseen gaps in execution;
- An OT-CSF translates generic external standards and regulatory requirements into executable processes;
- An OT-CSF creates the foundation to measure the effectiveness of security practices and benchmarks within an organisation.
- Last, but not least, a framework can be a useful tool to explain in a common language what you are doing in security to even the non-security-versed people in the organisation.
Deliverables from our OT Cyber Security Framework Service
This service offering is tailored to your organisation’s specific needs. Typical OT-CSF implementation produces the following:
- High-level OT cyber security policy based on globally recognised security standards;
- Detailed procedure set defining requirements, controls and responsibilities for key OT cyber security areas such as asset management, access control, governance, training, system development and maintenance, incident response, business continuity and disaster recovery;
- A pragmatic roadmap to roll out the OT policy and supporting processes defined in the framework including the implementation of required technical controls.
What is a Cyber Security Framework?
A cyber security framework is a collection of best practices that an organisation should follow to manage its cyber security risk. The goal of the framework is to reduce the company’s exposure to cyber attacks, and to identify the areas most at risk and other compromising activity perpetrated by cyber criminals.
Why Do I Need a Cyber Security Framework?
A Cyber Security Framework integrates industry standards, best practices and regulatory compliance requirements to help organisations manage their cyber security risks. It provides a common language that allows staff at all levels within an organisation, and at all points in a supply chain, to develop a shared understanding of their cyber security risks.
How Do I Create a Cyber Security Framework?
The typical process is as follows:
Step 1: Set your target goals.
Step 2: Create a detailed risk profile.
Step 3: Assess your current position.
Step 4: Gap analysis and action plan.
Step 5: Implement your action plan.
What Functions Does a Typical Cyber Security Framework Address?
The five core functions of a cyber security framework are:
- Identify
- Protect
- Detect
- Respond
- Recover
NIST defines the framework core on its official website as a set of cyber security activities, desired outcomes, and applicable informative references common across critical infrastructure sectors.
What is OT Cyber Security?
Operational Technology (OT) cyber security refers to the set of procedures and best practices designed to mitigate and prevent the exploitation of cyber-physical systems and industrial control systems (ICS). Industrial control systems are digital networks employed across a wide variety of sectors and services to automate production processes.
How to Choose an OT Security Framework that Suits My Needs?
The first step is to understand the importance of cyber security guidelines, best practices and applicable regulatory requirements. Then review the options to choose a framework that suits your organisation’s unique challenges.