What Does a Realistic OT Cybersecurity Baseline Actually Look Like?
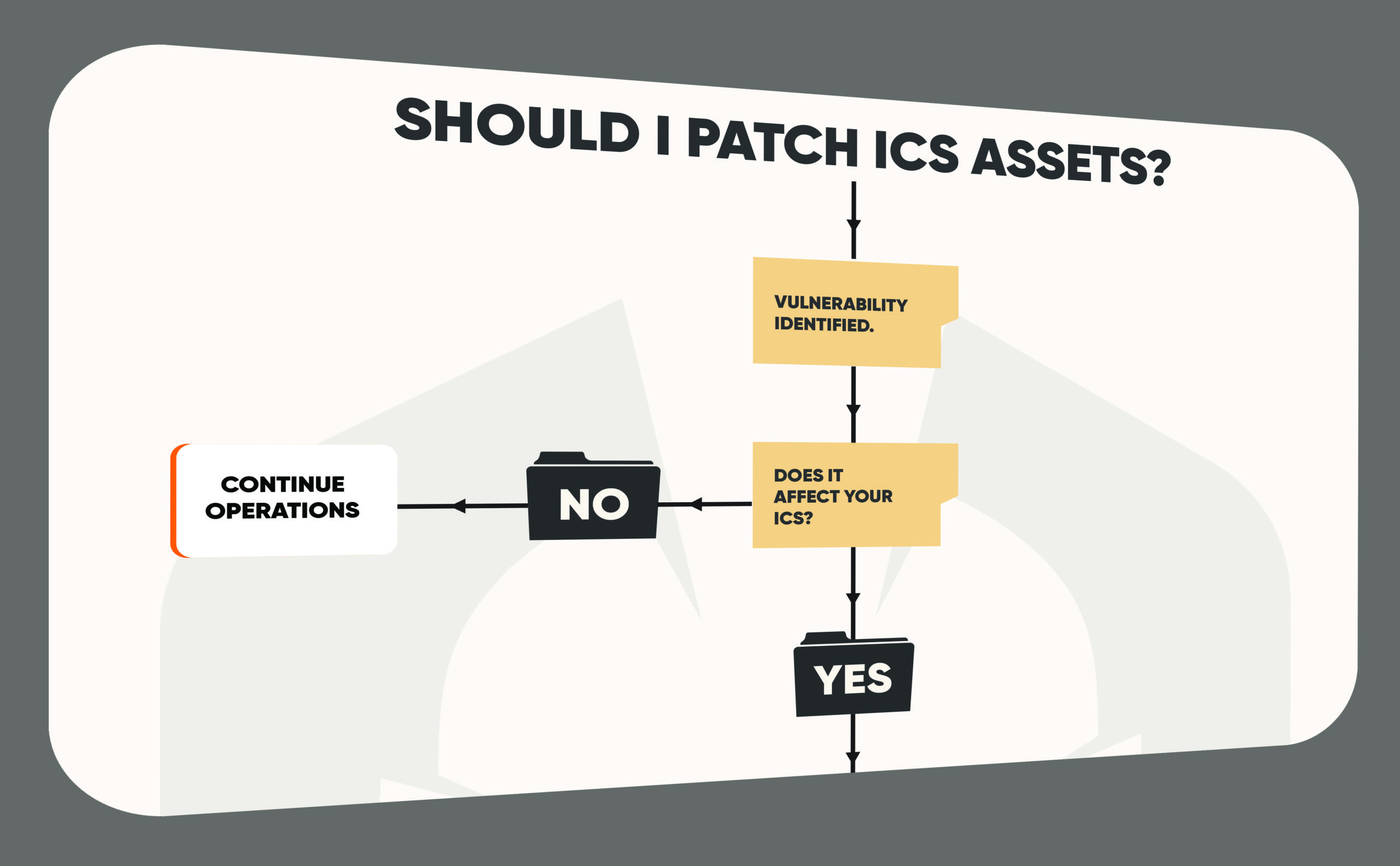
What Does a Realistic OT Cybersecurity Baseline Actually Look Like? From Reflection to Action by an OT Cybersecurity Practitioner Across the previous series (Part 1, Part 2, Part 3 & Part 4), I reflected on governance behaviour, visibility gaps, incentives, and the tendency to wait for perfection. A consistent theme emerged: maturity stalls not because…
View details