React Less. Defend More.
Incident Response
Ensure you’re equipped with the necessary skills and preparedness to respond to cyber incidents.
Incident Response Overview
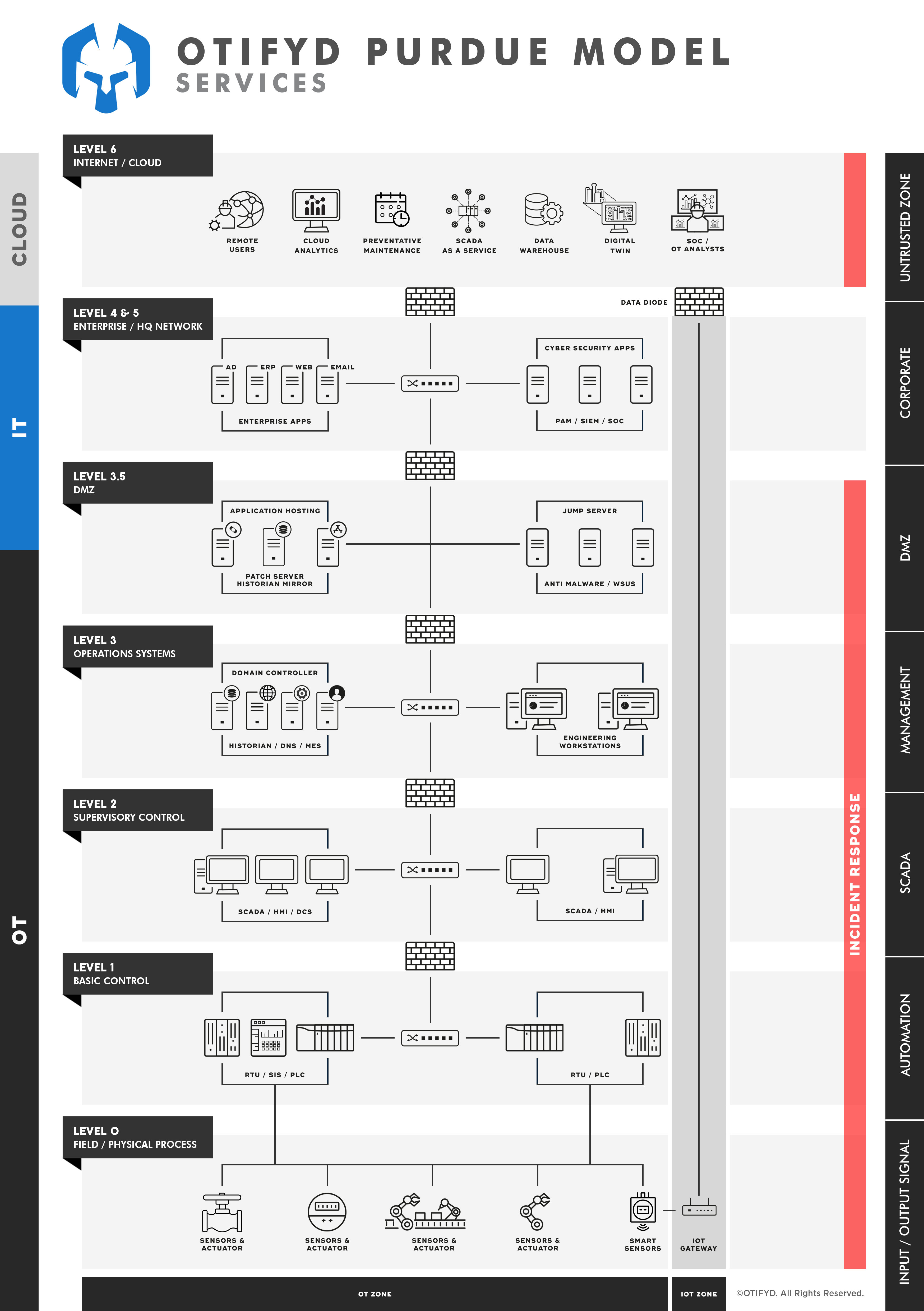
While many organisations are equipped with tools and resources that are capable of resolving common IT cyber incidents, the same cannot always be said for cyber incidents that impact their OT environments. Unfortunately, too many organisations fail to plan for that worst day. Often stating: It can’t happen to us, we are too busy, or our vendors and suppliers will respond if we need them. This reactive-only mindset often results in a far worse outcome should a cyber incident occur.
As digital transformation continues to drive OT/IT convergence, connectivity and technology in these once-separate domains have become more integrated and sophisticated. Although these advancements bring many improvements that drive business advancement and efficiencies, they also bring increased risk exposure from IT across to OT, and vice-versa. With this in mind, having the capability to provide a coordinated and effective response to cyber threats across an entire business becomes increasingly essential.
The above situation has seen the creation of joint IT/OT Cyber Incident Response Plans (CIRP), that aim to ensure an organisation is equipped with the necessary skills and preparedness to respond to cyber threats that arise throughout all their technological environments. This is good progress and a positive step forward for industries, however, the general reality is that this proactive approach is still far and few between with many organisations unprepared to deal with cyber incidents that could impact their live OT environments. The consequences of not having a defined and coordinated incident response could result in prolonged shutdowns, safety and environmental impacts, and reputational damage.
Why Define an OT Incident Response Process?
In simple terms, when it comes to attacks on OT assets, the longer assets are offline the more damage to a company’s financials. Worse still, cyber-physical OT assets in many plants can be an immediate threat to health and human safety, and even result in catastrophic failures that bring harm to those inside and outside the plant, and to the environment. Being able to quickly detect, respond, and recover from an attack is a critical element of OT cyber security risk management.
Incident response is often one of the last areas tackled by OT cyber security programs, but in reality, it should be one of the first. By taking an outcome-focused cyber security approach, organisations gain an understanding of real-world scenarios and what they actually mean to their business operations if they were, for example, hit by ransomware. Understanding this in turn provides the correct steer for effective remedial controls deployed by a security program as opposed to implementing a set of controls based on inapplicable threat scenarios, that offer little risk reduction, and are simply there for compliance reasons.
The key to outcome-focused cyber is the process of risk analysis. For example, what are the odds that a malicious actor can get to one OT asset that performs a critical process safeguarding function? It might be low. Add 50 people with electronic access to that same OT asset and the risk goes up significantly. Organisations must assess the cost of mitigating the risk against the cost and impact of the outcome if not responding to a vulnerability. This is a fundamental concept to develop effective OT Incident Response capabilities.
Key Benefits of an OT Incident Response Process
- Quicker Mitigation: Having defined pre-planned steps will help an organisation to minimise its response time. A delayed response means that the malicious actor has more time, potentially resulting in increased impact.
- Organised Approach: By proactively implementing an OT Incident Response plan, you have a clear, methodical plan of action to rely on in critical times.
- Strengthens Overall Security: In the process of creating the OT Incident Response plan, current measures, OT assets, weaknesses, and vulnerabilities are all analysed. In addition, these factors and their potential impact on various real-world security scenarios are considered. Thus, organisations have a better understanding of their overall security.
- Builds Trust: Customers, partner companies and other stakeholders will certainly prefer that an organisation have an effective OT Incident Response plan in place. Proactive measures like these showcase that an organisation has made the effort to consider and reduce its risk exposure.
- Compliance: Increasing regulations worldwide mean that organisations have to undertake measures to ensure compliance. Critical infrastructure sectors such as energy generation, water and waste utilities face stringent rules to ensure that cyber risk management is being undertaken.
What are the 7 Phases of Incident Response
In operational technology (OT) security, the ability to effectively respond to and mitigate security incidents is paramount to safeguarding critical infrastructure and industrial processes. An incident response plan outlines the steps and procedures necessary to detect, contain, and recover from security breaches or anomalies within OT environments. By following a structured approach, organizations can minimize the impact of incidents, maintain operational continuity, and strengthen their overall security posture.
Seven Phases of Incident Response in OT Security:
Preparation: Establishing proactive measures and resources to prepare for potential security incidents, including forming an incident response team, defining roles and responsibilities, and implementing necessary security controls.
Identification: Detecting and identifying signs of a security incident within the OT environment, such as unusual network activity or system anomalies, through continuous monitoring and analysis.
Containment: Taking immediate actions to limit the scope and impact of the incident by isolating affected systems or segments of the network to prevent further compromise.
Eradication: Eliminating the root cause of the incident by removing malicious entities, patching vulnerabilities, and restoring affected systems to a known good state.
Recovery: Restoring affected systems, services, and data to normal operation through backups, system reconfiguration, and implementing additional security measures to prevent recurrence.
Lessons Learned: Conducting a thorough analysis of the incident response process to identify areas for improvement, document lessons learned, and enhance future incident response capabilities.
Review and Continuous Improvement: Reviewing and updating incident response plans, procedures, and training based on the insights gained from past incidents and changes in the threat landscape, ensuring ongoing readiness to address emerging security challenges in OT environments.
By adhering to these seven phases, organizations can effectively respond to and mitigate security incidents in OT environments, enhancing resilience and protecting critical assets and operations.
Deliverables from our OT Incident Response Service
As part of this service offering, we typically conduct the following:
- Review existing incident response policies, procedures, network architectures, system configurations and asset inventories;
- Interview key stakeholders and personnel and clarify roles and responsibilities;
- Prepare staff responsible for OT security with tailored real-world incident scenarios, simulations and exercises to enact response measures swiftly;
- Provide remote support, next steps and reporting guidance in the case of an immediate incident.
What are the Fundamental 6 Steps of Incident Response?
In some references, there are seven phases of incident response which we have already covered. Some other references have listed the following 6 phases:
Step #1: Preparation.
Step #2: Identification.
Step #3: Containment.
Step #4: Eradication.
Step #5: Recovery.
Step #6: Lessons Learned.
What is an Incident Response Plan?
An incident response plan is a set of actions and procedures that outlines an organisation’s response to security incidents. An incident response plan is designed to facilitate timely and effective incident mitigation by making it clear what steps should be taken and by whom.
Why is it Important to Have an Incident Response Plan in Place?
For a cyber risk management strategy to be effective, it should include a comprehensive incident response strategy to help businesses:
- Know how to handle cybersecurity incidents,
- Minimise the incidents impact when they occur, and
- Strengthen their defences against future incidents.
What Do I Need to Consider When Developing an Incident Response Plan?
Although incident response planning may seem like a daunting task, there are a couple of key considerations you should keep in mind to facilitate drafting (or updating) your incident response plan.
- Document your incident response strategy in writing.
- Test your incident response plan.
- Review your incident response plan regularly.
- Set up an incident response team.
What Does an Incident Response Team Do?
The goal of the Incident Response Team is to minimise the impact of incidents on the business. This includes minimising the time it takes to resolve an incident, the financial impact of an incident, and the reputation damage that can occur as a result of an incident.
What Does an Incident Response Plan Typically Include?
- The organisation’s incident response strategy and how it supports business objectives;
- Roles and responsibilities involved in incident response;
- Procedures for each phase of the incident response process;
- Communication procedures within the incident response team, with the rest of the organisation, and external stakeholders;
- How to learn from previous incidents to improve the organisation’s security posture.