React Less. Defend More.
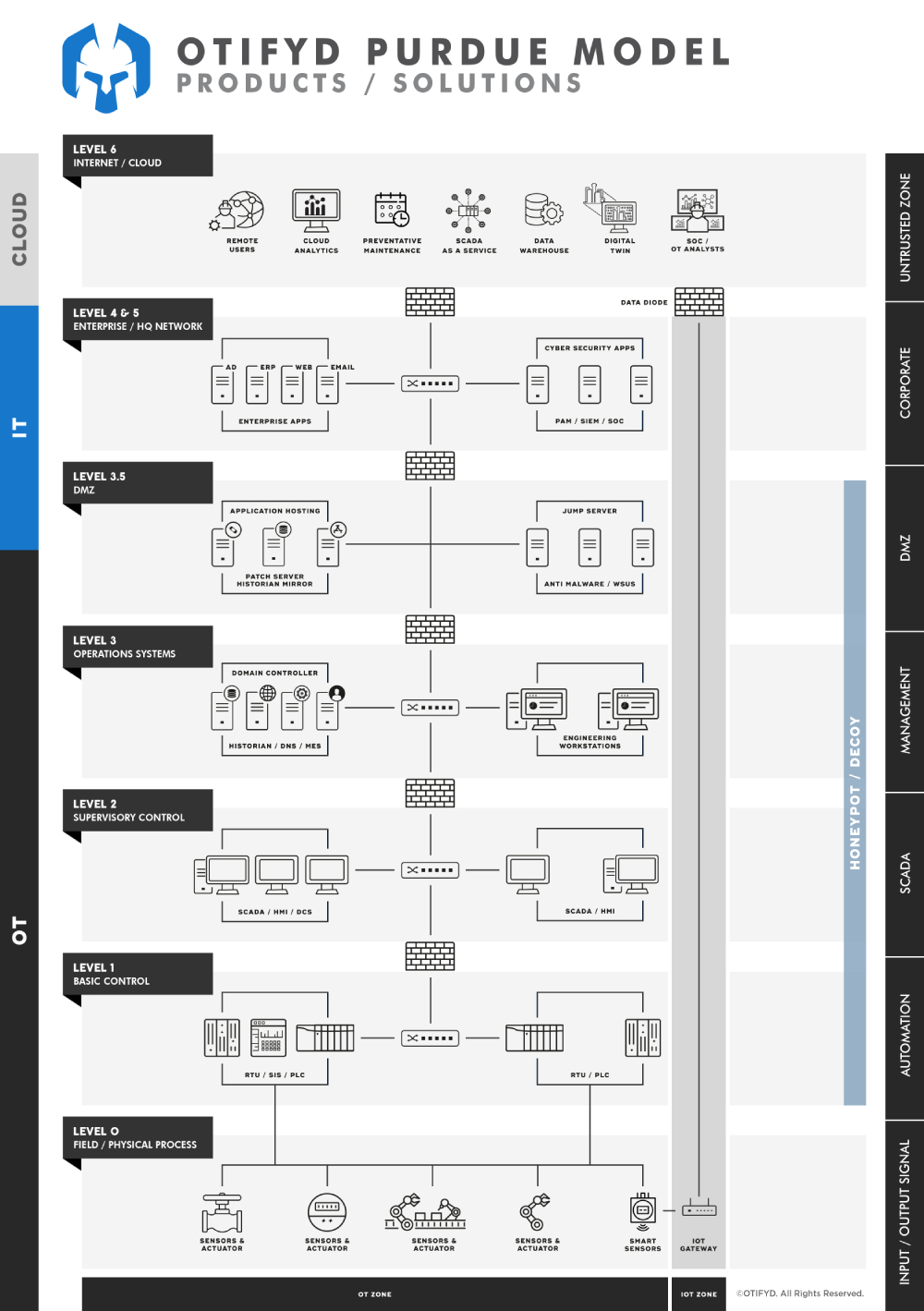
OT sandbox
Run programs, scripts, updates and patches in a safe, isolated environment that mimics your industrial operating environment.
OT Security Sandboxing
Sandboxing is an important security technique used to isolate operating systems (OS) and applications from each other and from the underlying host system. This isolation helps prevent malicious or untrusted code from compromising the security and stability of the system, as well as limiting the potential damage that can be caused by software bugs or other security vulnerabilities.
In the context of industrial control systems (ICS) and operational technology (OT), sandboxing is especially critical due to the critical nature of these systems and the sensitivity of the data they handle. These systems are often responsible for controlling and monitoring physical processes, such as production lines, power grids, and infrastructure systems, and therefore have a direct impact on human safety and the environment.
By using sandboxing techniques, OT systems can create isolated, virtualized environments where untrusted or potentially malicious code can be executed safely without affecting the rest of the system. This helps prevent cyber-attacks and other security incidents from compromising the operation of these systems, and protects against the unintended consequences of bugs or software malfunctions.
In summary, the use of sandboxing in OT systems is essential for maintaining the security, stability, and reliability of these critical systems.
As the name suggests, this isolated test environment functions as a kind of “sandbox,” where you can play with different variables and see how the program works and whether unforeseen consequences are realised. This is also a safe space, where if something goes wrong, it can’t actively harm your host devices or operational environment.
Importance of Sandboxing in OT
Sandboxing is an effective way to improve your organisation’s security since it’s proactive and offers the highest possible threat detection rate. Sandboxing works by keeping potentially malicious programs or unsafe code isolated from the rest of the organisation’s environment. This way, it can be analysed safely, without compromising your operating system or operational environment. If a threat is detected, it can be removed proactively.
- Security: Sandboxing helps isolate potentially malicious code and helps prevent cyber-attacks from compromising the security of industrial networks. This is critical for ensuring the integrity and availability of control systems and the data they handle.
- Stability: Sandboxing helps prevent software bugs or other security vulnerabilities from affecting the stability of industrial networks. This helps ensure that these systems are reliable and operate as intended, even in the presence of bugs or security incidents.
- Containment of incidents: Sandboxing helps contain the impact of security incidents, reducing the potential damage and downtime caused by cyber-attacks or software malfunctions.
- Compliance: Many industrial control systems must comply with industry-specific regulations and standards, such as the IEC 62443 series for industrial control systems. Sandboxing is often a requirement of these regulations, making it an important tool for ensuring compliance.
- Scalability: Sandboxing enables organizations to add new systems and applications to industrial networks without compromising their security or stability. This helps organizations scale their operations and embrace new technologies, while maintaining a high level of security.
- Does not risk your host devices or operational environment. The main advantage of sandboxing is that it prevents your host devices and operating systems from being exposed to potential threats.
- Evaluate potentially malicious software for threats. If you’re working with new vendors or untrusted software sources, you can test new software for threats before implementing it.
- Test software changes before they go live. If you’re developing new code, you can use sandboxing to evaluate it for potential vulnerabilities before it goes live.
- Quarantine zero-day threats. With sandboxing, you can quarantine and eliminate zero-day threats.
- Complement other security strategies. Sandboxing functions as a complementary strategy to your other security products and policies, providing you with even more protection.

On-site Appliance Sandbox
This type of sandbox is a physical device that is installed on-premises. It provides an isolated environment for executing potentially malicious code or for testing software. On-site appliance sandboxes are typically used in industrial control systems and other critical infrastructure environments, as they provide a secure and stable environment that is isolated from the underlying network.This is and ideal deployment mode for organisations that want to stay away from the cloud and the internet.
Cloud Base Sandbox
This type of sandbox is hosted in a cloud environment and provides a remote, isolated environment for executing code or testing software. Cloud-based sandboxes are often used by organizations that need to run applications in multiple locations, as they provide a flexible and scalable solution that can be accessed from anywhere with an internet connection.You can send files using your existing security gateway or Exchange server, with no further infrastructure changes necessary on your end.
Software Base Sandbox
This type of sandbox is a software-only solution that runs on a local machine or server. It provides an isolated environment for executing code or testing software, but relies on the underlying system to provide the necessary resources and security. Software-based sandboxes are often used for testing and development purposes, as they provide a convenient and cost-effective solution for isolating code. Upload suspicious files at any time for analysis by emulation service. Sandboxing software technology automatically analyzes the file and generates a detailed report that includes a wealth of forensic information such as malware family, targeted geography, MITRE ATT&CK techniques, emulation videos and dropped files.
What is an OT sandbox?
An OT (Operational Technology) sandbox is a virtual environment that simulates a real-world OT system to allow for testing, experimentation, and vulnerability assessment without risking damage to the actual system.
How does an ICS Sandbox work?
A sandbox works by creating a controlled and isolated environment for executing code or running applications. This environment is designed to prevent potentially malicious code or software bugs from affecting the stability or security of the underlying system.
In a typical sandbox, the code or application runs in a separate environment that is isolated from the rest of the system. This environment is designed to limit the resources and access that the code has, which helps prevent it from compromising the stability or security of the system.
What are the benefits of using an OT sandbox?
An OT sandbox provides a safe environment for testing and experimentation, allowing organisations to identify and address potential vulnerabilities in their OT systems without risking damage to the actual system. It also enables organisations to develop and test new protocols, configurations, and updates before deploying them to the live environment.
Why should we use an Sandbox in our OT network?
There are several reasons why it’s a good idea to use a sandbox in an operational technology (OT) network:
Improved security: Sandboxing helps prevent malware and other malicious code from compromising the security of an OT network. By isolating potentially malicious code in a controlled environment, a sandbox can help contain the impact of security incidents and prevent them from spreading throughout the network.
Enhanced stability: Sandboxing can help prevent software bugs and other stability issues from affecting the operation of an OT network. By isolating applications or services in a controlled environment, a sandbox can help ensure that the network remains stable and operational, even in the event of a software failure or bug.
Increased visibility: Sandboxing can provide enhanced visibility into the behavior of applications or services within an OT network. By monitoring the behavior of code in a controlled environment, a sandbox can provide valuable insights into the operation of the network and help identify any potential security or stability issues.
Eased testing: Sandboxing can make it easier to test new software or code within an OT network. By providing a controlled and isolated environment for testing, a sandbox can help reduce the risk of introducing new software or code into the network and help ensure that the network remains stable and secure.
What are some examples of OT systems that can be simulated in an OT sandbox?
Examples of OT systems that can be simulated in an OT sandbox include supervisory control and data acquisition (SCADA) systems, industrial control systems (ICS), programmable logic controllers (PLCs), and distributed control systems (DCS).
Who uses OT sandboxes?
OT sandboxes are used by organisations that operate OT systems, including critical infrastructure providers such as power plants, water treatment facilities, and transportation systems. They are also used by cybersecurity professionals and researchers to test and develop new security protocols and tools.
How do I set up an OT sandbox?
Setting up an OT sandbox requires specialized knowledge and expertise in both OT systems and cybersecurity. It typically involves creating a virtual environment that replicates the configuration and behaviour of the actual OT system, installing software and tools for testing and experimentation, and implementing security measures to prevent unauthorised access.
What are some best practices for using an OT sandbox?
Some best practices for using an OT sandbox include limiting access to authorised personnel, using realistic scenarios and data, keeping the sandbox up-to-date with the latest software and security patches, and monitoring the sandbox for suspicious activity. It is also important to have a clear understanding of the goals and objectives of the testing and experimentation, and to document and analyse the results.
