Vulnerability Assessment : Active Scanning vs. Passive Scanning
For quite some time, OT engineers and asset owners were horrified by the sound of the “active scan” and quite frankly, they were partially right. No one would dare to scan an OT network the way IT network scans were performed. An active scan could shut down an operation or at least bring down part of the network.
But that is a thing of the past. Even back then, there was a misconception that the “active scan” by the OT vendors is similar to the tools used in the IT. However what they didn’t know was active scans in ICS is not same active scan we have in IT. In IT we use scanners such as Nmap that broadcast addresses by counting the number of ICMP echo replies for each IP address during an ICMP ping sweep and fingerprint the protocols through network port scans.
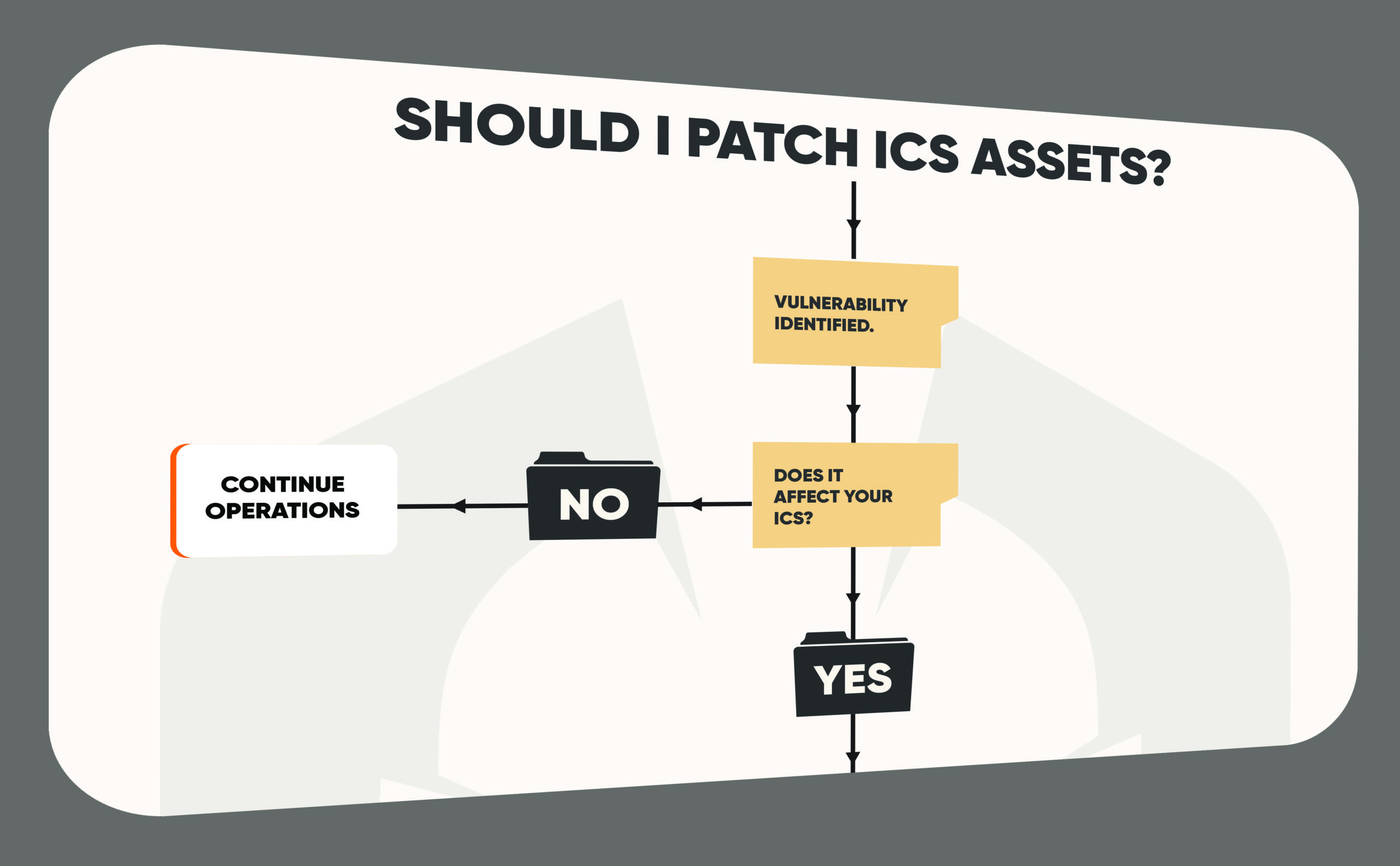
This could be disruptive in an industrial environment. However active scans in ICS environment is not a port scan. It is mostly authenticated scan to query information through SNMP, SSH, WMI, Netbios, etc…and since those are native protocols used by DCS vendors like Siemens, Schneider Electric, Emerson,… it’s safe.
What is an Active Vulnerability Scan?
An active vulnerability scanner sends transmissions of “test traffic” to the nodes or endpoints on the enterprise network. It then examines the responses received from these nodes to assess which node represents a weak point.
Security teams use active scanners to simulate attacks on the network. By using known attacks against one or more selected targets, they try to do what a potential attacker may do to compromise the organization and its resources. The goal is to uncover the security gaps in the network that a hacker could exploit.
Administrators may also use active scanners to examine an enterprise resource after an attack, to understand how an attacker got past existing defenses.
The Benefits of Active Vulnerability Scanners
Active scanners are especially useful when the organization needs constant vigilance to keep threat actors out. These tools provide critical information about devices. This includes basic information such as device name, IP address, and more detailed configuration information such as:
- Device make and model
- Type of installed software apps
- Software version
- Operating system type and patch level
- Firmware type and version
This information gives security admins an overview of ongoing processes and lets them check the health of systems on the entire network.
Some active scanners act autonomously to resolve discovered security issues. For example, they can automatically block potentially dangerous IP addresses or close open ports that may provide an entry point for attackers. They also raise alerts so administrators can take action to close vulnerabilities before bad actors can attack.
The Drawbacks of Active Vulnerability Scanners
One drawback of active scanners is that they are usually programmed to focus on a specific area or to prevent particular situations, such as employees using external media on enterprise devices. Since it’s not easy to customize or extend their core monitoring functionality, these scanners are usually suitable only for specific use cases.
Active scanners send packets directly to network nodes, which can overwhelm networks with high volumes of data traffic. This could affect network speed, performance, uptime, and operations. They may also send incompatible queries that could cause endpoints to malfunction.
Furthermore, active scanners usually don’t monitor networks 24×7, so they may not be able to detect temporary endpoints. Consequently, any vulnerabilities on these endpoints – including logical vulnerabilities like broken access control – can remain undiscovered and leave the door open for malicious actors to attack.
What is a Passive Vulnerability Scanner?
A passive vulnerability scanner watches the network’s traffic flow to collect information about its systems and endpoints. Unlike active scanners, a passive scanner does not directly interact with these systems by sending a probe request or requesting a probe response.
The Benefits of Passive Vulnerability Scanners
Security personnel can use passive vulnerability scanners to:
Understand what is being sent to and from the various endpoints
Monitor in-use operating systems
Monitor various software and their versions
See which services are available and running
Identify parts of the network, including open ports that may be vulnerable to threats
Admins can then reference all this information against a public vulnerability database such as the NVD to understand where vulnerabilities exist. They can also use passive scanners for IT asset management by seeing which assets are in use and identifying shadow IT applications.
A distinct benefit of passive scanners is that they don’t interact directly with endpoints, so they don’t flood the network with test traffic – which means no harm to network performance. Nor do passive scanners disrupt critical processes or cause undesired behaviors like device freezes.
The Drawbacks of Passive Vulnerability Scanners
Passive vulnerability scanning allows you to assess vulnerabilities in your applications, ports, operating systems, and software without interfering with a client or server. The drawback is that this limits the amount of information you collect, so you may not get a complete picture of your vulnerability status.
Also, the scanner must wait for network traffic to or from each endpoint to generate its vulnerability profile, so collecting endpoint data often takes more time.
Finally, while passive scanners can provide information about weaknesses, they can’t act to fix those weaknesses. Your security team must assess each vulnerability and take the necessary actions to remediate or mitigate it.
Active vs. Passive Vulnerability Scanners: Key Differences
The main difference between active and passive scanning methods is in how they operate. Active scanners directly interact with endpoints by querying them with test traffic packets and reviewing each response to find vulnerabilities. Passive scanners “silently” glean network data to detect weaknesses without actively interacting with endpoints.
Another difference is that active scanners generate more detailed data than passive scanners. On the other hand, active scanners usually monitor specific areas or devices, limiting their usability. Moreover, passive scanners can run either nonstop or at specified intervals, while active scanners rarely run 24×7.
Finally, admins can use active scanners to simulate an attack on the enterprise network and understand how a threat actor may attack. They can’t do this with passive monitoring. Also, passive scanners only provide information about weaknesses but don’t resolve them.
Does Your Organization Need Active or Passive Vulnerability Scanners?
The simple answer: Yes.
Active and passive vulnerability scanners are not replacements for each other. Rather, they complement each other.
Each type of scanner has its own strengths and weaknesses. By implementing both types in your vulnerability scanning program, you can combine their strengths and alleviate their weaknesses, giving you a more comprehensive understanding of your security profile.