React Less. Defend More.
Electrical Signal
ot Monitoring
Monitor the deepest level of your OT network with an out-of-band detection solution, undetectable by hackers
Electrical Signal
n an operational technology (OT) environment, monitors are used to monitor and collect data from electrical signals that are generated by various devices and systems. These monitors are used to help ensure the safe and efficient functioning of critical systems, such as power plants, oil and gas pipelines, and water treatment facilities. They are designed to detect and alert operators to any potential problems or anomalies in the electrical signals that they are monitoring, allowing them to take proactive measures to avoid equipment damage or safety incidents.
OT monitors typically use sensors and other types of monitoring devices to detect and measure electrical signals, such as voltage, current, power, and energy. They can also use communication protocols, such as Modbus and DNP3, to communicate with other devices and systems in the network, allowing for the collection and analysis of data from multiple sources. The data collected by these monitors is used to create detailed reports and visualizations, providing operators with valuable insights into the performance and status of the systems they are monitoring.
OT monitors play a critical role in ensuring the safe and efficient operation of critical systems, and are a key component in many industries where electrical signals are central to the functioning of essential systems.
How electrical signal monitoring complements network anomaly detection?
Electrical signal monitoring and network anomaly detection are complementary technologies that work together to ensure the safe and efficient operation of critical systems.
Electrical signal monitoring is used to monitor and collect data from electrical signals that are generated by various devices and systems. This data can include information about voltage, current, power, and energy, among other metrics. The data collected by electrical signal monitors provides operators with valuable insights into the performance and status of their systems.
Network anomaly detection, on the other hand, is used to identify unusual or unexpected behavior in a network. This can include detecting malicious activity, such as cyber attacks, as well as identifying performance issues, such as network congestion or component failures.
By combining the data collected from electrical signal monitoring with the data generated by network anomaly detection systems, operators can gain a more complete understanding of the health and performance of their critical systems. This can help them to quickly identify and respond to potential problems, allowing them to prevent equipment damage, safety incidents, and other types of disruptions.
In summary, electrical signal monitoring and network anomaly detection work together to provide operators with a comprehensive view of the performance and status of their critical systems, helping to ensure their safe and efficient operation.
Does SIGA (Signal Intrusion Detection and Assessment) replace Intrusion Detection System?
SIGA (Signal Intrusion Detection and Assessment) is a technology used to detect and assess electrical signal intrusion in electrical systems. It helps to detect unauthorised access or tampering in the electrical system by analysing the signals present in the electrical network. The technology uses algorithms to analyse the signals and identify any anomalies or deviations that could indicate a potential attack.
If an intrusion is detected, the SIGA system can then trigger an alarm or other appropriate response to alert the relevant authorities. This helps to prevent malicious actors from accessing sensitive information or causing damage to the electrical system. Additionally, the SIGA system can provide detailed information about the intrusion, such as the location and type of attack, which can help organizations respond more effectively.
In summary, the SIGA electrical signal technology can help detect attacks by continuously monitoring the electrical signals in a system and alerting authorities of any anomalies or deviations that may indicate an intrusion. SIGA does not replace Intrusion Detection Systems or Anomaly Detection solutions, it complements them.
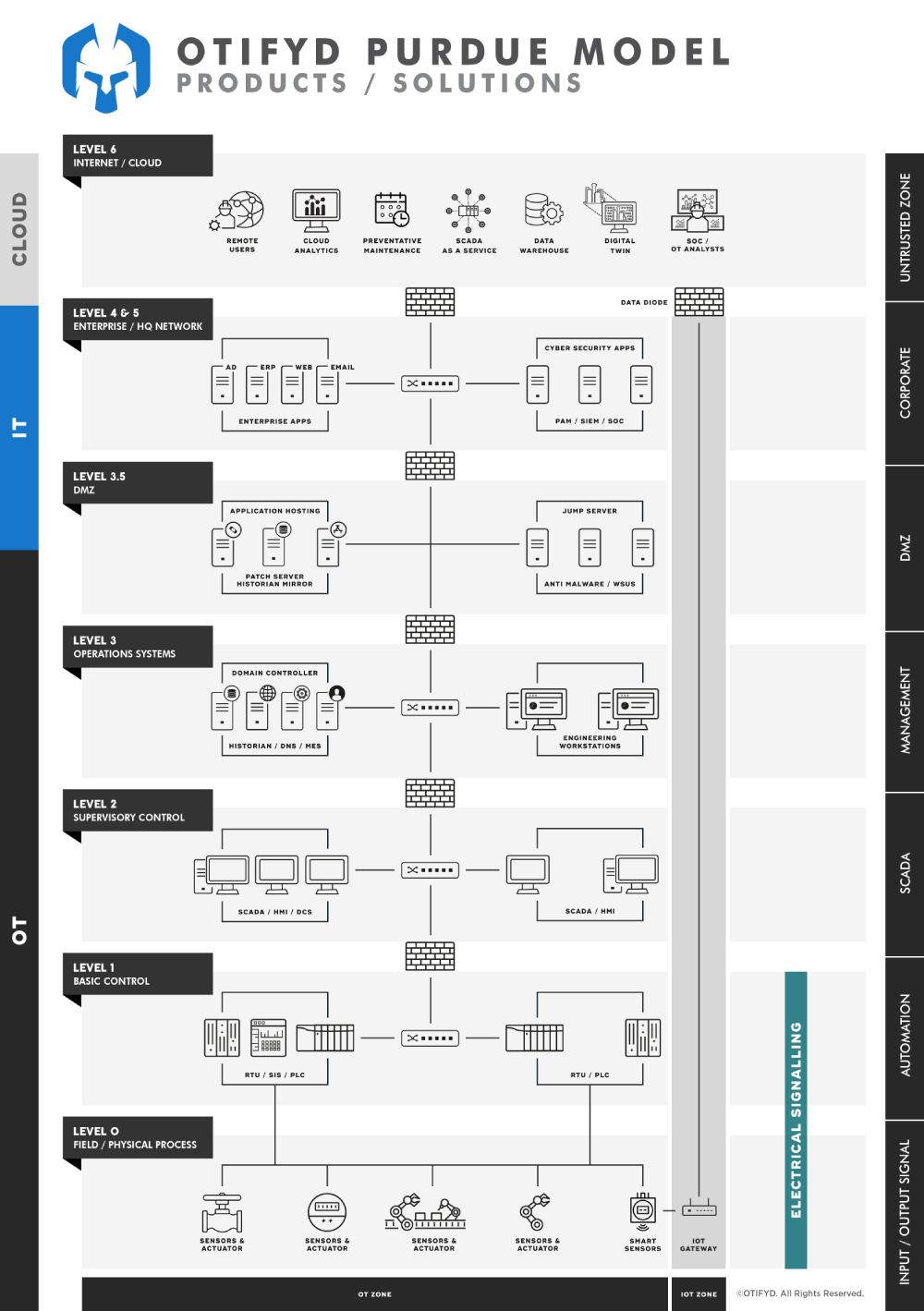
Which level of Purdue model is associated with SIGA?
The SIGA technology is typically associated with the Physical Layer layer 1 and layer 0 of the Purdue Model.
The Physical Layer is responsible for transmitting the raw bit stream over the physical medium, such as a network cable. The SIGA technology monitors the electrical signals that are transmitted over the physical medium and analyzes them for any anomalies or deviations that could indicate a potential attack.
By working at the Physical Layer, SIGA provides a unique layer of security for electrical systems, helping to prevent unauthorised access or tampering. By monitoring the physical signals, SIGA can detect intrusions that might go unnoticed by other security measures that work at higher layers of the Purdue Model, such as firewalls or intrusion detection systems.
How SIGA benefits from connecting via an out-of-band network?
An out-of-band network is a separate network that is used for monitoring and control purposes, separate from the main network that is used for normal operation. This type of network has several benefits:
Security: An out-of-band network provides an additional layer of security for the main network. The off-band network is used for administrative and monitoring purposes, and is typically not connected to the internet or other external networks. This reduces the risk of external threats or attacks compromising the main network.
Reliability: An out-of-band network can help to increase the reliability of the main network. If the main network fails or experiences issues, the off-band network can be used to monitor the system and diagnose the problem.
Network Separation: An out-of-band network provides a separate network for administrative and monitoring purposes, which can help to reduce network congestion and improve network performance.
Remote Access: An out-of-band network can be used to provide remote access to the main network, allowing administrators to monitor and control the network from a remote location.
Network Management: An out-of-band network can help to improve network management by providing a separate network for monitoring and control purposes, which can help to reduce network downtime and improve overall network performance.
What is SIGA?
SIGA stands for Signal Intrusion Detection and Assessment. It is a technology used to detect and assess electrical signal intrusion in electrical systems.
How does SIGA work?
SIGA works by continuously monitoring the electrical signals in a system and analysing them for any anomalies or deviations that could indicate a potential attack. If an intrusion is detected, the SIGA system can then trigger an alarm or other appropriate response to alert the relevant authorities.
Where is SIGA used?
SIGA is used in a variety of electrical systems, including critical infrastructure systems, industrial control systems, and other types of electrical networks.
What are the benefits of SIGA?
The benefits of SIGA include increased security, improved reliability, and enhanced network management. SIGA helps to prevent unauthorised access or tampering in electrical systems, and can provide detailed information about potential intrusions to help organizations respond more effectively.
How does SIGA differ from other security measures?
SIGA differs from other security measures, such as firewalls or intrusion detection systems, by working at the Physical Layer of the network. By monitoring the physical signals in an electrical system, SIGA can detect intrusions that might go unnoticed by other security measures that work at higher layers of the network.
How SIGA can stop HMI Spoofing?
HMI spoofing is a type of cyber attack where an attacker creates a fake human-machine interface (HMI) to deceive operators into thinking that they are interacting with the legitimate HMI.
To prevent HMI spoofing, SIGA can detect cyberattacks from the electrical signals between the PLC (Level 1) and (Level 0) I/O.
