React Less. Defend More.
OT Network Segmentation
Enhance security by segregating and segmenting OT networks into trusted and untrusted zones and stopping attacks from propagating throughout your industrial control system networks.
OT Network Segmentation Overview
Network segmentation is an architectural approach that divides a network up into multiple segments (also referred to as “subnets”), each acting as its own small network. This enables the flow of traffic between segments to be based on specifically configured policies (also known as “firewall rules”). Organisations use segmentation to improve monitoring, boost performance, localise technical issues and – most importantly – enhance security.
Many Operational Technology (OT) networks in use today were constructed in the so-called “air gap” era when security was deemed adequate due to the inherent isolation from other company IT systems and the internet. With this in mind, many OT assets are considered “insecure by design” by default as security was not really considered. But malicious threat actors also know this and are continuing to take advantage of vulnerabilities in OT assets made possible through digital transformation, increased connectivity and continued IT and OT convergence. Attacks also show no sign of slowing down. Recent research by a renowned security firm identified almost 100% more new ransomware variants in the first half of 2022 than in the previous six-month period.
Why Deploy OT Network Segmentation?
Network segmentation is one approach organisations should consider to help address unauthorised access and ransomware cyber threats. When deployed in OT environments, network segmentation provides a powerful tool with which to prevent unauthorised traffic flows and access to critical OT assets and valuable data such as Safety Instrumented Systems (SIS), Distributed Control Systems (DCS), Supervisory Controls and Data Acquisition (SCADA) systems and the so-called “crown jewels” data repositories (e.g. proprietary recipes, trade secret information, manufacturing data etc).
Network segmentation provides layers of both physical and logical security to an OT environment. This is achieved by cordoning off the multiple networks that make up an OT environment from one another (known as security zoning), and also from other external networks such as corporate IT, third-party and other manufacturing networks (e.g. plant-to-plant connectivity).
Our Network Segmentation service’s primary aim is to enhance security by stopping attacks from propagating throughout an OT network and penetrating vulnerable assets. Effective network segmentation prevents malware from spreading into other assets, systems and networks. Network segmentation also lessens network congestion, improving overall network performance and reducing performance degradation. This is crucial for critical OT systems and resource-intensive processes found in manufacturing plants, power generation plants, water treatment facilities, oil rigs and other industrial settings.
Due to the possibility of unintentionally affecting a live production process, implementing network segmentation can be particularly challenging for OT environments. Temporarily losing an asset may not always have much of an effect on company operations in an IT context, but an asset going offline can have serious negative effects in an OT environment. Another complexity arises when segmenting an OT environment with assets from many vendors with different network designs, IP subnets and bespoke requirements for their protocols and services to function correctly. However, with the right tools, experience, technologies and processes in place, it’s absolutely possible to successfully segment and secure your OT environment.
NIST 800-53 and OT Network Segmentation Summary:
NIST 800-53 is a cybersecurity framework published by the National Institute of Standards and Technology (NIST) that provides guidelines and best practices for securing federal information systems and networks. Network segmentation is an important aspect of NIST 800-53 and is recommended as a way to limit the impact of cyberattacks or other security incidents.
According to NIST 800-53, network segmentation involves dividing a network into smaller, isolated subnetworks or zones, each with its own set of security controls. This can help limit the spread of cyberattacks or other security incidents by restricting the ability of attackers to move laterally within the network. NIST 800-53 recommends that organisations use network segmentation to protect their most critical assets and systems, and to apply the principle of least privilege when designing their security policies.
NIST 800-53 also provides specific security controls that organisations should implement to support network segmentation, including access controls, firewalls, intrusion detection and prevention systems (IDS/IPS), and network-based authentication mechanisms. Organisations are also encouraged to regularly monitor and audit their network segmentation controls to ensure that they are functioning properly and effectively mitigating security risks.
Key Benefits from OT Network Segmentation
- Slowing Down Attackers: One of the biggest benefits of effective network segmentation is that it can buy you extra time during a cyber attack or security incident. If an attacker successfully breaches your OT environment directly from within the network or indirectly via a connected IT network, and the OT environment is segmented, then it will take extra time for the attacker to break out of that segmented portion of the network to get at other assets, data or resources they really want.
- Enabling Policy of Least Privilege: Having strong network segmentation makes it easier to restrict user access to your most critical OT assets and data. This can be invaluable for protecting OT assets if a user’s access credentials are compromised or abused. In other words, network segmentation helps you to protect your business against insider attacks, including misuse, as well as attacks by malicious outsiders.
- Reducing Damage from Successful Attacks: Because strong network segmentation can help restrain attackers from breaking out of a network before you’ve contained the breach and cut off their access, this in turn can help to minimise the damage caused by such breaches. There’s a world of difference between the time, money, and effort it takes to recover from a breach where the attacker was only able to compromise a small number of OT workstations and a breach involving many OT assets and systems across your entire OT environment.
- Increasing Overall Data Security: By segmenting networks, it becomes easier to protect your most valuable OT data (e.g. regulatory, compliance, batch data etc). The creation of a layer of separation between servers containing sensitive data and everything outside of your OT environment can do wonders to reduce your risk of data loss or theft.
- Improved Network Performance: Rather than having all OT assets able to talk to one another on one big flat network regardless of their function and business criticality, network segmentation allows traffic flows to be controlled to a granular level. This enables critical OT assets and their associated data connectivity traffic profiles to be segmented separately and enclosed within smaller logical networks, reducing network congestion and aiding system performance and reliability.
Deliverables from our OT Network Segmentation Service
Our OT Network Segmentation service typically delivers the following:
- Comprehensive network architecture discovery and analysis
- Security zones and conduit diagram creation
- Logical and physical network architecture diagrams creation that represent current and target architecture
- Logical segmentation proposal, including IP subnetting and VLAN plans
- Tactical and strategic recommendations, including technology solution consideration
What is OT Network Segmentation?
OT network segmentation is the process of dividing an OT network into smaller, isolated subnetworks or zones, each with its own set of security controls, to improve overall network security.
What are the Main Purposes of Network Segmentation?
- Limiting access privileges to those who truly need it.
- Protecting the network from widespread cyberattacks.
- Boosting network performance by reducing the number of hosts and users in specific zones.
Why is Network Segmentation Important for Cybersecurity?
OT network segmentation is particularly important because it helps limit the spread of cyberattacks or other security incidents that might compromise the network’s availability, confidentiality, or integrity.By segmenting networks, it becomes easier to protect your critical OT systems and data. The creation of a layer of separation between servers used by critical OT systems, other systems and everything outside of your network can do wonders to reduce your risk of production shutdown or data loss or theft.
What are the Types of Network Segmentation?
There are two types of network segmentation: Physical and Virtual.
Physical segmentation uses dedicated hardware to build segments. While physical segmentation is the most secure method, it is also the most difficult to manage.
Virtual network segmentation covers the entire network, not just at the perimeter. Switches manage the virtual local area network environment, and firewalls are shared, reducing the required hardware.
What are the Benefits of Network Segmentation?
Overall, network segmentation’s major benefit is in the area of security, with manageability and performance also a consideration. Network segmentation by virtualisation increases security in several ways, including the following:
- Better isolation;
- Better containment;
- Better access control;
- Improved monitoring;
- Reduced complexity;
- Easier management.
What are the Risks of Unsegmented OT Networks?
All of the equipment in a facility is interconnected and forms a flat network. There is no compartmentalisation, segmentation, distinction, or prioritising since any device can “speak” to any other device. Malware can easily propagate across assets resulting in potential production shutdown.
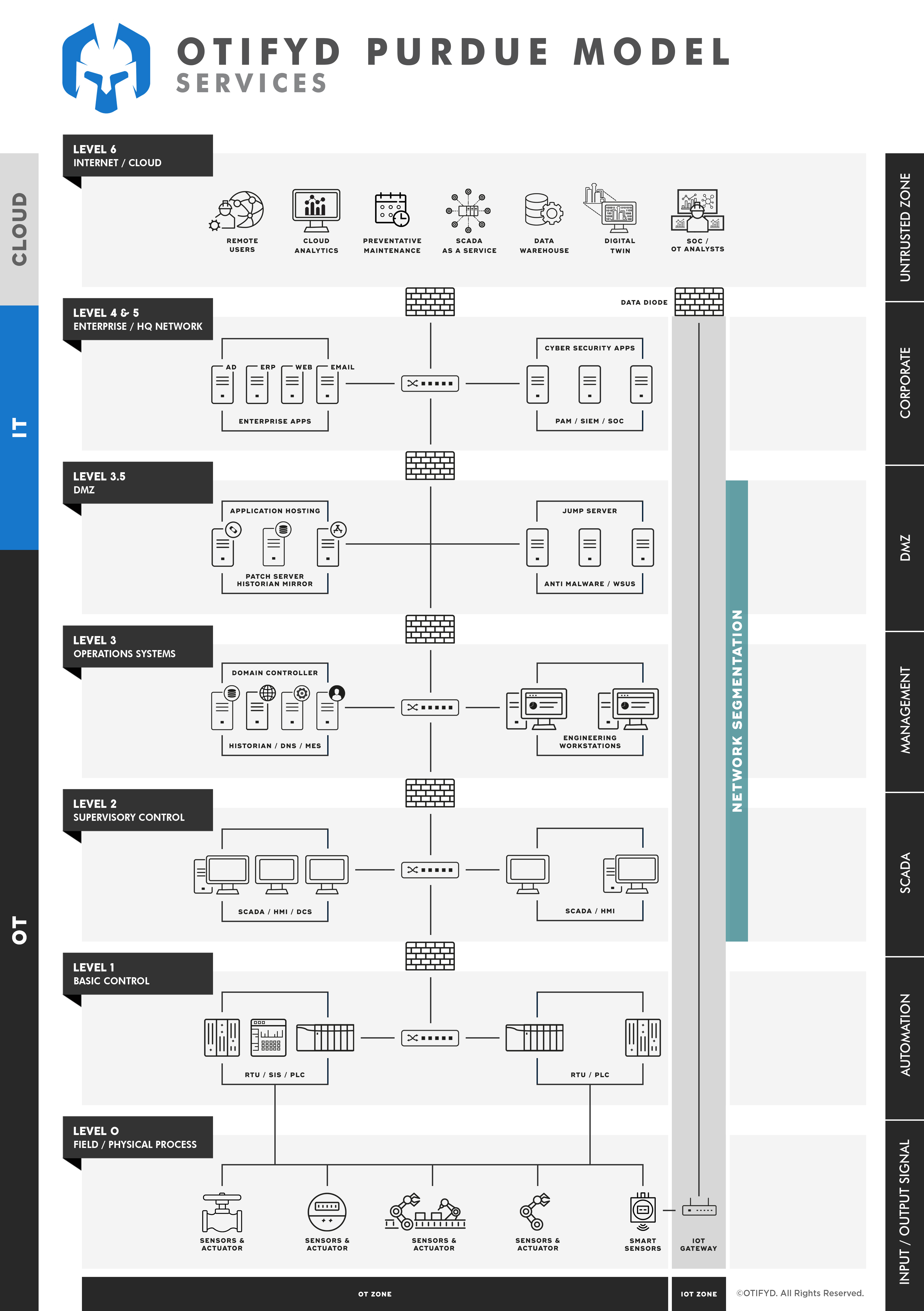
What is the Purdue Enterprise Reference Architecture (PERA) Model?
In a nutshell, the PERA model (an industry framework for segmenting OT networks) promotes process automation, business intelligence adoption, and effective cyber risk mitigation. It effectively aligns OT and IT departments — and strengthens the security posture of an entire organisation. Essentially, the PERA model guides micro-segmentation security policies by grouping assets into zones that share common security requirements.
In the PERA model, the industrial network is divided into 4 zones and 6 levels. A fifth zone, the Safety Zone, is only relevant for nuclear power stations; 95% of installations don’t include this zone in their PERA models.
What is Micro-Segmentation?
Micro-segmentation is a security strategy that involves dividing a network into small segments and applying security controls to each segment to protect against threats that might originate from within the network.
How Does Micro-Segmentation Differ from Traditional Network Segmentation?
Traditional network segmentation typically involves dividing a network into larger subnetworks or zones, while micro-segmentation divides the network into much smaller segments to provide more granular security controls.
What are the Benefits of Micro-Segmentation?
Micro-segmentation can help improve network security by limiting the lateral movement of threats within the network, reducing the attack surface, and enabling more granular access controls.
What are Some Common Challenges Associated with OT Network Segmentation?
Common challenges include the need to balance security with operational requirements, the complexity of managing multiple security policies and controls, and the potential for increased costs and complexity associated with deploying and managing segmented networks.
What are the Best Practices for OT Network Segmentation?
- Identify critical assets: Start by identifying the most critical assets and systems in your OT environment, and prioritize them for segmentation.
- Develop a segmentation plan: Create a detailed plan for how you will segment your OT network, including the specific subnetworks or zones that you will create and the security controls that will be applied to each segment.
- Use a risk-based approach: Take a risk-based approach to network segmentation, focusing on the areas of your network that are most vulnerable to cyberattacks or other security incidents.
- Use network segmentation tools: Use network segmentation tools and technologies, such as firewalls, intrusion prevention systems (IPS), and access control lists (ACL), to segment your network and enforce security policies.
- Apply the principle of least privilege: Apply the principle of least privilege when designing your security policies, limiting access to critical assets and systems only to those who need it.
- Monitor and audit your network: Regularly monitor and audit your network to ensure that your security policies and controls are being properly enforced, and to identify any potential security gaps or vulnerabilities.
- Regularly update your security policies: Review and update your security policies and controls regularly to ensure that they are up-to-date with the latest threats and vulnerabilities.