React Less. Defend More.
Digital Forensics Incident RESPONSE
Peace of mind that an expert team with vast knowledge of incidents will respond to your needs quickly and effectively.
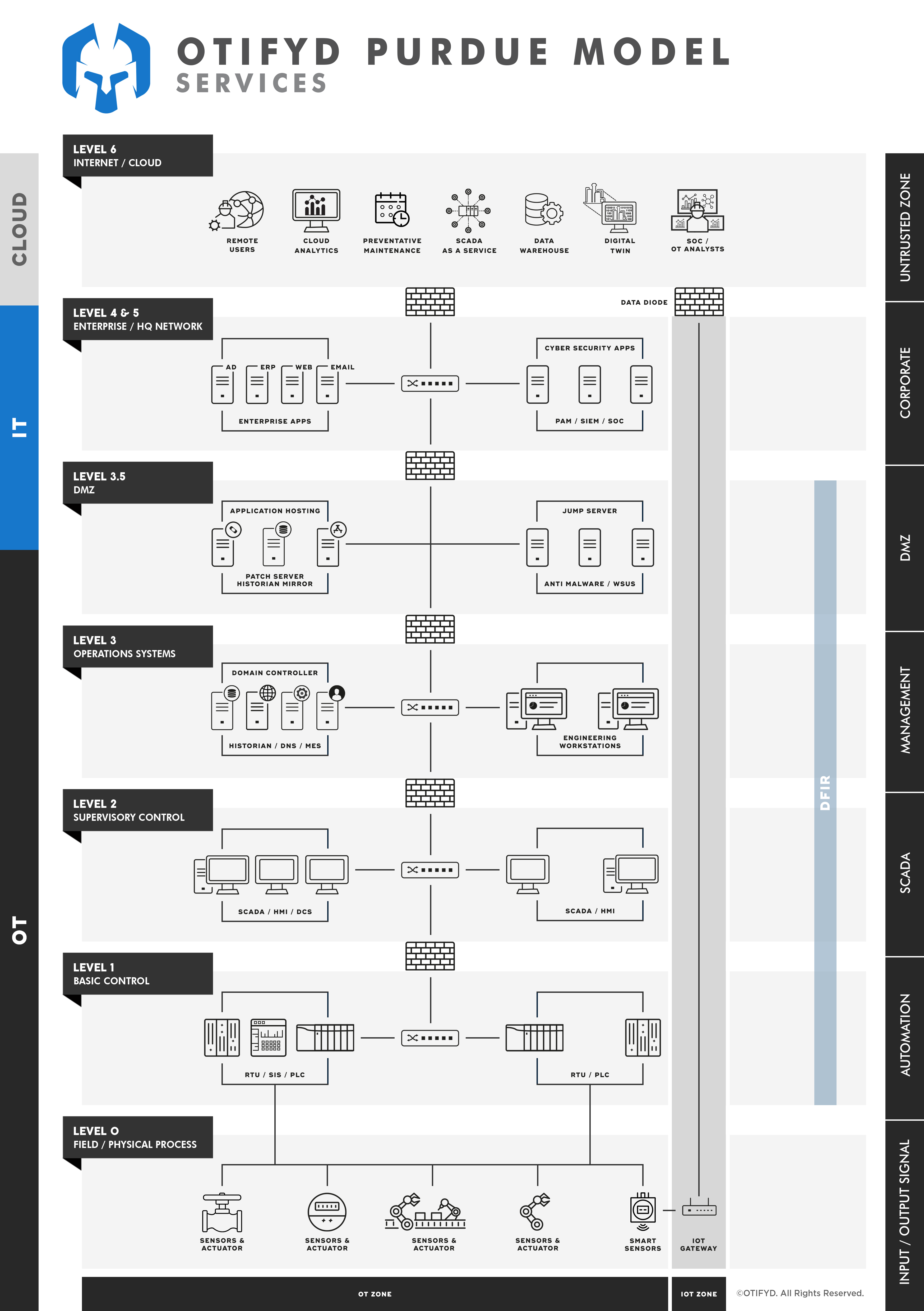
Digital Forensics Incident Response (DFIR) Overview
Digital Forensics and Incident Response (DFIR) is a field within cyber security that focuses on the identification, investigation, and remediation of cyberattacks. DFIR has two main components which are:
- Digital Forensics (DF): A subset of forensic science that examines system data, user activity, and other pieces of digital evidence to determine if an attack is in progress and who may be behind the activity.
- Incident Response (IR): The overarching process that an organisation will follow in order to prepare for, detect, contain, and recover from a cyber incident (i.e. data breach).
Due to the proliferation of endpoints and an escalation of cyber security attacks in general, DFIR has become a central capability within an organisation’s security strategy and threat-hunting capabilities. The shift to the cloud, as well as the acceleration of remote-based work, has further heightened the need for organisations to ensure protection from a wide variety of threats across all devices that are connected to the network.
Though DFIR is traditionally a reactive security function, sophisticated tooling and advanced technology, such as artificial intelligence (AI) and machine learning (ML), have enabled some organisations to leverage DFIR activity to influence and inform preventative measures. In such cases, DFIR can also be considered a component within a proactive security strategy.
Why Establish an OT Digital Forensics Incident Response (DFIR) Capability?
A robust DFIR service provides an agile response for businesses susceptible to threats. It gives you peace of mind that expert teams with vast knowledge of Operational Technology (OT) and cyber incidents will respond to attacks quickly and effectively.
During the aftermath of a cyber security incident, things can be chaotic. The last thing you want to be doing in the heat of the moment is searching for a DFIR vendor that is familiar with OT environments. With ransomware threats escalating in volume and intensity each year, it is inevitable that OT environments will also fall victim to this threat. The consequences of such could result in production delays, deferments or even shutdown.
It’s becoming more common for organisations of all sizes to prepare for OT cyber attacks by seeking out a security partner. In case of compromise, the DFIR vendor takes action to quickly contain the incident and restore the systems. Partnering with a DFIR vendor minimises the detriment and overall impact of attacks on organisations. With a DFIR partner in place, organisations demonstrate to their stakeholders, and in some cases, cyber insurance providers that they are taking proactive steps with their OT Cyber Security Strategy. In turn, they greatly lower their risk profile and can reduce insurance premiums.
In the event an OT cyber incident occurring, it is important to be ready to react swiftly. It is also important to forensically preserve data crucial to the investigation and reporting phase of recovery. Often, a written report summarising the facts around the incident is required by cyber insurance, lawyers, regulatory enforcement agencies, and other stakeholders to understand the compromise and recommendations for strategically moving forward.
Our team goes to work quickly, working with you to identify, contain, eradicate, and recover from the OT cyber incident while communicating with you and you’re stakeholders every step of the way.
Key Benefits of OT Digital Forensics Incident Recovery (DFIR)
- Respond to incidents with speed and precision;
- Follow a consistent process when investigating and evaluating incidents;
- Minimise downtime, data loss or theft, as well as reputational harm, as a result of a cybersecurity attack;
- Strengthen existing security protocols and procedures through a more complete understanding of the threat landscape and existing risks;
- Recover from cyber security events more quickly and with limited disruption to business operations;
- Assist in the prosecution of the threat actor through evidence and documentation.
Deliverables from our OT Digital Forensics Incident Response (DFIR) Service
The deliverables of our Digital Forensics Incident Recovery Service typically include:
Incident Report: A comprehensive report that details the nature and scope of the security incident or breach, including the timeline of events, the systems and data affected, and the extent of the damage.
Evidence Collection and Analysis: A detailed analysis of the digital evidence collected during the investigation, including logs, network traffic, system images, and other data sources.
Chain of Custody Report: A report that documents the collection, handling, and storage of digital evidence to maintain the integrity of the evidence and ensure it is admissible in court.
Root Cause Analysis: An analysis of the underlying causes of the security incident or breach, including the vulnerabilities that were exploited, the methods used by the attackers, and the extent of the damage.
Incident Response Plan: Recommendations for improving the incident response process to prevent similar incidents from occurring in the future.
Legal and Regulatory Compliance Report: A report that assesses the compliance of the organization with relevant legal and regulatory requirements, including data protection laws, industry standards, and contractual obligations.
Recommendations and Remediation Plan: A plan that outlines the steps to be taken to remediate the vulnerabilities identified during the investigation, including patches, configuration changes, and additional security controls.
Overall, the deliverables are designed to provide a comprehensive analysis of the security incident or breach and the steps that should be taken to prevent similar incidents from occurring in the future. This can help organisations improve their security posture and reduce the risk of data loss, theft, and damage.
This service offering is tailored to your organisation’s specific needs. Get in touch to discuss further.
Why Is DFIR Important in Cyber Security?
Together, digital forensics and incident response can provide a deeper understanding of cyber security incidents through a comprehensive process. When cyberattacks occur, experts can use DFIR to gather and investigate massive amounts of data and fill in information gaps.
Typically, DFIR attempts to answer questions such as:
- Who are the attackers?
- How did they gain entry?
- What are the exact steps they took to put systems at risk?
- What data was lost?
- What was the actual damage they caused?
What are the Typical Digital Forensics (DF) Process Steps?
The Digital Forensics (DF) function performs several critical steps in an incident response process. In summary these are typically:
- Identification;
- Preservation;
- Analysis;
- Documentation;
- Reporting.
What are the Typical Incident Response (IR) Process Steps?
Once Digital Forensics (DF) process is complete, DFIR teams can begin the Incident Response (IR) process which typically includes:
- Scoping;
- Investigation;
- Securing;
- Support and Reporting;
- Transformation.
What Value Does DFIR Bring?
Robust DFIR provides an agile response for organisations susceptible to threats. Knowing that expert teams can respond to attacks quickly and effectively gives Organisations peace of mind. When done optimally, DFIR can provide several significant advantages, including the ability to:
- Respond to incidents quickly and accurately;
- Follow an efficient, consistent process for investigating incidents;
- Minimise damage (i.e., data loss, damage to organisational systems, business disruption, compliance risks, and reputational damages);
- Improve the organisation’s understanding of its threat landscape and attack surface.
- Rapidly and fully recover from security incidents, identifying the root cause, and eradicating threats across all organisational systems.
- Enable effective prosecution of attackers by law authorities and provide evidence for legal actions taken by the organisation.
What are Basic DFIR Best Practices?
DFIR best practices include:
- Determining the root cause of all issues;
- Correctly identifying and locating all available evidence and data;
- Offering ongoing support to ensure an organisation’s security posture is stable for the future.
The success of DFIR depends on the rapid and thorough response.
Digital forensics teams must have ample experience and the right DFIR tools and processes to provide a swift, practical response to any issue.