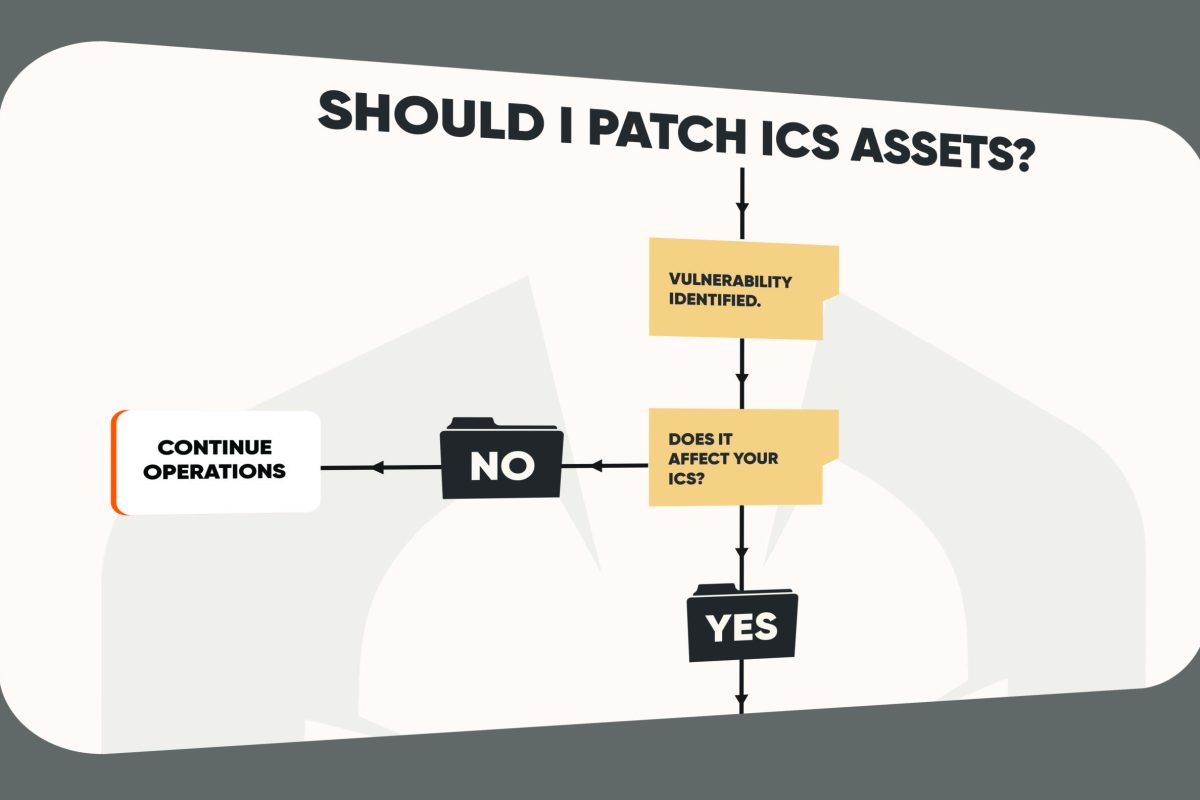
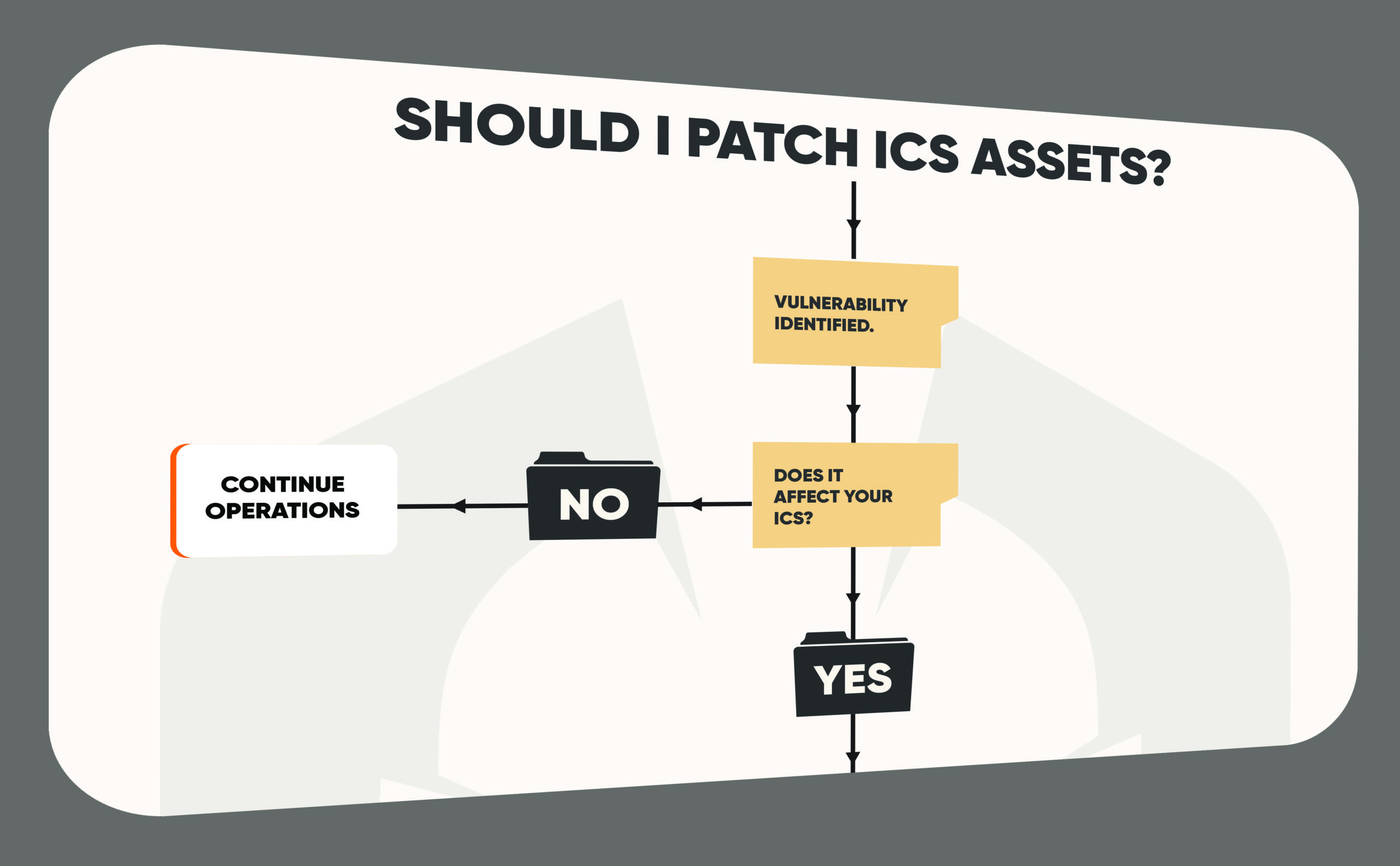
The decision to patch ICS assets is a topic of significant debate in the cybersecurity community. Unlike IT systems, where patching is generally encouraged to address vulnerabilities, ICS environments often prioritize stability and availability, leading to differing views on whether patching should be immediate or even necessary in every case. Many experts argue that patching can introduce more risk than it mitigates by potentially destabilizing critical systems. Others, however, emphasize that patching is essential to protect against evolving threats that could compromise safety and functionality. This flowchart highlights a balanced approach, helping organizations make informed decisions based on risk, operational needs, and available mitigations.
Using this flowchart can help organizations make more informed, risk-based decisions about when and how to patch ICS assets, balancing security needs with operational stability.
- Vulnerability Relevance: Not all identified vulnerabilities impact every ICS environment. Before considering a patch, evaluate if the vulnerability affects the specific ICS setup. Recent studies indicate that a significant percentage of ICS vulnerabilities don’t directly impact system functionality, reducing the necessity of an immediate patch.
- Downtime Constraints: One of the critical decision points is whether the patch can be applied without downtime. Studies show that over 60% of ICS operators delay patching primarily due to concerns about operational continuity, as unplanned downtime can lead to significant production losses. For industries like energy and manufacturing, even a few minutes of downtime can result in substantial financial impacts.
- Risk Mitigation vs. Operational Needs: The flowchart emphasizes balancing operational needs against security risks. If operational needs outweigh the immediate security risks, compensating controls can be considered instead of direct patching. For example, network segmentation or strict access control might reduce the exploitability of certain vulnerabilities. This aligns with the practice seen across critical infrastructure, where compensating controls are often prioritized over immediate patch deployment.
- Maintenance Windows: Patching during planned maintenance is a common strategy for ICS systems, with around 75% of ICS environments opting for this approach due to the strict uptime requirements. Scheduling patches during these windows allows for necessary updates without disrupting critical processes.
- Documentation and Delayed Patching: If patching is delayed, rigorous documentation is essential. Maintaining a log of vulnerabilities and planned mitigations helps teams stay aware of potential risks and track any shifts in threat levels. Studies show that thorough documentation and delayed patching are effective strategies when paired with regular security assessments.
- Compensating Controls: If a workaround is available or suitable mitigation is in place, patching may not be necessary immediately. This option is crucial for high-risk environments where availability and safety are prioritized. For instance, air-gapping, access restrictions, and real-time monitoring are effective compensating measures that many ICS operators employ to reduce the likelihood of exploitation without applying the patch right away.
Deciding whether or not to patch ICS assets requires careful consideration of both security and operational factors. By following a structured approach, organizations can make informed decisions that balance risk and maintain stability.
You can download the PDF version here: ICS PATCHING PROCESS