React Less. Defend More.
OT Penetration Testing
Evaluate the security of your OT environment from a hacker’s perspective to identify exploitable vulnerabilities and blind spots.
OT Penetration Testing Overview
Operational technology (OT) systems are the backbone of critical infrastructures such as power grids, water treatment plants, and transportation systems. As these systems become increasingly connected and digitised, they become more vulnerable to cyber-attacks. This is where OT penetration testing comes in.
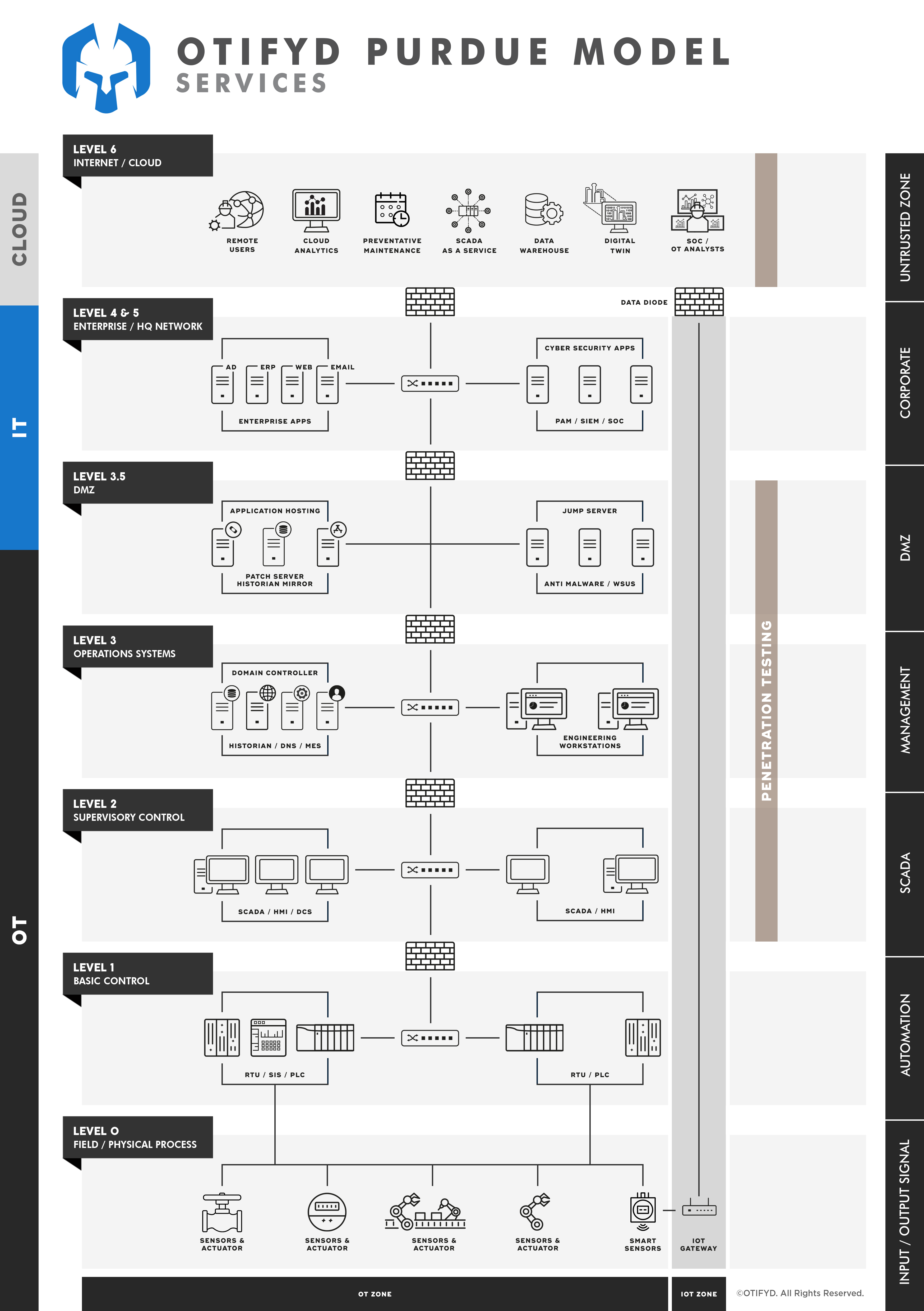
OT penetration testing is a process that involves simulating a cyber attack on an OT environment / Industrial Control System (ICS) to identify vulnerabilities and weaknesses in the system’s security. This process is critical in identifying potential entry points for malicious hackers and protecting against attacks.
To perform an OT Penetration Test, a penetration tester will typically use non-intrusive penetration testing techniques to identify potential vulnerabilities in the OT network. These techniques can include vulnerability scanning, network mapping, and analysis of network traffic.
OT Penetration Testing can also involve more intrusive techniques, such as attempting to exploit vulnerabilities discovered during the initial assessment. This allows the penetration tester to demonstrate the potential impact of an attack and provide recommendations for improving the security of the OT environment.
The goal of OT Penetration Testing is to identify weaknesses in the OT environment system’s security before malicious hackers can exploit them. This can include vulnerabilities in the software and hardware used, as well as potential weaknesses in the network architecture and configuration.
Offensive security is another critical component of OT Penetration Testing. A penetration tester will use offensive security techniques to test the effectiveness of the organisation’s security controls and identify potential gaps that could also be exploited by hackers.
Organisations should conduct regular Penetration Testing of their OT environment for the following key reasons:
- To identify weaknesses in infrastructure (hardware), application (software) and people (process) in order to develop remedial controls;
- To ensure implemented security controls are effective, this provides assurance to security teams, senior management and stakeholders that security posture is maintained;
- To discover new bugs in existing software as patching and updates can fix existing vulnerabilities, but they can also introduce new vulnerabilities;
- When appropriately performed, OT Penetration Testing goes beyond merely stopping malicious threat actors from unauthorised access to a company’s OT assets and environment. It creates real-world scenarios that show organisations how well their current defences would fare when confronted with a full-scale cyber attack.
Why Conduct OT Penetration Testing?
Organisations should conduct regular Penetration Testing of their OT environment for the following key reasons:
- To identify weaknesses in infrastructure (hardware), application (software) and people (process) in order to develop remedial controls;
- To ensure implemented security controls are effective, this provides assurance to security teams, senior management and stakeholders that security posture is maintained;
- To discover new bugs in existing software as patching and updates can fix existing vulnerabilities, but they can also introduce new vulnerabilities;
- When appropriately performed, OT Penetration Testing goes beyond merely stopping malicious threat actors from unauthorised access to a company’s OT assets and environment. It creates real-world scenarios that show organisations how well their current defences would fare when confronted with a full-scale cyber attack.
Key Benefits from OT Penetration Testing
- Understanding how successful hackers would be against the protections and mitigations built into your OT environment.
- Understanding what type of operational impacts may result from compromise;
- Understand the applicable types of attacks which may be targeted at your OT assets;
- An in-depth technical exploration, analysis and test of your OT assets and network security posture;
- Identify and prioritise risks that may impact critical OT assets.
We always prioritise “Availability” when it comes to OT Penetration Testing. As such, appropriate precautions are always taken accompanied by a testing strategy that is thoroughly detailed and agreed upon. This ensures our testing remains comprehensive and valid without disrupting your operations.
Deliverables from out OT Penetration Testing and Standards Used
This service offering scope and depth are tailored to your specific needs. Typical assessments conducted are :
- Internal Penetration Test: Imitates an insider threat and identifies how an attacker with internal access may compromise or damage the network, systems, or data.
- External Penetration Test: Designed to discover and exploit vulnerabilities in hosts accessible via networks external of the OT environment (e.g. IT, Internet).
- Application Penetration Test: Simulates attacks on a system in an attempt to gain unauthorised access.
- Wireless Penetration Test: Identifies vulnerabilities in your wireless infrastructure.
The results of the assessment activities are documented within a formalised report that includes:
- Assessment methodology;
- Executive summary;
- Detailed technical analysis and remediation recommendations;
- Identified security vulnerabilities classified according to potential impact and the likelihood of exploitation.
All our OT penetration tests are conducted based on best practices set by the following standards:
- NIST SP 800-82: Guide to Industrial Control Systems (ICS) Security
- ISA/IEC 62443 Cybersecurity for Industrial Automation and Control Systems
- NIST Cybersecurity Framework (CSF)
- ISO/IEC 27001: Information security management systems
- OWASP Top 10 for ICS Security
- SANS Institute Top 20 Critical Security Controls for Effective Cyber Defense
- ENISA (European Union Agency for Cybersecurity) Good Practices for Industrial Control Systems Security CIS Controls for OT Security
- FERC (Federal Energy Regulatory Commission) Cyber Security and Physical Security Standards.
What is a Penetration Test?
A penetration test, or “pentest” for short, is a security assessment that simulates an attack by a malicious party on a network or application in order to identify security flaws.
What is OT Penetration Testing?
OT Penetration Testing is a process of simulating a cyber attack on an OT / industrial control system (ICS) to identify vulnerabilities and weaknesses in the system’s security. This helps organisations to identify potential entry points for malicious hackers and protect against operational technology attacks.
Why is OT Penetration Testing Important?
OT Penetration Testing is critical in identifying potential vulnerabilities and weaknesses in the security of an industrial control system. As these systems become increasingly connected and digitised, they become more vulnerable to cyber-attacks. Penetration testing helps organisations to identify potential entry points for hackers and protect against cyber attacks.
Why Do I Need a Penetration Test?
A penetration test helps reduce risk exposure to consequences including health and safety impact, financial loss and repulational damage, resulting from a breach. Having a window into the mind of an attacker, a penetration test helps to uncover targets of opportunity, the path of least resistance, and technical vulnerabilities that, if exploited, may result in any of the above consequences.
When Do I Need a Pen Test? How Often Should I Conduct One?
We recommend Organisations to get to the point where they use penetration testing as a security best practice. In other words there is already a foundational level of cyber security risk management in place with associated controls being followed. An organisation with no cyber risk management in place would benefit more from conducting foundational risk management activities first opposed to a penetration test.
Pen testing is a good way to check the security of your internal processes too; from IT to OT engineering –you can make sure that departments are communicating and doing their jobs effectively, and that the “business as usual” cyber processes are working.
Other reasons you might need a penetration test: if you’re making major changes to your networks, installing new hardware like firewalls or servers with new operating systems in critical zones, reorganising your whole network, adding new zones, moving to a new data centre, or transferring data storage to a cloud.
It’s a good idea to periodically test any environment that contains critical production systems with a penetration test. If you’re changing software or adding new features, it may be a good time to do an application penetration test.
How Often Should an Organisation Conduct OT Penetration Testing?
The frequency of OT Penetration Testing will depend on various factors such as the size and complexity of the OT environment, the rate of change in the network, and the regulatory requirements. It is recommended that organisations conduct regular assessments of their OT environment and perform OT penetration testing at least annually to maintain the security of their critical infrastructure.
What are the Different Techniques Used in OT Penetration Testing?
OT Penetration Testing techniques can include vulnerability scanning, network mapping, analysis of network traffic, and attempting to exploit vulnerabilities discovered during the initial assessment. A penetration tester will typically use non-intrusive techniques to identify potential vulnerabilities in an OT environment.
What is the Difference Between a Pentest and a Vulnerability Assessment Scan?
There are a couple of big differences. First, a Vulnerability Assessment (VA) scan is an automated test. A penetration test is performed by qualified individuals that actually dig into the complexities of your network environment and actively try to exploit any vulnerabilities that they may discover.
A VA scan typically only identifies vulnerabilities at a high level, the scan is not intended to exploit vulnerabilities, and produces an indication report. A pentester will dig deeper and attempt to identify root causes of vulnerabilities; they use their experience and creativity to gain access to systems and extract sensitive data.
One way to think about the difference between pen tests and VA scans is that VA scans are meant to regularly and quickly give you high-level insights into your network, while pentests go to a deeper level of security testing and are typically performed less often.
How Does Penetration Testing Improve Security in My Company?
Penetration testing helps prioritise investments in your OT Security Program. Penetration testing is practical and helps understand the impact of each missing or ineffective control within your business.
What are the Benefits of OT Penetration Testing?
The benefits of OT Penetration Testing include identifying vulnerabilities in the OT network, understanding the potential impact of an attack, and providing recommendations for improving the security of the OT environment. This helps organisations to strengthen their security posture, protect against operational technology attacks, and maintain the integrity of their critical infrastructure.
What Do I Need to Know Before a Pentest?
To prepare for a pentest, you will need to answer some important questions: what is my motivation? What do I really want to find out? What are my compliance requirements? These answers will help us know how to approach the testing.
Do you just want to know that you’re secure for your own peace of mind? Do you want to improve and evaluate your security posture? Do you need to increase security awareness for upper management in your company? Perhaps you want to justify spending for security expenses. Do you want to identify your controls and have confidence that they are working? Perhaps you are having a lot of security incidents and you want to reduce the frequency and the impact of those incidents.