React Less. Defend More.
OT Vulnerability assessment
Understand the strengths and weaknesses of your OT security posture across people, processes and technology.
OT Vulnerability Assessment Overview
OTIFYD offers a comprehensive vulnerability assessment service that accurately identifies cyber security vulnerabilities for your Operational Technology (OT) environment. Our OT Security Vulnerability assessment service includes:
- Identification and evaluation of current (as-is) controls;
- Identification and evaluation of gaps and vulnerabilities;
- Identification and evaluation of additional mitigating controls;
- Risk rating, prioritisation and remedial recommendations;
- Formalised assessment report.
Our assessments are “outcome-focused” which means any remedial recommendations proposed are aimed at providing tangible risk reduction. This approach helps organisations justify OT cyber security improvements and the associated costs by being armed with better information and understanding of the “What, Why and How?”
Finally, our assessments are conducted according to industry best practices and standards/frameworks such as ISO/IEC 62443, ISO/IEC 27001, NIST and ISF but can also be tailored to your specific needs.
Why Conduct an OT Security Vulnerability Assessment?
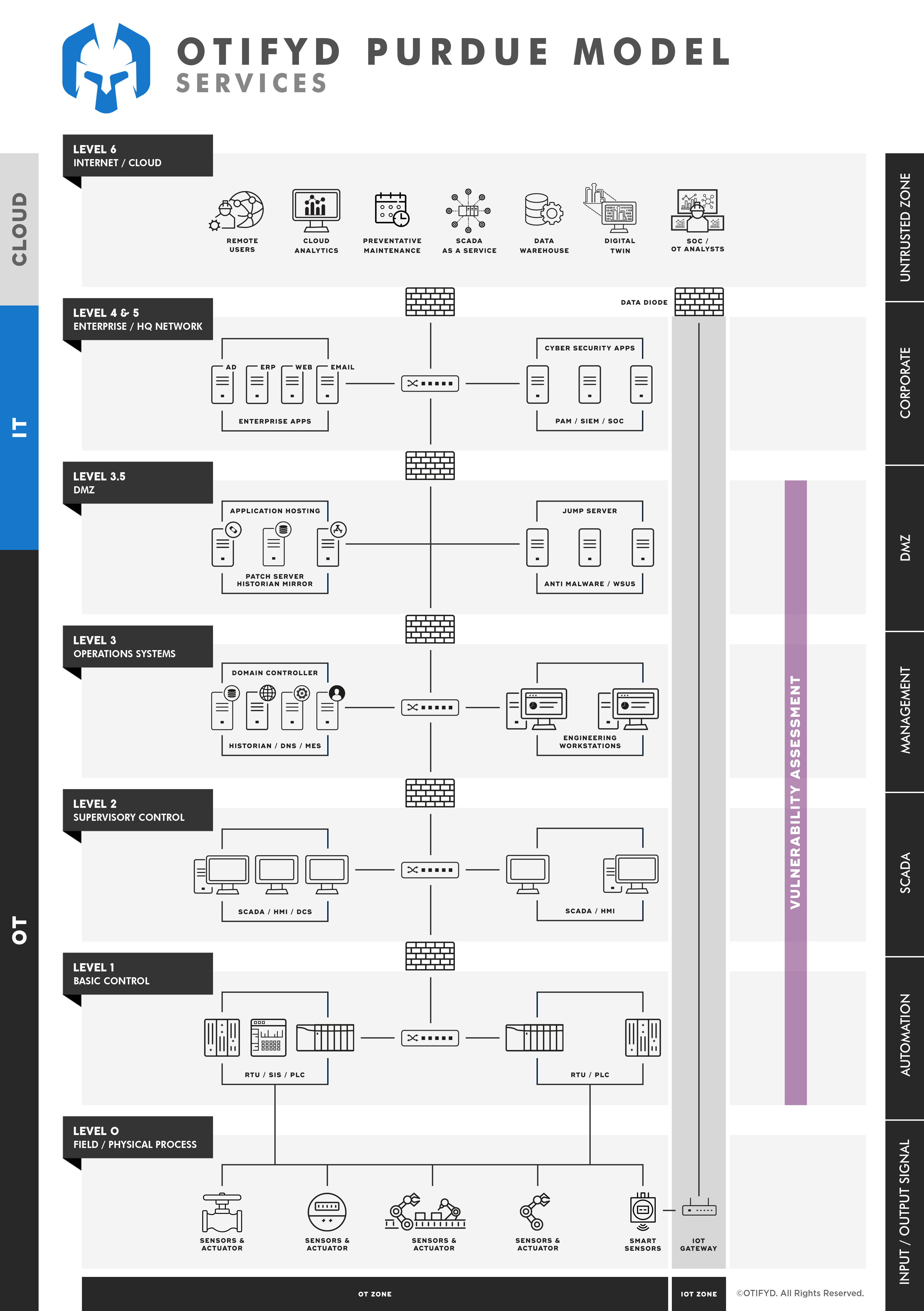
At a high level, this assessment builds a structured snapshot (“as-is”) of the cyber-security posture for your Operational Technology (OT) environment. The snapshot contains risk-based analysis and details the strengths and weaknesses of your OT security posture across people, processes and technology practice areas. Also included are prioritised tactical and strategic recommendations targeted at reducing the risk exposure identified. The assessment methodology and data gathering process leverage our experience, threat intelligence, OT cyber security industry best practices and automated tooling.
Why is an "OT" Specific Vulnerability Assessment Necessary?
Traditional IT information security models prioritise Confidentiality, then Integrity and lastly Availability (commonly known as the “CIA Triad”), whereas OT cyber security models prioritise Availability, then Integrity and lastly Confidentiality (commonly known as the “AIC Triad”).
This is because the assets and systems that make up an OT environment (e.g. manufacturing plant, upstream oil asset etc) rely heavily on being available and their integrity dependable for both process control and safeguarding. In some cases, the loss of availability or system integrity could jeopardise the safety of the workforce, consumers, physical assets and the environment. Depending on the type and length of availability loss, this can result in economic, ecological, and life-threatening situations. Examples of availability attacks include the 2021 Colonial Pipeline attack, the 2019 Springhill Memorial Hospital ransomware attack, and the 2015 Sandworm attacks on Ukrainian critical infrastructure.
These differences between IT and OT environments should be considered to correctly assess risks and propose appropriate countermeasures, hence why an OT-specific risk assessment is necessary.
Key Benefits of Conducting an OT Security Vulnerability Assessment
- A comprehensive understanding (baseline) of current OT Security posture and risk exposure.
- Determination of improvements to reduce both attack surface and risk over the short, mid and long-term.
- Identifies gaps covering People, Process and Technology which aids prioritise high-risk areas for remediation and / or improvement.
- Provides supporting information to make informed decisions in relation to cyber security investment.
- Non-intrusive assessment methods.
- Swift execution.
Deliverables from our OT Security Vulnerability Assessment
As part of this service offering, OTIFYD delivers a formalised report that includes:
- Assessment methodology;
- Executive summary;
- Description of the current situation and risk exposure;
- Assessment findings and observations;
- Remediation recommendations with associated priorities.
Additionally, the following items will also be provided:
- High-level presentation for executive-level stakeholders.
What is OT Vulnerability Management?
OT (Operational Technology) Vulnerability Management refers to the process of identifying, evaluating, and addressing vulnerabilities in OT systems and networks. OT systems are those that control and monitor physical processes, such as manufacturing plants, power grids, and transportation systems.
OT vulnerability management involves several steps, including:
Asset Inventory: The first step is to identify and inventory all assets within the OT environment, including hardware, software, and network devices.
Vulnerability Scanning: Once assets are identified, the next step is to scan them for known vulnerabilities. Vulnerability scanners are automated tools that can identify security weaknesses in systems and applications.
Risk Assessment: The vulnerabilities identified during scanning are then assessed to determine their impact on the OT environment. This includes evaluating the likelihood of exploitation and the potential consequences of a successful attack.
Remediation: Once vulnerabilities have been identified and assessed, a plan is developed to remediate them. This may involve applying software patches, reconfiguring systems, or implementing additional security controls.
Monitoring: Finally, the OT environment is continuously monitored for new vulnerabilities and potential threats, and the vulnerability management process is repeated on a regular basis to ensure ongoing security.
Effective OT vulnerability management is critical to ensure the safety, reliability, and resilience of critical infrastructure systems.
What is a Vulnerability?
In the context of an OT asset, a vulnerability is a system weakness that, if exploited, will result in a breach of system integrity, which could then lead to system malfunction.
What is Security Posture?
The security status of an organisation’s OT networks, systems and data based on information security resources (e.g., people, hardware, software, policies) and capabilities in place to manage the defence of the enterprise and to react as the situation changes.
What are Mitigating Controls?
Mitigating controls are methods used to reduce the overall impact of a threat. The mitigating controls are therefore assigned to appropriate threats.
What does "Outcome Focused" Approach Mean?
Adopting an outcomes-focused approach means orienting your organisation to achieve outcomes, in other words, the results of your activities. A focus on outcomes helps organisations also prove to stakeholders that what they are doing is working.
What is Risk Exposure?
Risk exposure is the probability of loss resulting from a cyber attack or cyber incident. Risk exposure is typically expressed as Low, Medium and High.